The Cyber-Extortion Trinity—the BianLian, White Rabbit, and Mario ransomware gangs—was observed by researchers working together to launch a joint extortion campaign against publicly traded financial services companies.
Although these joint ransomware attacks are uncommon, they may grow more often due to Initial Access Brokers (IABs) working with various Dark Web groups.
Law enforcement actions that establish networks of cybercriminals are another aspect that might be encouraging more cooperation. Members of these threat actor networks who have been displaced might be more open to working with competitors.
Resecurity, Inc. (USA) has found this significant connection between three main ransomware gangs based on a recent Digital Forensics & Incident Response (DFIR) engagement with a law enforcement agency (LEA) and one of the top investment firms in Singapore.
Overview of BianLian, White Rabbit, and Mario Ransomware Gangs
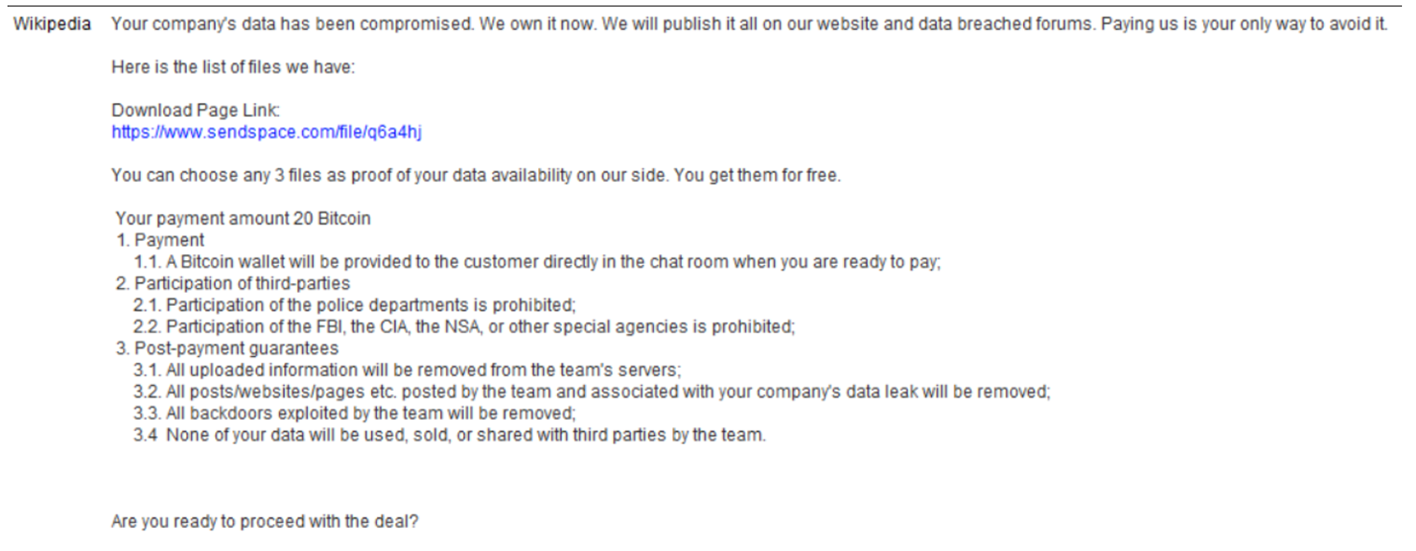
After attacking a U.S. bank in December 2021, the White Rabbit ransomware family was first observed in the wild, focusing on financial institutions (FIs).
Giving victims four or five days to pay their ransom was a strategy that the threat actors behind White Rabbit initially adopted. This ransom family’s note threatens to report victims to oversight authorities, putting businesses at risk of fines and General Data Protection Regulation (GDPR) enforcement if they don’t pay the extortion money on time.
Notably, the Ransomhouse Telegram Channel has always been mentioned in White Rabbit’s ransomware note.
According to the CISA-ACSC advisory, Since June 2022, companies in several crucial infrastructure sectors in the United States have been the target of BianLian, a cybercriminal group that develops, deploys, and demands data using ransomware.
They have targeted professional services, property development, and Australia’s essential infrastructure sectors.
Using legitimate Remote Desktop Protocol (RDP) credentials, BianLian acquires access to victim systems, performs credential harvesting and discovery using open-source tools and command-line scripting, and exfiltrates victim data via File Transfer Protocol (FTP), Rclone, or Mega.
Actors from the BianLian organization then threatened to release data to extract money. The BianLian group used a double-extortion methodology in which they first encrypted the victims’ systems after exfiltrating the data.
