Threat actors target wireless chargers for multiple malicious activities, such as implanting malware or conducting power-related attacks.
The rising popularity of wireless charging brings convenience. Still, recent research by Zihao Zhan, Yirui Yang, Haoqi Shan, Hanqiu Wang, Yier Jin, and Shuo Wang from the University of Florida and CertiK uncovered vulnerabilities.
They discovered that electromagnetic interference can manipulate the chargers, which poses security risks.
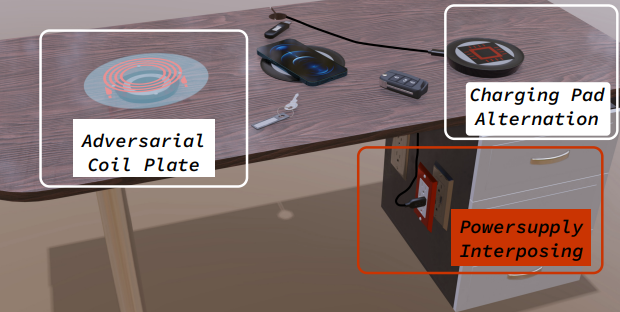
Researchers discovered VoltSchemer, which enables the execution of innovative attacks on wireless chargers by tweaking power supply voltage without any modification.
Threats include voice assistant manipulation, device damage, and Qi-standard bypass.
VoltSchemer Wireless Charger Attack
VoltSchemer attacks exploit newly found wireless charger vulnerabilities that allow complete control via intentional electromagnetic interference (IEMI).
By manipulating the magnetic fields, the threat actors gain control of voice assistants and initiate harmful power transfers.
More than 300,000 analysts use ANY.RUN is a malware analysis sandbox worldwide. Join the community to conduct in-depth investigations into the top threats and collect detailed reports on their behavior..
However, cybersecurity analysts identified the widespread vulnerability and risks after testing the same on 9 top-selling chargers.
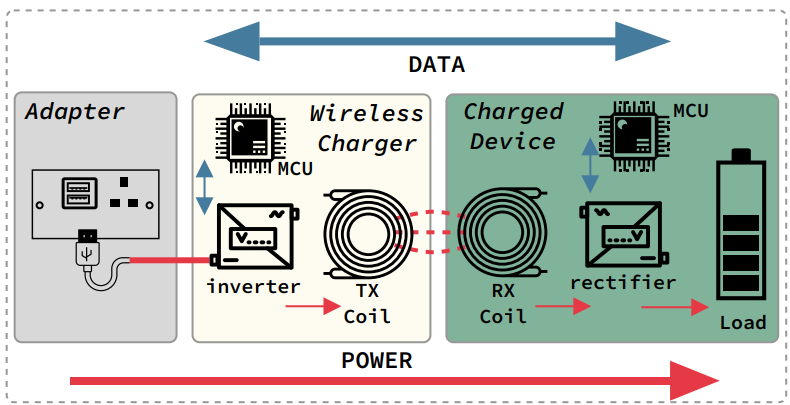
Wireless charging uses near-field magnetic coupling and transfers power without direct connections, which prevents data access by threat actors.
The Qi standards ensure safety and device protection. Its benefits, like enhanced security, which simplified the charging and reduced mess, drive its rapid market growth.
Wireless chargers are now everywhere, as they have already been deployed widely in airports, restaurants, and more.
Wireless charging differs significantly from wired charging by eliminating physical connections, which helps reduce the attack surfaces.
The Qi standards ensure robust communication and safety by employing the following techniques for data integrity:-
- Amplitude-Shift Keying (ASK)
- Biphase Mark Coding (BMC)
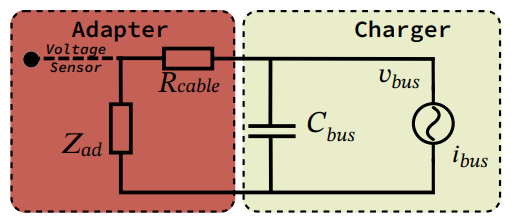
According to the report, real-world power adapters vary from ideal performance due to workload behaviors affecting the switching regulator’s limitations.
