Cybersecurity analysts at SentinelOne security firm have recently identified that the Vice Society ransomware gang has switched to custom ransomware which is dubbed “PolyVice.”
There are two algorithms that are used by this custom ransomware in order to implement a robust encryption system:-
Vice Society Ransomware
Researchers consider Vice Society ransomware is might be the split version of HelloKitty ransomware, and since June 2021 it has been active in the threat landscape. Windows and Linux systems are the most commonly targeted by this malware, with a majority of the victims belonging to small and medium companies.
The Vice Society gang was tracked by Microsoft with the DEV-0832 tracker ID, and originally for the first time, it appeared on the threat landscape back in May 2021. Moreover, this hacking group is so popular and notorious for the following illicit skills:-

- Intrusion
- Exfiltration
- Extortion
- Double-extortion
During multiple attacks, several other ransomware operations’ encryptors were also used by the Vice Society ransomware gang and they are like:-
- Zeppelin
- Five Hands
- HelloKitty
There appears to have been a change in the way Vice Society has used the encryptor, with the latest version believed to have been created by a commodity ransomware builder, instead of one that was created by Vice Society itself.
PolyVice Encryptor
Vice Society attacks are defined by the unique signature created by the newly developed PolyVice strain. Dropping ransom notes named ‘AllYFilesAE’ and adding the “.ViceSociety” extension to all the locked files.
There are a number of other groups that use the codebase used for assembling the Vice Society Windows payload as the basis for making custom-branded payloads, including the following:-
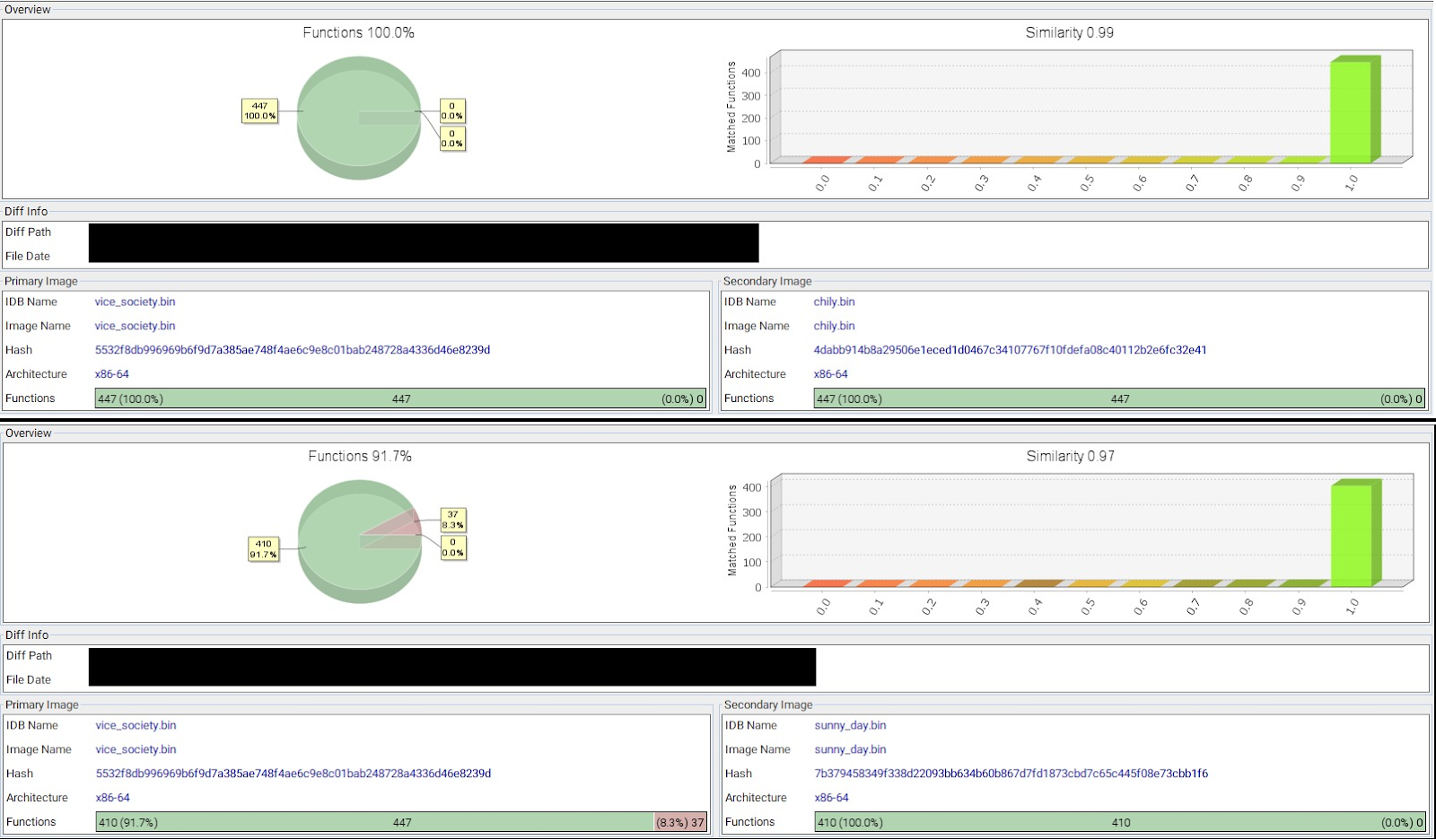
In short, there are significant similarities between the code of PolyVice and Chilly ransomware, and SunnyDay ransomware, and they are similar in terms of function and syntax.
As early as July 13, 2022, the new variant was first spotted in the wild, but it wasn’t until much later that the group was able to fully adopt it.
It is the details specific to each campaign that makes the differences, such as:-
- File extension
- Ransom note name
- Hardcoded master key
- Wallpaper
Encryption Mechanism Implementation
For the purpose of securely encrypting files, PolyVice implements a hybrid encryption mechanism that combines both asymmetric encryptions as well as symmetric encryption.
Open-source implementations of the quantum-resistant NTRUEncrypt algorithm are used for asymmetric encryption. The ChaCha20-Poly1305 algorithm is used for symmetric encryption, and it’s an open-source implementation that is used for this algo.
When the payload is launched, it imports a 192-bit NTRU public key, which is pre-generated by the payload. It then generates on the compromised computer a unique 112-bit NTRU private key pair, which is unique to each victim, that is then used to access the compromised computer.
PolyVice ransomware uses multi-threading for a parallel symmetric data encryption mechanism and it’s a 64-bit binary. There are a variety of speed optimization strategies that can be applied to every file by PolyVice workers by reading the file content.
As a result, PolyVice applies intermittent encryption selectively based on the size of the file. Here below we have mentioned all the criteria that are checked:-
- Encryption is provided for all files smaller than 5MB.
- The contents of files between 5MB and 100MB are partially encrypted, with every second chunk being skipped and the file being broken into 2.5MB chunks.
- Large files greater than 100 MB are split into ten chunks, with 2.5 MB encrypted for each chunk.
It appears that the ransomware was developed by a team of experienced developers or an individual who has experience with the development of ransomware since the encryption scheme is strong and performance optimization is an important part of the development process.
As a result of the adoption of PolyVice Ransomware, their ransomware campaigns are now even more effective. By utilizing a robust encryption scheme, they encrypt victims’ data quickly and effectively.
A continuously growing trend of hyperspecialization and outsourcing of ransomware remains at the forefront of the ransomware ecosystem, which is constantly evolving.
Managed DDoS Attack Protection for Applications – Download Free Guide
Read the full article here

