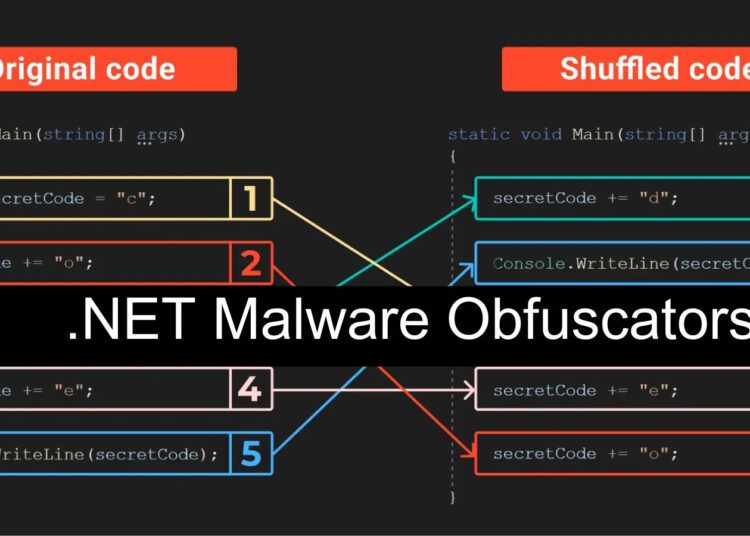
The .NET malware obfuscators are tools used to obfuscate the source code of .NET applications, making it challenging for reverse engineers to understand and analyze the code.
They rename variables, alter code structures, and add misleading instructions to hide detection and analysis by enhancing the malware’s strength against security measures.
It’s rare to find clean malware, as they are often altered to prevent analysis with obfuscators. Some mutate machine code (C/Asm/Rust), while others modify .NET IL code.
According to ANY.RUN Technical write-up Part 1, to comprehend obfuscators, we must think like their creators. To defend correctly, you must understand the offensive, like the red/blue team in cybersecurity.
ANY.RUN is a developer of a cloud malware sandbox that handles the heavy lifting of malware analysis for SOC and DFIR teams, as well as Threat Intelligence Feeds