DDoS attack evolves with changing tech and attacker motivations, with recent cases involving significant damages and legal consequences.
Recently, the DDoS defense platform of Akamai Prolexic prevented the largest DDoS attack on a major U.S. financial institution’s platform, reaching 633.7 Gbps and 55.1 Mpps.
Security analysts at Akamai reported that this largest DDoS attack lasted for less than 2 minutes, and in this attack, threat actors used the combination of the following flood attack vectors:-
Prolexic’s DDoS protection shield platform prevented several record-breaking attacks in Europe and Asia-Pacific, including a 704.8 Mpps spike in September 2022 and a 900.1 Gbps surge in February 2023.
Malicious Traffic source
Here below, we have mentioned the top malicious traffic sources:-
- Bulgaria
- Brazil
- China
- India
- United States
- Thailand
- Russia
- Ukraine
- Vietnam
- Japan
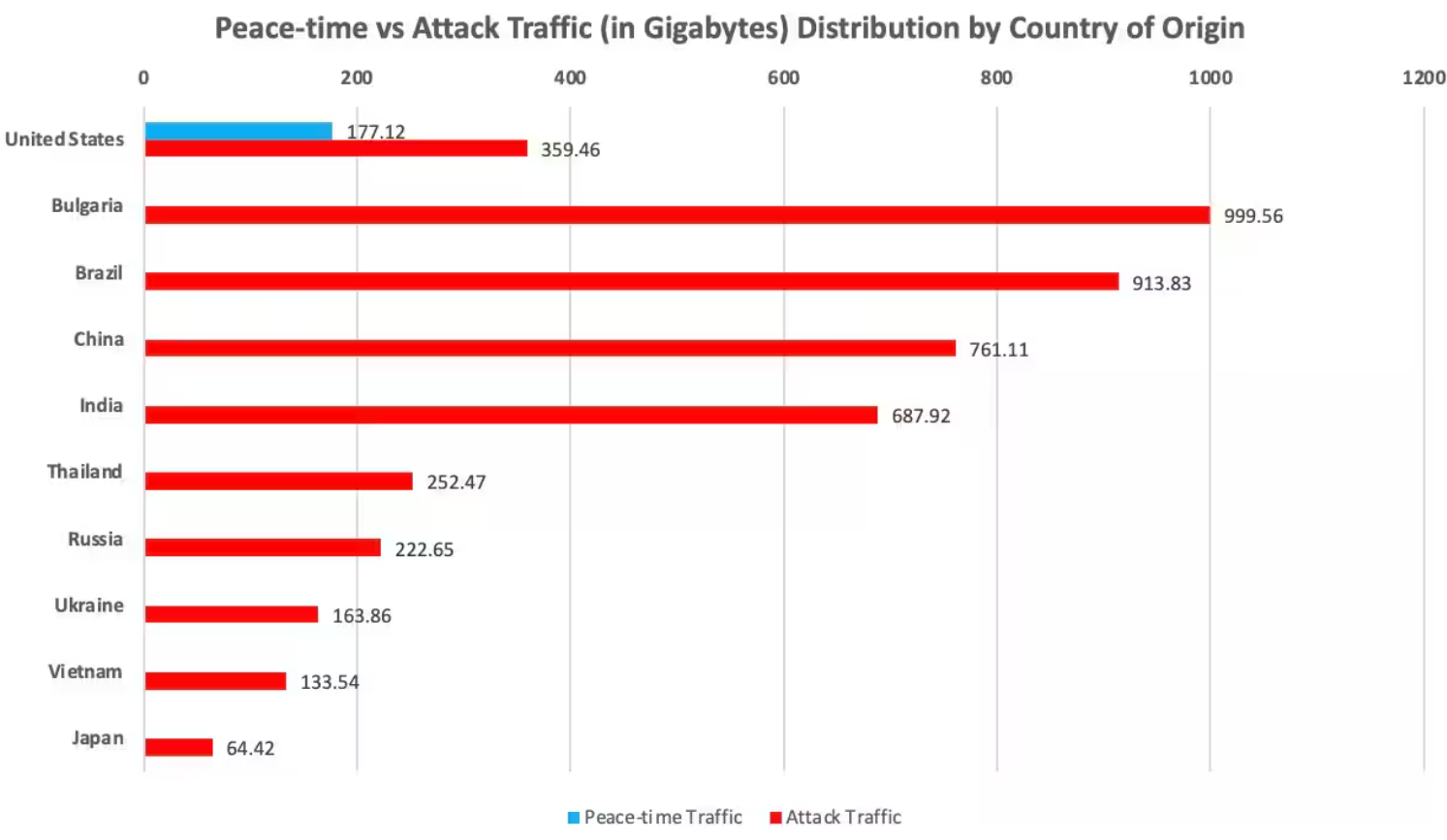
Moreover, U.S. traffic surged to over twice its usual volume during the attack. DDoS attacks, deliberate and cost-effective, now serve as smokescreens for triple extortion ransomware attacks on vital financial institutions, impacting entire economies.
Attack Analysis
From 10-15% historically, DDoS attacks on financial services surged to over 30% since 2021, marking a significant shift in attack patterns once seen primarily in the following sectors:-
- Software
- Tech
- Gaming
- Media
- Entertainment
- Internet
- Telecom
Besides this, a surge in deeper reconnaissance threats and attacks on vulnerable assets was noted by the security researchers at Akamai.
However, the recent DDoS attack seems quite different than the usual ones, as in this attack, threat actors directly targeted a major US-based financial institution’s primary web page, aiming to disrupt online banking.
Moreover, Akamai confirmed zero collateral damage due to proactive defense with their global command center partnership. While in today’s high-risk environment, a solid DDoS strategy is crucial and essential.
Recommendations
Here below, we have mentioned all the recommendations provided by the Akamai:-
- Make sure to adopt CISA recommendations promptly.
- Check all the key subnets and IPs for effective mitigation controls.
- Establish continuous DDoS security controls as your initial defense layer.
- Enhance security with advanced network cloud firewall beyond basic DDoS protection.
- Form a proactive crisis team and keep incident plans and runbooks up to date.
Keep informed about the latest Cyber Security News by following us on Google News, Linkedin, Twitter, and Facebook.
Read the full article here

