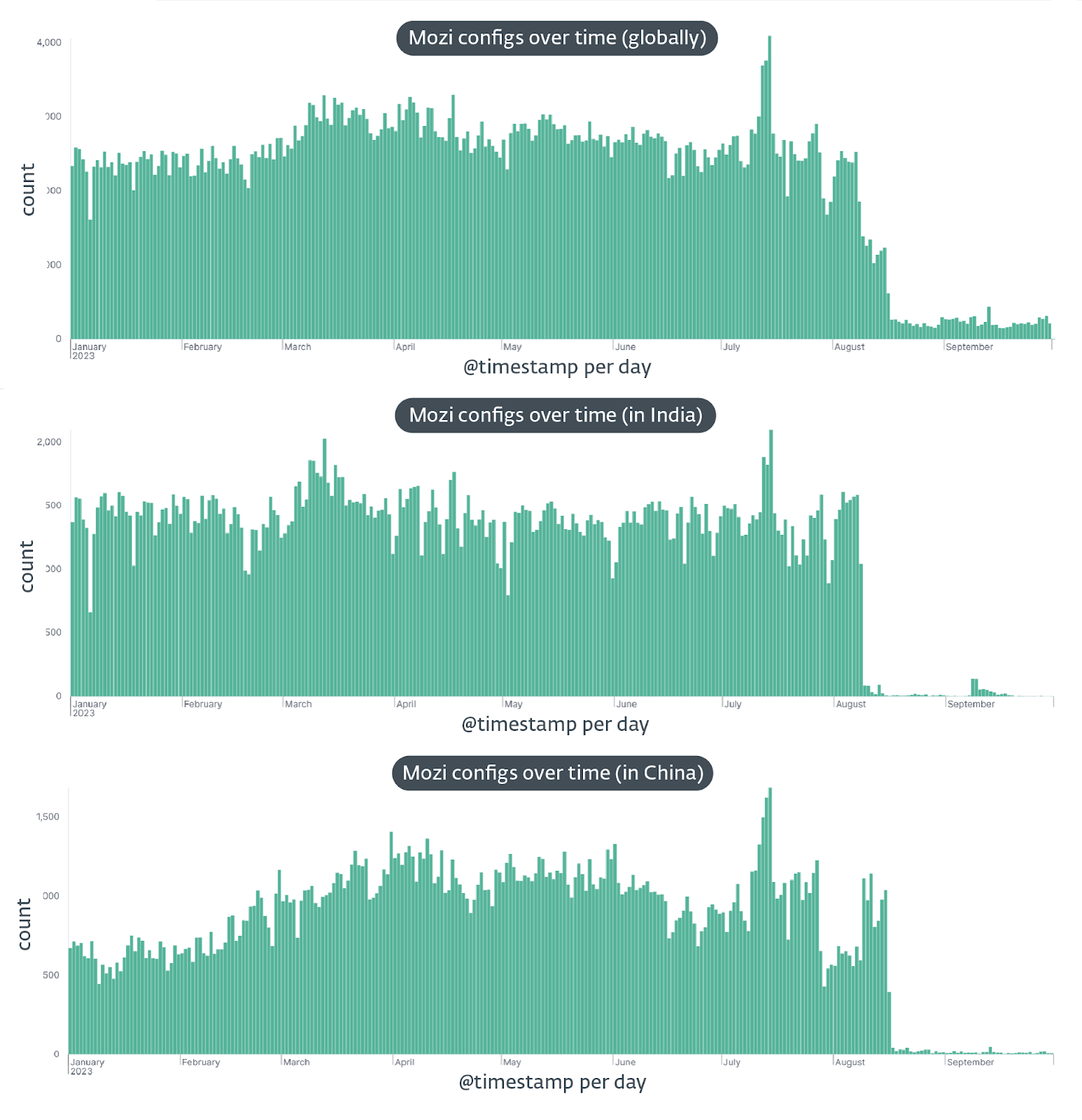
As of August 2023, one of the most notorious IoT Botnets called “Mozi” vanished from their activities. Mozi Botnet had been exploiting hundreds of thousands of IoT devices.
In the year 2023, a strange phenomenon occurred where a certain type of object began to disappear without explanation. The disappearance started in India on August 8th and then spread to China on August 16th. The sudden vanishing of these objects left many people puzzled and concerned.

Analyzing further, a Kill Switch was discovered with a user datagram protocol (UDP) message. The person responsible for this takedown used the kill switch eight times, instructing the bot to download and install an update via HTTP.
Kill Switch Functionalities
Researching further, the kill switch demonstrated several functionalities such as the parent process, disabling sshd and dropbear services, replacing the original Mozi file with itself, executing configuration commands, disabling access to various ports, and establishing the same foothold as the replaced original Mozi file.
Ensure your Cyber Resiliance with the recent wave of cyber-attacks targeting the financial services sector. Almost 60% respondents not confident to recover fully from a cyber attack.
The kill switch showed a strong connection between the botnet’s source code and most recently used binaries. Additionally, it also shows the use of correct private keys to sign the control payload.
Who Initiated the Kill Switch?
There are no confirmed reports on who took down Mozi Botnet. However, some hypotheses suggest that the kill switch might have been initiated by the Mozi botnet creators or Chinese law enforcement forcing the cooperation of the creators, reads the ESET report.
Nevertheless, the fall of one of the most notorious botnets provides a lot of information about the creation, operation, and termination of botnets in the wild.
Indicators of Compromise
Files
| SHA-1 | Filename | Detection | Description |
| 758BA1AB22DD37F0F9D6FD09419BFEF44F810345 | mozi.m | Linux/Mozi.A | Original Mozi bot. |
| 9DEF707F156DD4B0147FF3F5D1065AA7D9F058AA | ud.7 | Linux/Mozi.C | Mozi bot kill switch. |
Network
| IP | Domain | Hosting provider | First seen | Details |
| 157.119.75[.]16 | N/A | AS135373 EFLYPRO-AS-AP EFLY NETWORK LIMITED | 2023-09-20 | Kill switch hosting server |
Protect yourself from vulnerabilities using Patch Manager Plus to patch over 850 third-party applications quickly. Try a free trial to ensure 100% security.
Read the full article here