and Threat Intelligence Lookup. Every day, 300,000 professionals use our platform to investigate incidents and streamline threat analysis.
Technical Analysis
ANY.RUN researchers built a simple obfuscator in which the one function below the image, “ProtectMe,” which outputs “No_On3_Can_Find_My_S3cr37_Pass,” contains a few lines of code and one variable.
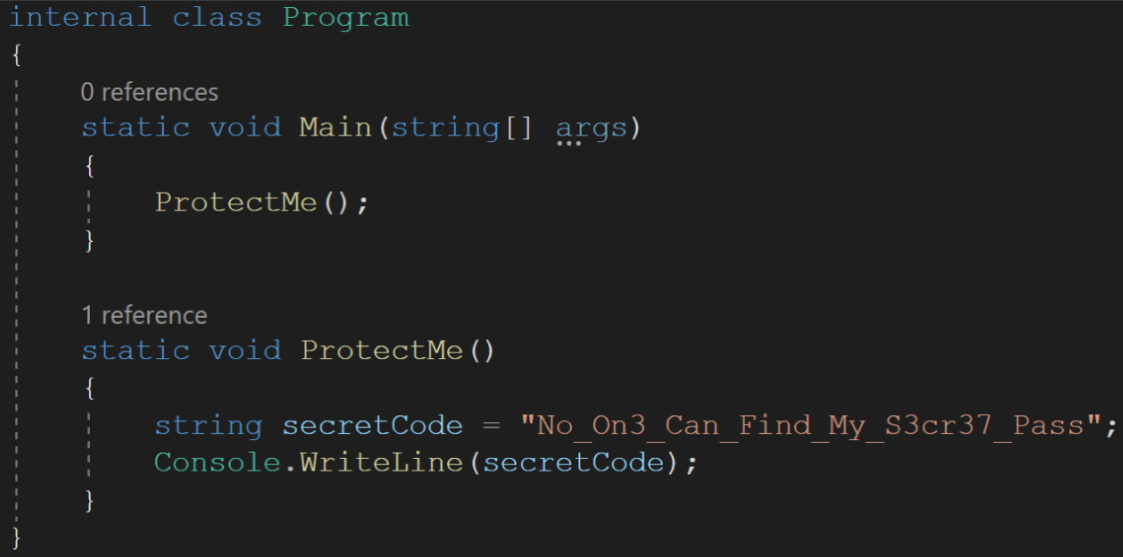
In the .NET debugger “DnSpy” the decompiled code looks like the following:
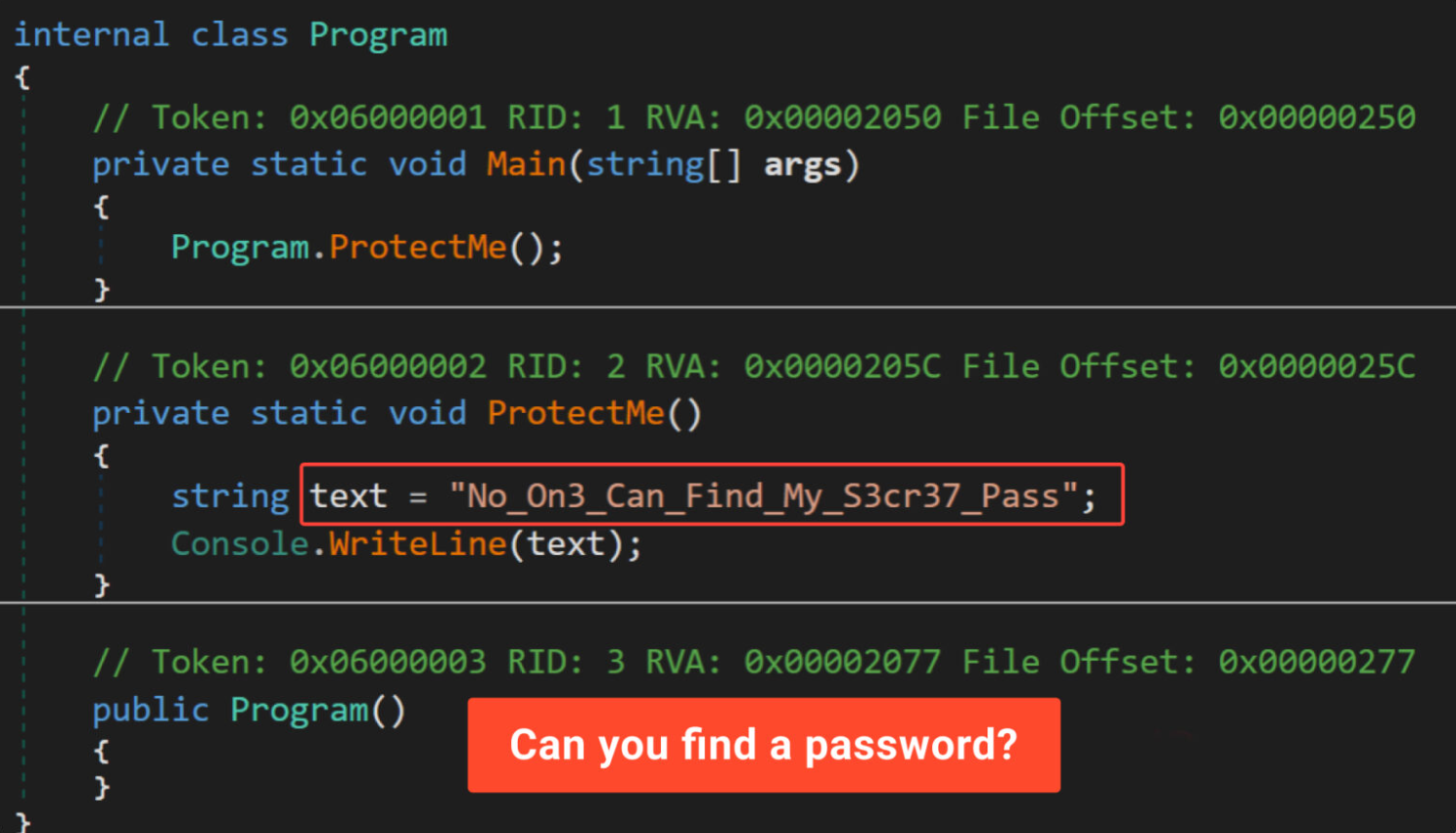
Opening the built-in software in the relevant tool shows that anyone may quickly and readily discover the password.
To protect the password. following strategies are recommended:
- proxy functions
- character breakdown
- numeric conversion
- heavy math
- CFG obfuscation
The proxy functions put each static string in its own function with an absurd name that gives better control over these individual functions.
