SSH protocol is one of the most used protocols across several organizations to establish a remote terminal login and file transfer. SSH consists of an authenticated key exchange for establishing the secure channel connection to ensure integrity and confidentiality.
However, a new technique named “Terrapin attack” has been discovered, which will allow threat actors to downgrade the SSH protocol version, thus allowing the exploitation of vulnerable servers. Additionally, the threat actor can redirect the victim’s login into a shell under the attacker’s control.
Terrapin Attacking SSH Protocol
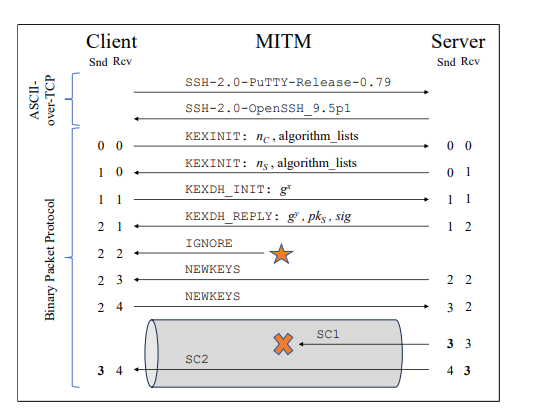
Terrapin attack is a kind of prefix truncation attack in which the initial encrypted packets sent through the secure SSH channel can be deleted without the server or client noticing it.
There are two root causes for this flaw; one of them is the optional messages that are allowed in the SSH handshake, which do not require authentication. Second, the SSH handshake does not reset message sequence numbers when encryption is enabled.
Root Cause Analysis
SSH Does Not Protect the Full Handshake Transcript
SSH server authentication uses a signature to verify the handshake integrity. However, the handshake is formed with a constant list of handshake messages instead of a complete transcript. This creates an authentication flaw that allows an attacker to tamper with the handshake and manipulate the sequence numbers.
SSH Does not Reset Sequence Numbers
As specified, the SSH does not sequence numbers during the initial connection. Instead, it increases sequence numbers monotonically, which is not associated with the encryption state. Hence, any tampered sequence number before the secure channel goes directly into the channel.
With respect to these two root causes, there were many possible attacks, such as:
Sequence number manipulation: An attacker can increase the receiver counter, allowing full control of the receive and send counters.
Prefix Truncation attack on the BPP (Binary Packet Protocol): An attacker can manipulate the sequence numbers to delete a specific number of packets at the initial secure channel without any noise.
Extension Negotiation Downgrade attack: An attacker can manipulate the client into believing that the server does not support recent signature algorithms, which will prevent certain countermeasures from being executed.
Rogue Extension Attack and Rogue Session Attack: An attacker can replace the victim’s extension info message with a custom one. On the other hand, an attacker can also inject a malicious user authentication message, which will log the victim into a shell that is controlled by the attacker, which will give complete control over the victim’s terminal.
Furthermore, a complete report has been published, which provides detailed information about the attack scenarios, the results of the attack, and the observed behavior.
Read the full article here