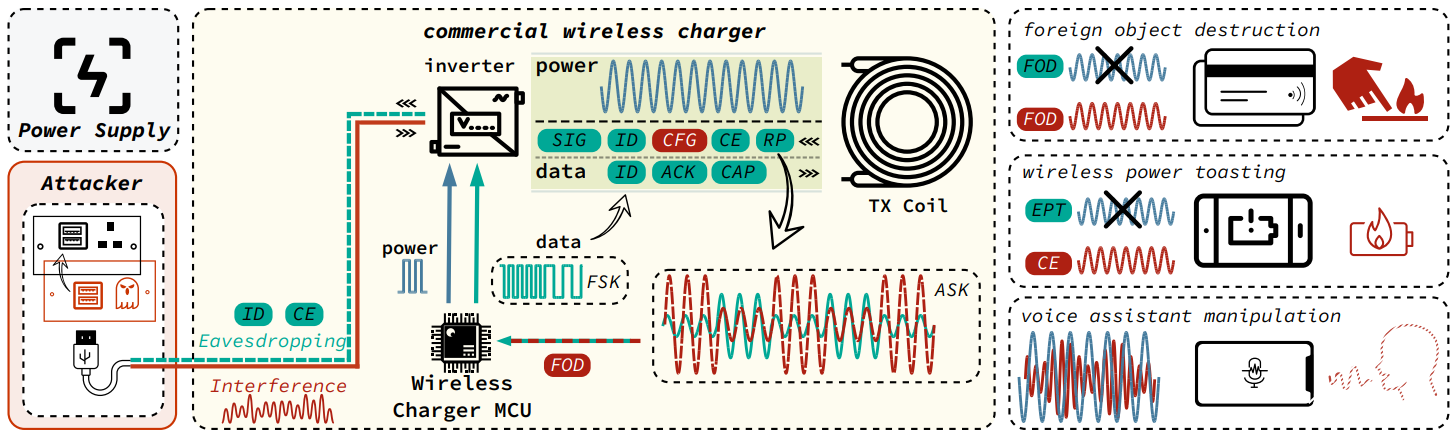
Attack Vectors
Here below, we have mentioned the attack vectors:-
- Voice Injection
- Qi Message Injection
- Qi Message Eavesdropping
Researchers assess system resilience by testing the voice command injection on iPhone SE and Pixel 3 XL across various chargers.
While the success depends on factors like system electrical characteristics, voice signal features, and assistant algorithms.
Finding the minimum interference depth for efficient and stealthy attacks, observations show charging interruptions increase beyond 0.35, which shows the accuracy in threshold measurements.
Testing wireless power-toasting attacks on Samsung Galaxy S8 shows that the smartphone protection measures are compromised.
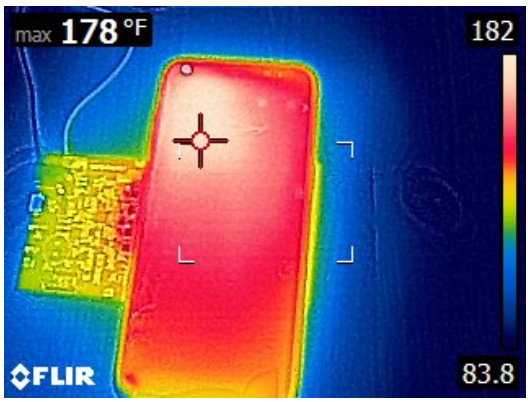
Voltage interference corrupts the power-halting attempts by misleading the charger and maintaining dangerously high temperatures despite protective measures, stabilizing at 178°F.
To counter the attacks, researchers recommended integrating noise suppression components like extra DC/DC converters, which is practical.
Testing on a Renesas P9242 charger shows significant noise reduction across frequencies, with a minimum of 15 dB. However, this solution increases cost, size, weight, failure rate, power consumption, and thermal stress.
You can block malware, including Trojans, ransomware, spyware, rootkits, worms, and zero-day exploits, with Perimeter81 malware protection. All are extremely harmful, can wreak havoc, and damage your network.
Read the full article here