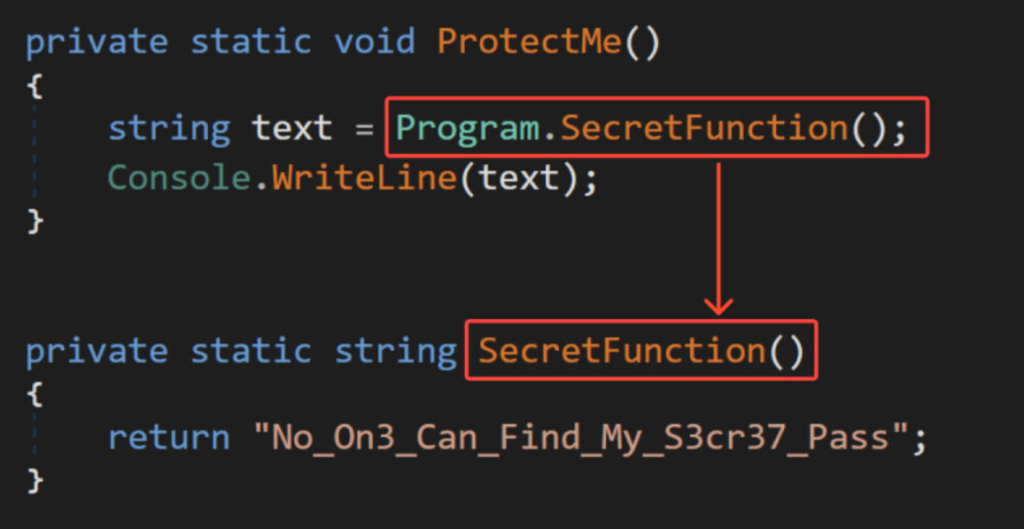
Researchers urged that the IL code needs to be modified to achieve the goal. Then, on the compiled “Source code,” the proper analysis and implementation are required using the “Dnlib” library.
Several steps are needed to be followed to complete this process, and here we have mentioned them:
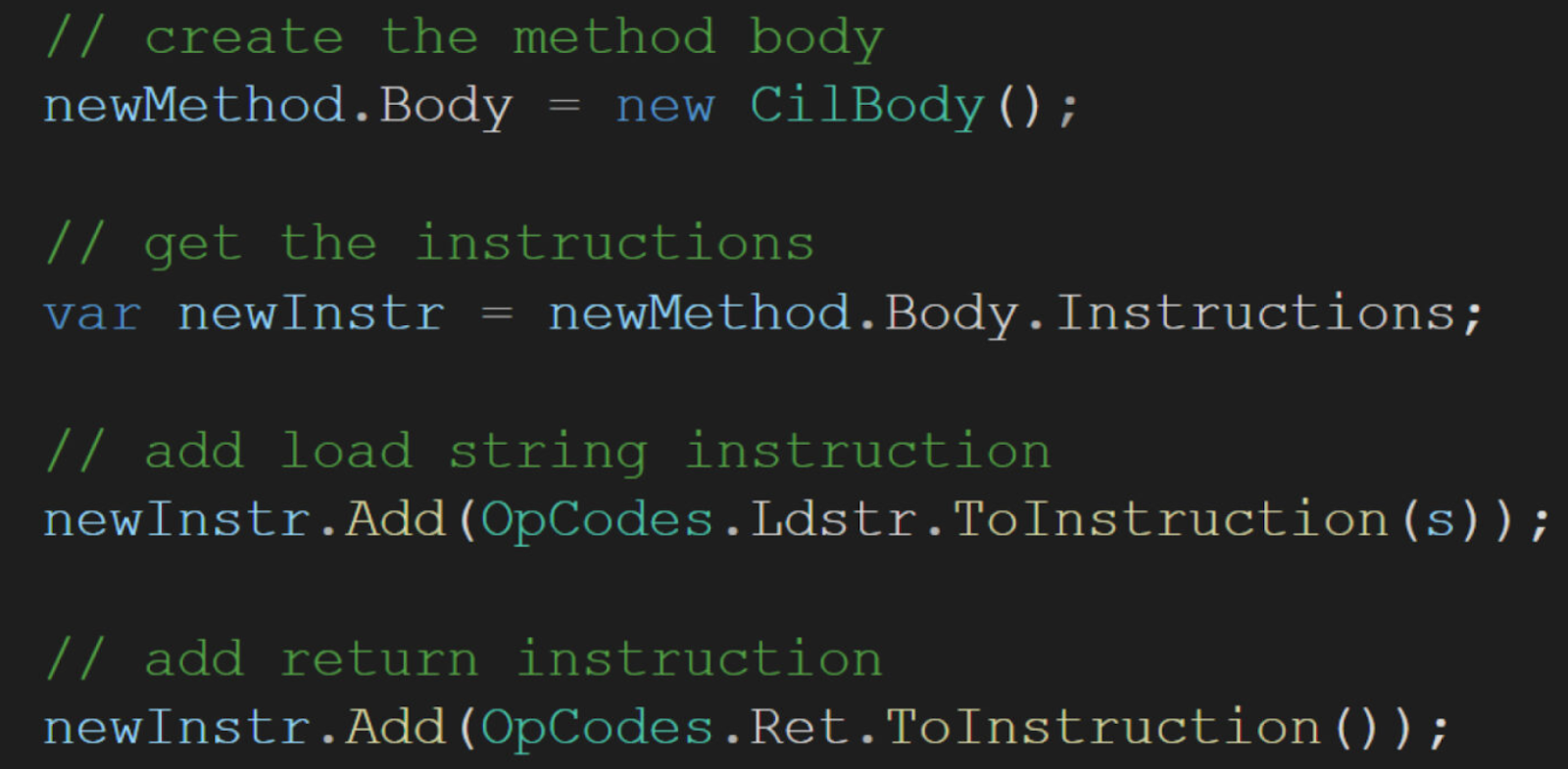
- Locate function “ProtectMe”.
