Browser-based timerless speculative execution attacks are a security threat that exploits vulnerabilities in web browsers and CPUs.
These attacks do not rely on timing measurements, making them harder to detect.

Their sophistication varies, but they can be very advanced, allowing attackers to steal sensitive data or compromise system security by exploiting speculative execution mechanisms in modern CPUs.
The following cybersecurity researchers from their respective organizations have recently uncovered a new attack, dubbed “iLeakage,” that enables hackers to attack Apple Safari for email and password theft:-
- Jason Kim from the Georgia Institute of Technology
- Stephan van Schaik from the University of Michigan
- Daniel Genkin from the Georgia Institute of Technology
- Yuval Yarom from the Ruhr University Bochum
iLeakage Analysis
iLeakage is a JavaScript-based transient-execution attack that enables attackers to retrieve secret Safari data while overcoming Apple-specific challenges and standard countermeasures.
The first speculative execution attack on Apple Silicon CPUs and Safari, known as iLeakage, successfully extracted data from a number of iOS browsers, including:-
Not only that, even through a timerless Spectre attack, it also manages to evade the typical side-channel defenses.
Analysts defeated Apple’s side-channel protections, including low-resolution timers and compressed 35-bit addressing, to bypass Safari’s site isolation policy and leak sensitive data through speculative type confusion.
Watch in Action
The attack uses the following two programming languages to retrieve Gmail messages on an iPad in Safari when the victim interacts with the page customized by the attacker:-
Besides this, from a LastPass-managed account, cybersecurity researchers managed to steal an auto-filled Instagram password in Safari by applying the same method.
They also demonstrated how “iLeakage” functions with Chrome for iOS, gaining access to YouTube watch history because of Apple’s ban against third-party browsers.
Apple’s Arm-based M1 CPUs have seen side-channel attacks, like cache capacity, Spectre v1, and more recently, PACMAN, exploiting various vulnerabilities.
iLeakage proves the continued relevance and exploitability of the Spectre attack, revealing how an attacker can recover sensitive data from popular sites, including Gmail passwords, through speculative execution in Safari.
Impacted Devices
All the Apple devices from 2020 with A-series and M-series ARM processors are affected by “iLeakage,” leaving no detectable traces but requiring advanced browser-based side-channel attack knowledge.
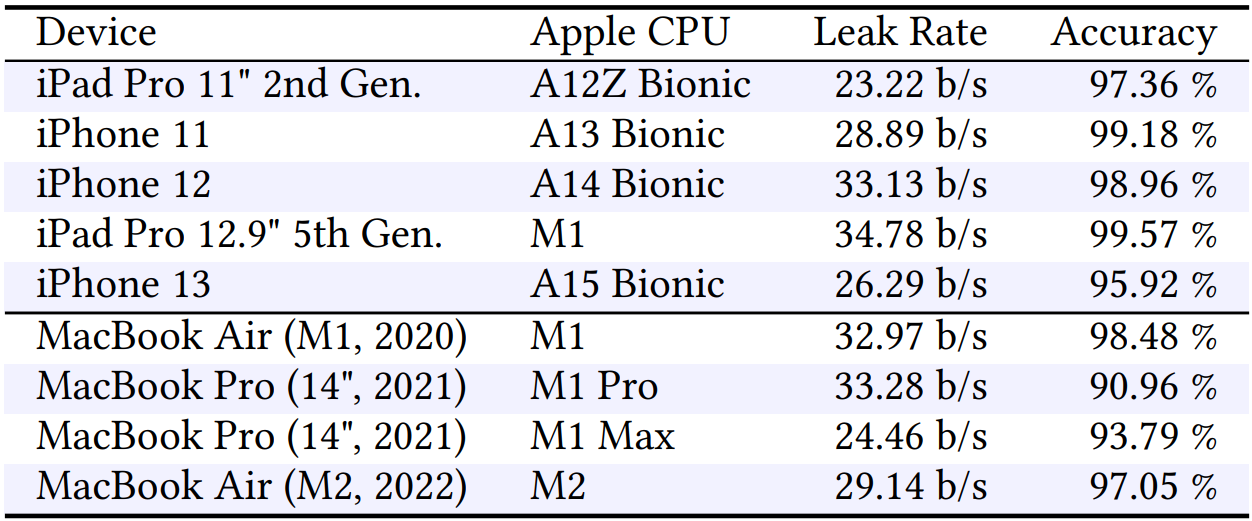
Countermeasures
Here below, we have mentioned all the countermeasures offered by the cybersecurity researchers:-
- Preventing Consolidation via Site Isolation.
- Preventing Speculation Past Type Checks.
- Removing Poisoning Optimizations.
- Measuring COI Adoption.
- Make sure to analyze all the results properly.
- Have constant checks on leak rate.
- Inability to Cross Address Spaces.
- Memory Safety Under Speculation.
Protect yourself from vulnerabilities using Patch Manager Plus to patch over 850 third-party applications quickly. Try a free trial to ensure 100% security.
Read the full article here

