Hackers seek to exploit WhatsApp flaws to gain unauthorized access to user data, messages, and sensitive information.
Exploiting these flaws allows threat actors to compromise user privacy, conduct espionage, and engage in malicious activities.
Recently, a cybersecurity analyst, Tal Be’ery, discovered a WhatsApp privacy flaw that devices information on any other user.
Compounding the problem are zero-day vulnerabilities like the MOVEit SQLi, Zimbra XSS, and 300+ such vulnerabilities that get discovered each month. Delays in fixing these vulnerabilities lead to compliance issues, these delay can be minimized with a unique feature on AppTrana that helps you to get “Zero vulnerability report” within 72 hours.
WhatsApp Privacy Flaw
For message confidentiality, WhatsApp, with over 5 billion downloads and 2.4 billion active users, relies on the End-to-End Encryption (E2EE) protocol.
WhatsApp introduced E2EE in 2016, where each app generates a unique crypto key for secure messaging. This key is tied to the device that changes during reinstallation to notify other users that a device switch has occurred.
WhatsApp prevents information leaks during app reinstallation by maintaining the same key if restored from backup. In 2021, with multi-device architecture, companion devices generate their keys known as ‘Identity keys,’ valid until the app is uninstalled.
The sender creates session keys for each device based on its Identity Key when sending a message to a multi-device recipient.
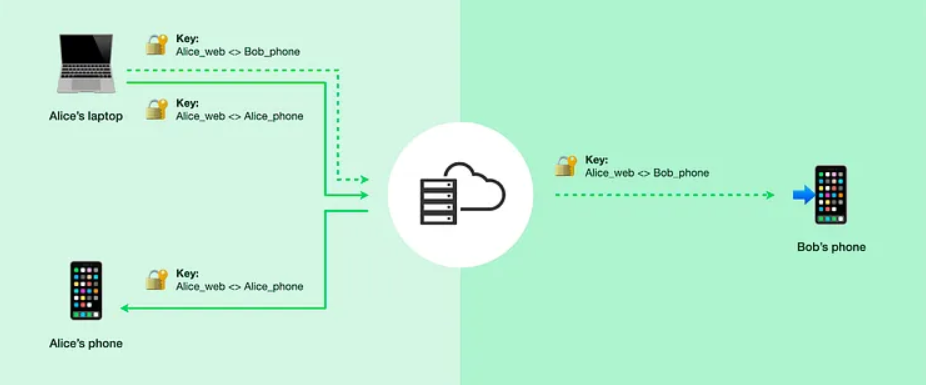
