A sophisticated variant of StrelaStealer malware has been identified, targeting Spanish-speaking users with the primary aim of pilfering email account credentials from popular email clients Outlook and Thunderbird.
This updated strain of StrelaStealer, first spotted in the wild in early November 2022, has been enhanced with advanced obfuscation and anti-analysis techniques, making it a formidable threat to cybersecurity.
The malware is ingeniously delivered via JavaScript embedded in archive files attached to emails. Once the unsuspecting user executes the JavaScript, it drops a 64-bit executable file into the %userprofile% folder and initiates the malware process.
This executable acts as a loader for the payload, cleverly disguised to evade detection.
The technical analysis reveals that the malware employs a single-byte XOR encryption to decrypt an encoded Portable Executable (PE) file containing the malicious payload.
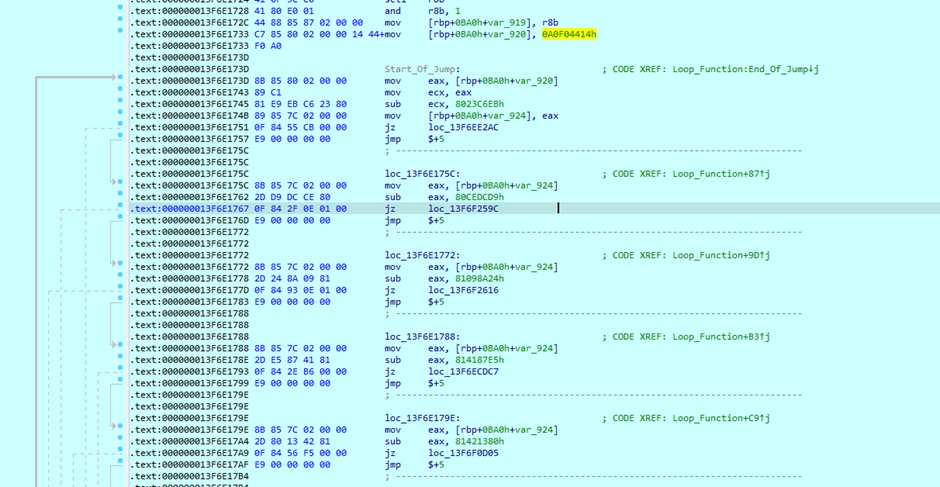
The obfuscation techniques are particularly effective, involving jump blocks, multiple loops, and dummy functions designed to waste analysts’ time and delay execution.
Trustifi’s Advanced threat protection prevents the widest spectrum of sophisticated attacks before they reach a user’s mailbox. Try Trustifi Free Threat Scan with Sophisticated AI-Powered Email Protection .
Targeting Specific Users
One of the most intriguing aspects of StrelaStealer is its selective execution based on the keyboard layout.
The malware checks the system’s keyboard layout against a list of hardcoded values corresponding to countries like Germany, Spain, Italy, and Poland.
If the system’s layout matches any of these, the malware proceeds; otherwise, it terminates itself.
SonicWall’s recent blog highlights the emergence of StrelaStealer, a new malware that targets Outlook and Thunderbird email client users.
A recent tweet from Virus Bulletin shared that SonicWall’s Capture Labs threat research team has analyzed an updated variant of StrelaStealer.
Stealing Confidential Data
StrelaStealer’s primary function is to steal confidential data from infected machines, specifically targeting Mozilla Thunderbird and Outlook.
It searches for specific files and registry keys containing user credentials. It encrypts the harvested data using a single-byte XOR encryption before exfiltrating it to an attacker-controlled server.
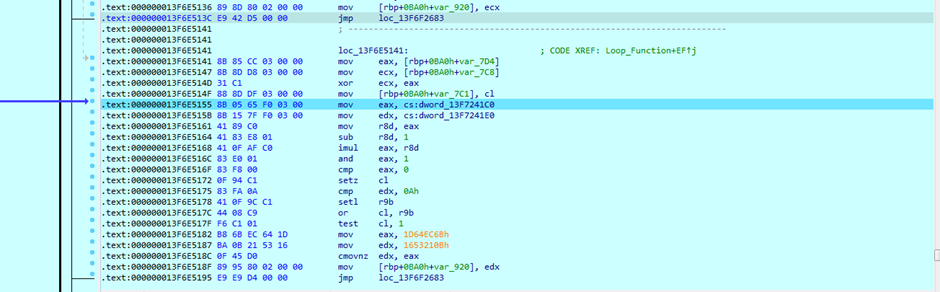
Evading Detection
The malware goes to great lengths to avoid detection by antivirus products.
It intentionally omits to copy the PE header to the injected PE and employs dynamic API resolution to obscure its activities further.
This updated variant of StrelaStealer underscores the evolving threat landscape and the continuous need for vigilance among users and cybersecurity professionals.
The malware’s sophisticated evasion techniques and targeted approach make it a significant threat, particularly to Spanish-speaking users.
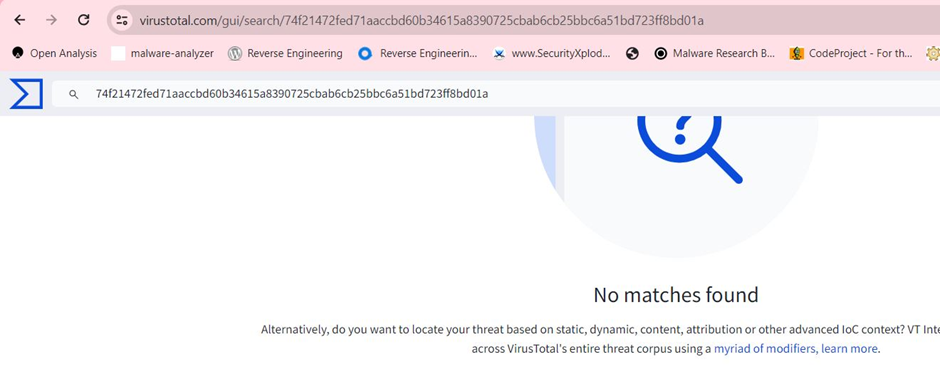
As of this writing, the archive file containing StrelaStealer has not been found on popular threat intelligence sharing portals like VirusTotal, indicating the malware’s relative obscurity and potential for widespread damage if not adequately addressed.
The emergence of this updated StrelaStealer variant is a stark reminder of cyber threats’ persistent and evolving nature.
Users are advised to exercise caution when opening email attachments, even from seemingly trustworthy sources, and to keep their antivirus software current.
As the cyber threat landscape evolves, staying informed and vigilant is more crucial than ever.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.
Read the full article here

