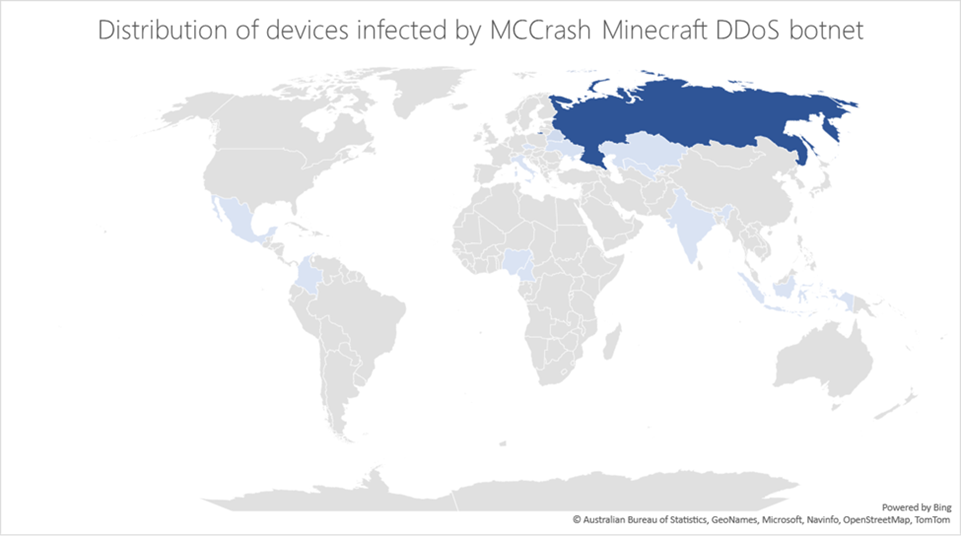
A cross-platform botnet, ‘MCCrash’ that starts out from malicious software downloads on Windows devices and spreads to a range of Linux-based devices was recently examined by the Microsoft Defender for IoT research team.
The botnet spreads by obtaining the default credentials on Secure Shell (SSH)-capable devices that are open to the internet. Particularly, IoT devices may be vulnerable to attacks like this botnet as they frequently have remote configuration enabled with potentially unsafe settings.
This activity cluster is being monitored by Microsoft under the name DEV-1028, a cross-platform botnet that affects Windows, Linux, and IoT devices.
The DEV-1028 botnet is known to launch distributed denial of service (DDoS) attacks against private ‘Minecraft servers’.

“Our analysis of the DDoS botnet revealed functionalities specifically designed to target private Minecraft Java servers using crafted packets, most likely as a service sold on forums or darknet sites,” reports Microsoft
Researchers say once it infects a device, it can self-spread to other systems on the network by brute-forcing SSH credentials.
How Does This Botnet Affect Multiple Platforms?
Microsoft researchers discovered that the botnet’s first entry points were devices that had been compromised by the installation of malicious cracking tools that claimed to be able to get illegal Windows licenses.

The cracking tools contain malicious PowerShell code that downloads a file named ‘svchosts.exe,’ which launches ‘malicious.py,’ the primary botnet payload.
After that, MCCrash tries to propagate to more networked devices by attacking Linux and IoT devices with brute-force SSH attacks.
“The botnet’s spreading mechanism makes it a unique threat because while the malware can be removed from the infected source PC, it could persist on unmanaged IoT devices in the network and continue to operate as part of the botnet.” Microsoft
Linux and Windows environments can both run the malicious Python script. Upon initial launch, it creates a TCP communication channel over port 4676 with the C2 and sends basic host information, such as the system it is running on.
On Windows, MCCrash establishes persistence by adding a Registry value to the “SoftwareMicrosoftWindowsCurrentVersionRun” key, with the executable as its value.
“Based on our analysis, the botnet is primarily used to launch DDoS attacks against private Minecraft servers using known server DDoS commands and unique Minecraft commands”, researchers.