Using client-fanout, each message is encrypted for all devices, which requires the sender to know and be aware of all receiver devices by including the distinction between primary and companion devices.
Threat actors can access WhatsApp users’ device info by exploiting the WhatsApp web client that stores identity keys in the browser’s local storage.
Examining the ‘Signal-storage.identity-store’ table reveals user contacts and their keys, which distinguishes the primary devices with a ‘.0’ suffix and companion devices with a ‘:<n>.0’ suffix
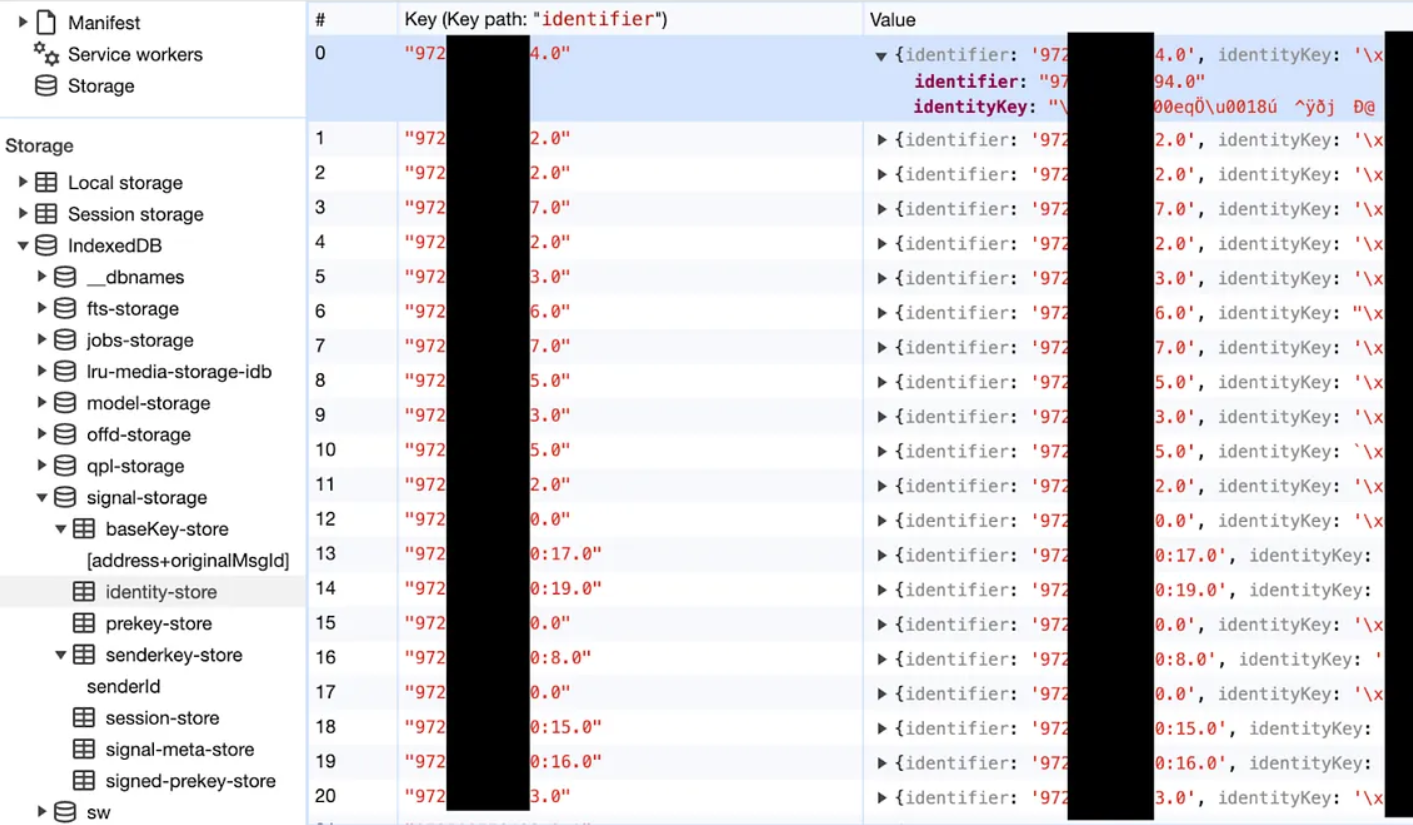
Threat actors using these methods can passively query any WhatsApp user’s device info by monitoring companion devices and identity changes.
This allows them to choose the ‘path of least resistance’ for attacks to target specific devices and exploit changes in user platforms. Even non-sophisticated attackers can leverage this information to access WhatsApp content.
However, the researcher notified the Meta about this bug and received the following response:-
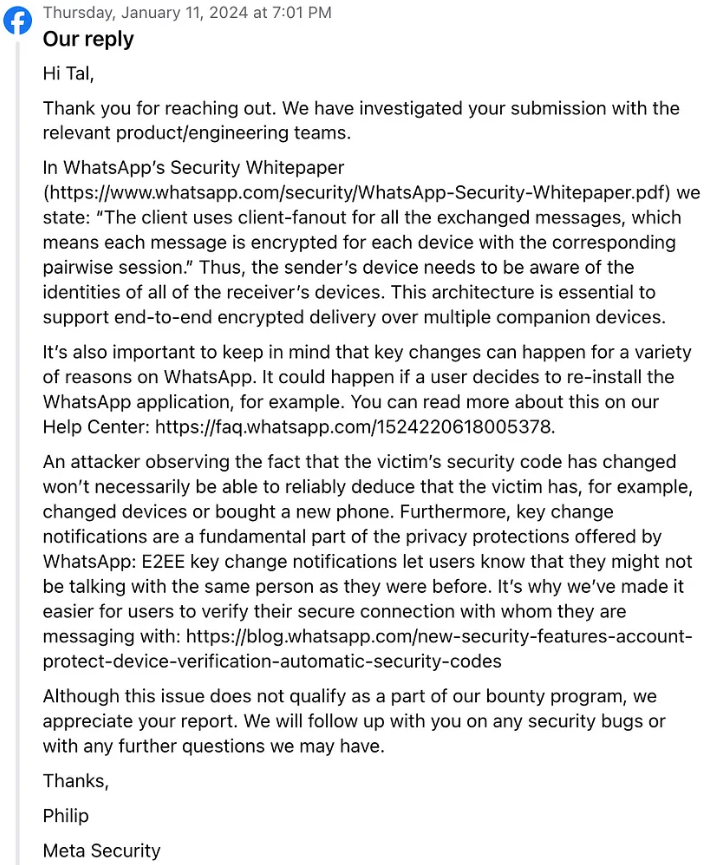
While removing the table is a partial solution, as the core issue lies in fixing the E2EE protocol for true privacy. Introducing a security control to limit the exposure of identity keys to contacts would significantly mitigate this privacy leak without addressing signs.
Try Kelltron’s cost-effective penetration testing services to evaluate digital systems security. Free demo available.
Read the full article here