- Go through all the instructions and find each instance of “ldstr” (load string).
- Create a new class and a new function with a random name.
- Add “ldstr” and “ret” instructions to the body of the created function.
- Replace the original “ldstr” with a call to the new function.
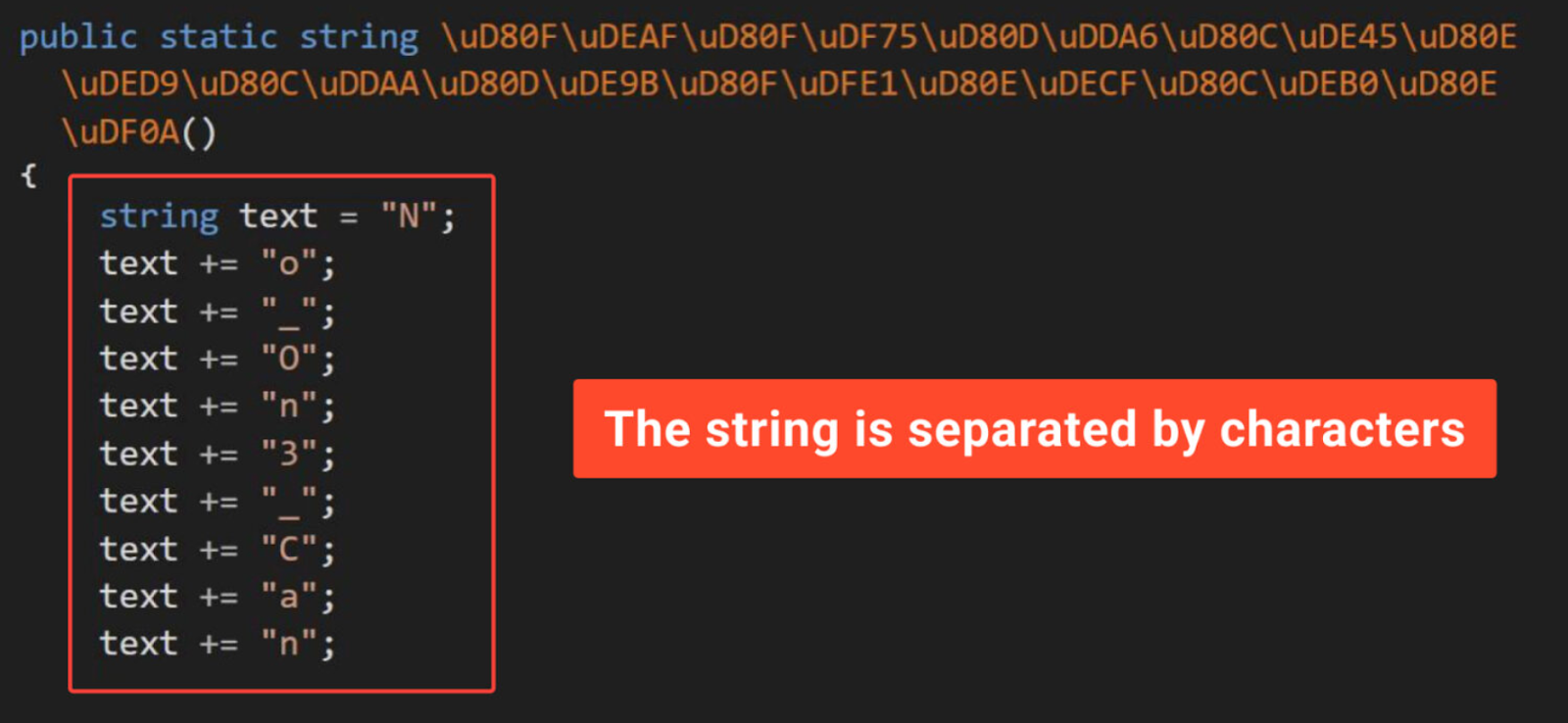
Researchers obscured the original string, but it remains easily discoverable. The cybersecurity analysts fragmented the secret into characters to enhance security by enabling later shuffling for a more challenging code presentation.