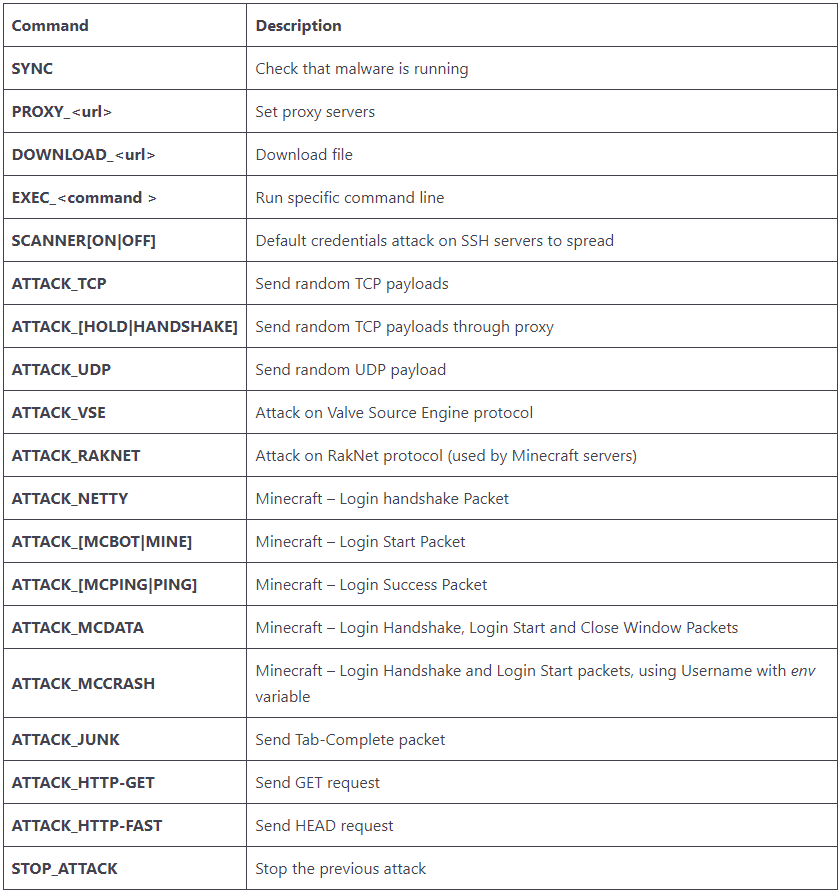
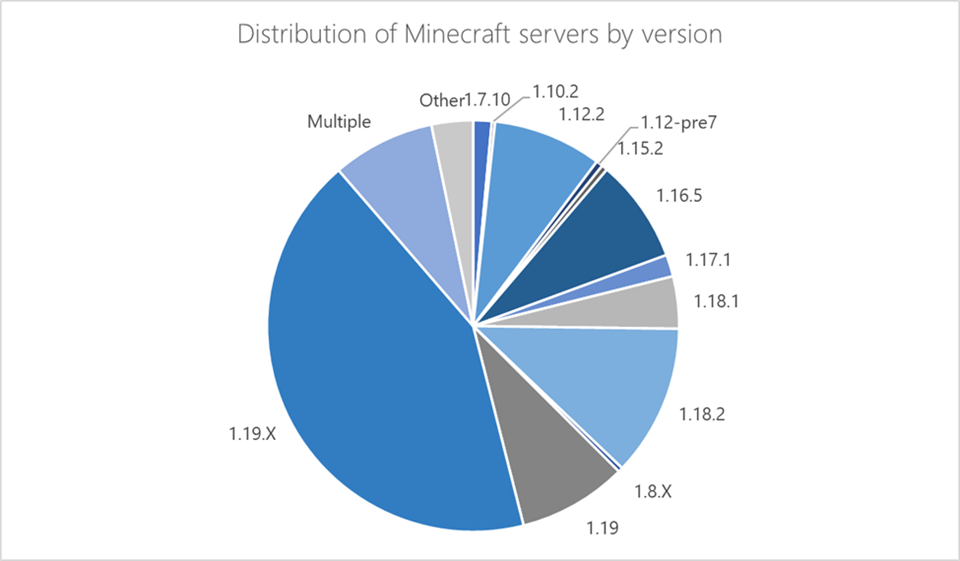
Threat actors created the botnet to target Minecraft server version 1.12.2, but all server versions from 1.7.2 and up to 1.18.2 are also vulnerable to attacks.
Mitigation
Microsoft researchers recommend keeping your IoT devices’ firmware up to date. Change the default password with a stronger (lengthy) one, and turn off SSH connections when not in use to prevent them from botnets.
Penetration Testing As a Service – Download Red Team & Blue Team Workspace
Read the full article here

