State-sponsored hackers or threat actors and their cyber operations are evolving at an alarming pace, leveraging advanced techniques and constantly adapting to exploit emerging vulnerabilities.
The intersection of technology and geopolitics fuels a relentless race, driving these actors to enhance their capabilities swiftly and maintain a persistent threat in the digital landscape.

Cybersecurity researchers at Insik Group reported that Chinese hackers are actively expanding their capabilities to exploit Zero-Day vulnerabilities.
In the last five years, Chinese state-sponsored cyber ops matured, targeting known and zero-day vulnerabilities in public security. Emphasizing operational security, they’ve become harder to detect.
Chinese Hackers and Zero-Day Vulnerabilities
Internal shifts like military restructuring and external factors like Western reporting shaped Chinese cyber ops. This evolution poses challenges for defense against these threats.
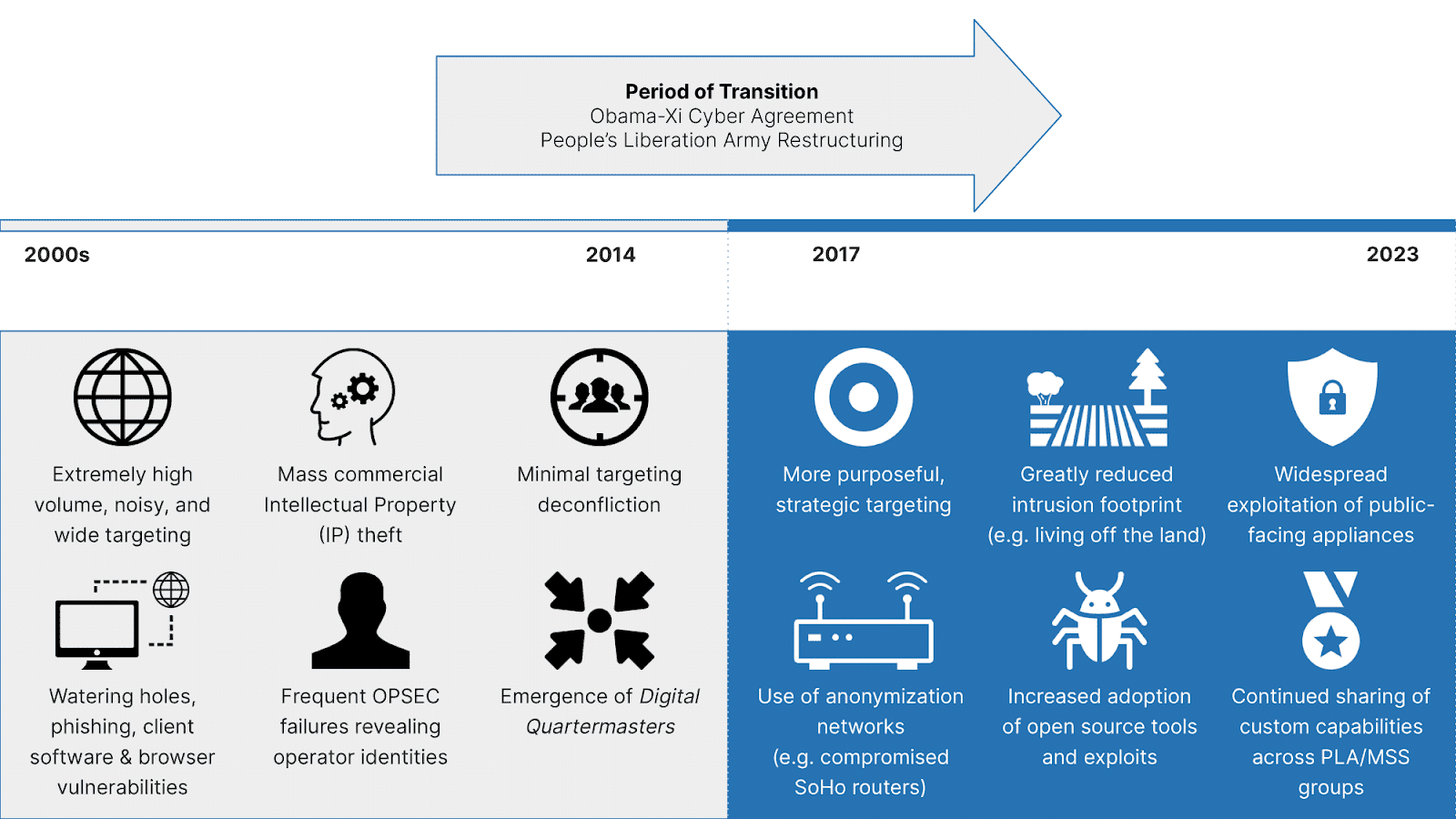
Chinese cyber economic espionage now targets specific goals, like the Belt and Road Initiative, shifting from broad IP theft to strategic objectives.
Due to this significant shift, the government and corporate risks rise, which has a serious impact on two critical areas:-
- Negotiations
- Competitiveness
Zero-day vulnerabilities give threat actors an edge as they are undisclosed and lack available patches, allowing for stealthy and effective cyber attacks.
StorageGuard scans, detects, and fixes security misconfigurations and vulnerabilities across hundreds of storage and backup devices.
Exploiting these vulnerabilities gives attackers an opportunity before security measures are implemented.
The rapid cyber-growth of China is a strong indication that taking advantage of public appliance zero-day vulnerabilities works well for gaining access to worldwide targets.
It’s completely obvious to expect a similar emphasis when enterprises move to the cloud.
Strategic reconnaissance and information collection will probably increase due to China’s force projection in the South China Sea and US relationships or alliances.
Attacking critical infrastructure isn’t a sign of immediate conflict but a preparation for future possibilities.
Moreover, China is positioned to dominate worldwide cyber espionage and information warfare due to its significant investments in cyber operations.
Secures your storage & backup systems With StorageGuard – Watch a 40-second Video Tour.
Read the full article here

