Microsoft Access is a relational database management system developed by Microsoft that allows users to store and manage data.
Hackers target it because vulnerabilities in Access can be exploited to gain unauthorized access to databases, compromising sensitive information.

Cybersecurity researchers at Checkpoint recently discovered that hackers are actively abusing or exploiting the Microsoft Access feature to steal Windows users’ NTLM tokens.
Hackers Exploit Microsoft Access
Microsoft’s 1993 NTLM is an outdated, challenge-response authentication protocol, and the users derive responses from a stored NTLM hash, presenting a security concern.
Here below, we have mentioned all the attacks against NTLM that are popular:-
Mitigations against NTLM attacks existed in protocols like Kerberos before NTLM’s introduction.
Blocking outbound traffic on NTLM ports (139 and 445) is a stop-gap solution, but a new method using MS-Access “Access Link Tables” can bypass this defense, targeting internal users directly.
Linked tables in MS Access allow efficient connections to external databases like remote SQL servers. Activating the feature involves clicking ‘ODBC Database’ under ‘External Data.’
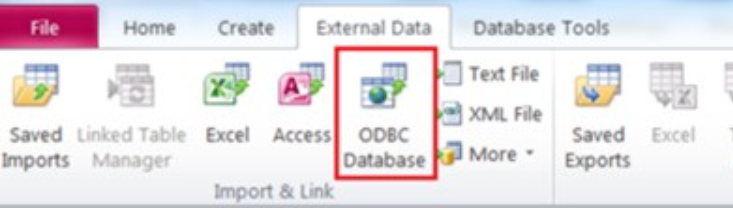
This applies to all Office versions, with an alternative option for a one-time download of remote tables treated as local subsequently.
Selecting ‘SQL Server’ as the ODBC source, the user then chooses an authentication method and may leave the port as default or pick a strange one, like port 80.
StorageGuard scans, detects, and fixes security misconfigurations and vulnerabilities across hundreds of storage and backup devices.
An SQL server can listen on port 80, though it’s unusual. The linked table appears in the client’s list if authentication is successful and reads the CheckPoint report.
By clicking it, a connection to the remote database is established, and the user’s Windows credentials are used to authenticate with the SQL server.
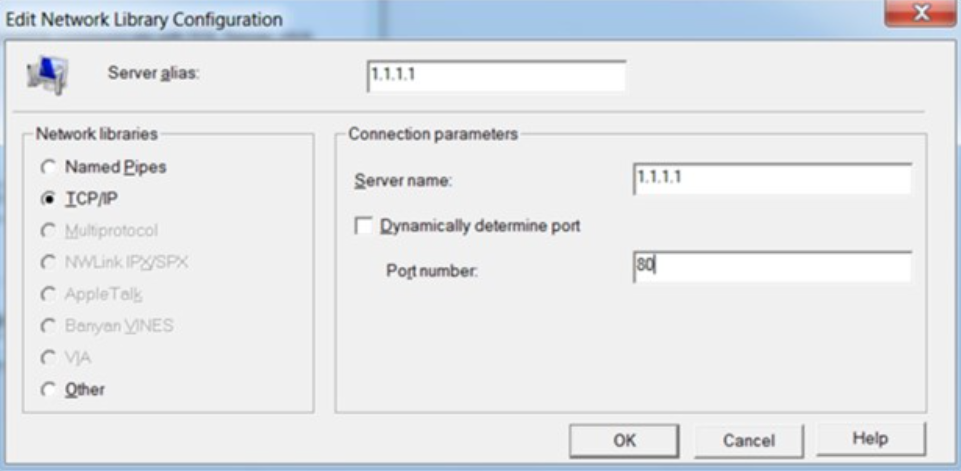
To weaponize, an attacker sets up a server on port 80, puts its IP in the server alias field, and sends the file to the victim.
The attacker-controlled server can execute an NTLM relay attack if the victim opens the file and clicks the table. While getting the victim to open and click is challenging, MS-Access macros could automate it.
Security features like protected view don’t apply to simple MS-Access macros, potentially exposing users to risks.
Microsoft Access is an OLE linking server on Windows, enabling other apps to request object handling. It functions like embedding an image in MS Word, where MS Paint processes it for display.
Similarly, a .accdb file in MS Word acts as an auto-downloadable OLE object, handled by MS Access via port 80/tcp.
Mitigations
Here below, we have mentioned all the mitigations recommended by the researchers:-
- Opt for a “content-aware” firewall—it goes beyond destination port checks, incorporating packet inspection for enhanced security.
- Disable MS-Access macros or uninstall them if unnecessary for your Office suite.
- Make sure to not open the attachments received from unknown or suspicious sources.
- Always use a robust security solution for enhanced security.
Patch Manager Plus, the one-stop solution for automated updates of over 850 third-party applications: Try Free Trial.
Read the full article here