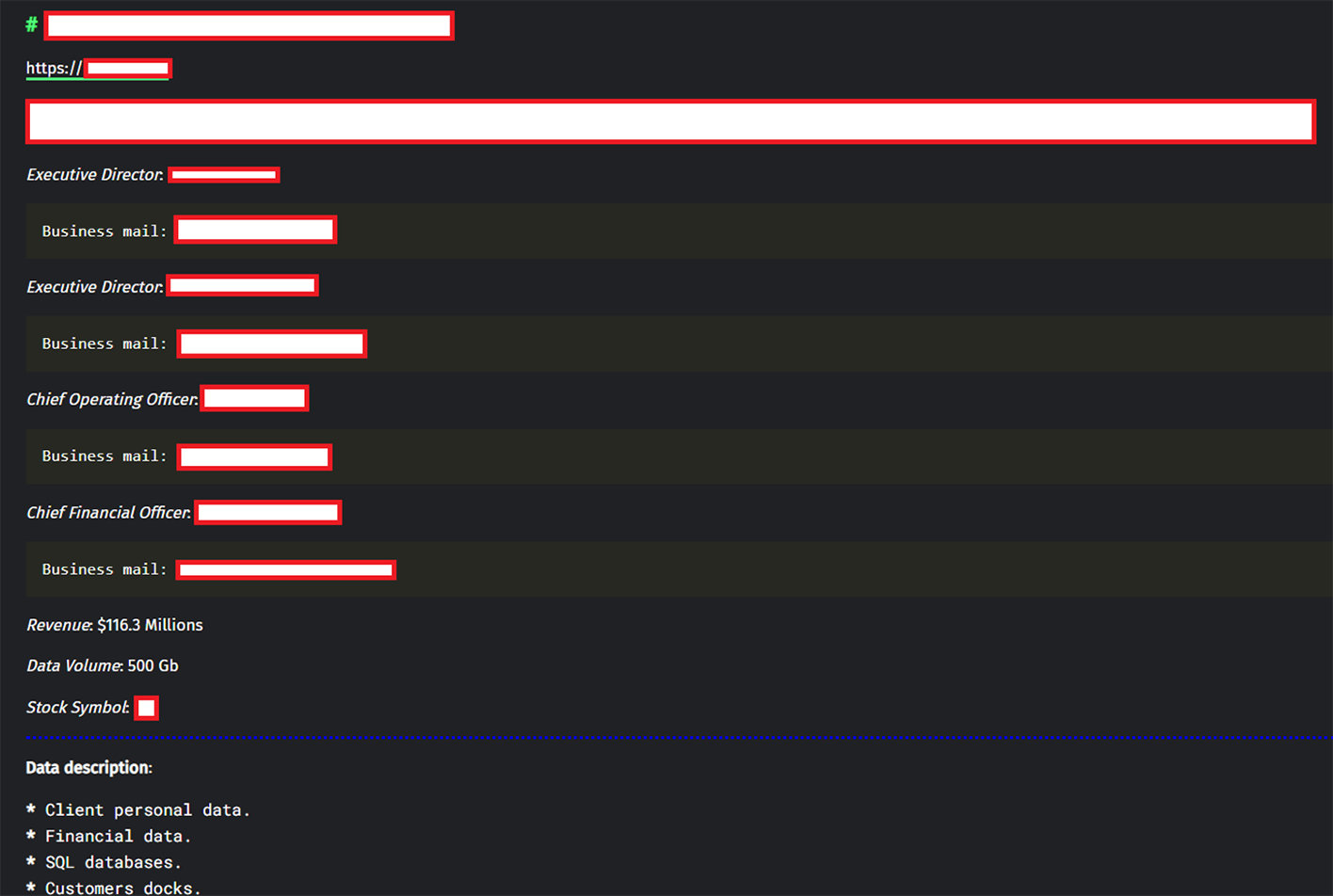
MarioLocker is a ransomware-type malware. People whose computers are infected with this kind of malicious software typically aren’t able to view or use their files.
Subsequent analysis revealed that additional ransomware notes bearing a signature linked to the Mario ransomware were found on a number of the victim’s compromised computers. The note included a clear reference to the RansomHouse Telegram Channel.

Hence, the current dynamic ransomware threat landscape poses a significant challenge for organizations, and this instance highlights the vital significance of proactive cybersecurity strategy and planning.
Regular system updates, strong threat detection systems, and employee training to assist staff in recognizing and preventing social engineering attacks are recommended.
Read the full article here