Replacing the symbols with numerical representations in the source and decompiled code obscures characters effectively.
Using the “Conv.U2” instruction, each character is converted to an unsigned int, reverted to a string, and appended to the final result.
Researchers tweaked their obfuscator, where the “MaskCharsWithNumVal” function facilitates this conversion.
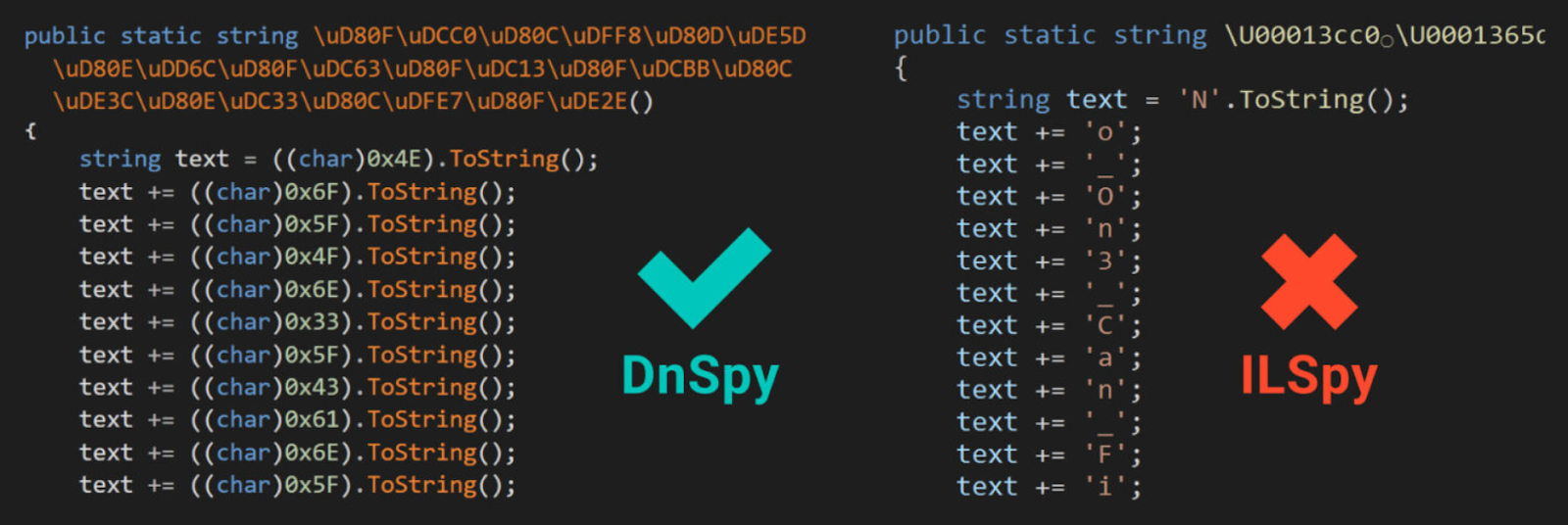
IlSpy is another effective IL code analysis tool that adeptly reverts numerical representations to characters, rendering them readable.
Besides this, examining the file’s binary view reveals the scattered presence of the researchers’ secret.
Threat Intelligence Lookup centralized repository of millions of IOCs extracted from ANY.RUN’s extensive database of interactive malware analysis sessions..
Here below, we have mentioned all the elements that could be used to attack the simple obfuscator:
- Breakpoint
- Memory dump
- The De4dot
Modern obfuscators employ evolved versions of these techniques. With an enhanced understanding, researchers are well-prepared to study contemporary obfuscators thoroughly, which helps them delve into their core difficulties.
Part 2 will cover further code protection methods. How obfuscators counter breakpoints, De4dot, and memory dumps. How to bypass their defenses to comprehend the code and other fascinating elements will also be examined. We will keep you posted.
Try all features of ANY.RUN Interactive malware analysis premium access at zero cost for 14 days with a Free Trial.
Read the full article here