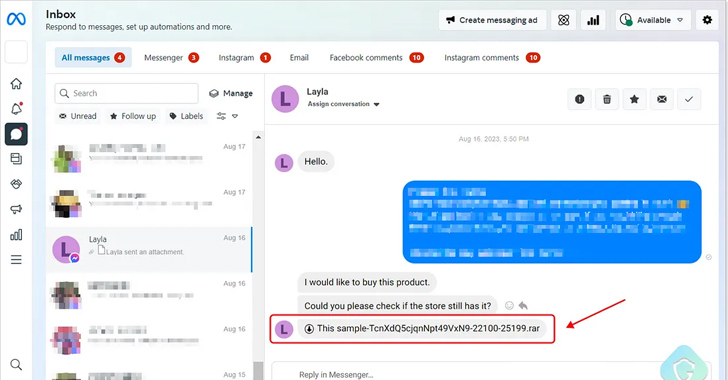
A new phishing attack is leveraging Facebook Messenger to propagate messages with malicious attachments from a “swarm of fake and hijacked personal accounts” with the ultimate goal of taking over the targets’ accounts.
“Originating yet again from a Vietnamese-based group, this campaign uses a tiny compressed file attachment that packs a powerful Python-based stealer dropped in a multi-stage process full of simple yet effective obfuscation methods,” Guardio Labs researcher Oleg Zaytsev said in an analysis published over the weekend.
In these attacks, dubbed MrTonyScam, potential victims are sent messages that entice them into clicking on the RAR and ZIP archive attachments, leading to the deployment of a dropper that fetches the next-stage from a GitHub or GitLab repository.
This payload is another archive file that contains a CMD file, which, in turn, harbors an obfuscated Python-based stealer to exfiltrate all cookies and login credentials from different web browsers to an actor-controlled Telegram or Discord API endpoint.

A clever tactic adopted by the adversary involves deletes all cookies after stealing them, effectively logging victims out of their own accounts, at which point the scammers hijack their sessions using the stolen cookies to change their passwords and seize control of them.
The threat actor’s links to Vietnam comes from the presence of Vietnamese language references in the source code of the Python stealer and the inclusion of Cốc Cốc, a Chromium-based browser popular in the country.
Despite the fact that triggering the infection requires user interaction to download a file, unzip, and execute the attachment, Guardio Labs found that the campaign has witnessed a high success rate where 1 out of 250 victims are estimated to have been infected over the last 30 days alone.

A majority of the compromises have been reported in the U.S., Australia, Canada, France, Germany, Indonesia, Japan, Nepal, Spain, the Philippines, and Vietnam, among others.
“Facebook Accounts with reputation, seller rating, and high number of followers can be easily monetized on dark markets,” Zaytsev said. “Those are used to reach a broad audience to spread advertisements as well as more scams.”
Way Too Vulnerable: Uncovering the State of the Identity Attack Surface
Achieved MFA? PAM? Service account protection? Find out how well-equipped your organization truly is against identity threats
Supercharge Your Skills
The disclosure comes days after WithSecure and Zscaler ThreatLabz detailed new Ducktail and Duckport campaigns that target Meta Business and Facebook accounts using malverposting tactics.
“The Vietnamese-centric element of these threats and high degree of overlaps in terms of capabilities, infrastructure, and victimology suggests active working relationships between various threat actors, shared tooling and TTPs across these threat groups, or a fractured and service-oriented Vietnamese cybercriminal ecosystem (akin to ransomware-as-a-service model) centered around social media platforms such as Facebook,” WithSecure noted.
Read the full article here