A financially motivated threat actor known as UNC4990 is leveraging weaponized USB devices as an initial infection vector to target organizations in Italy.
Google-owned Mandiant said the attacks single out multiple industries, including health, transportation, construction, and logistics.
“UNC4990 operations generally involve widespread USB infection followed by the deployment of the EMPTYSPACE downloader,” the company said in a Tuesday report.
“During these operations, the cluster relies on third-party websites such as GitHub, Vimeo, and Ars Technica to host encoded additional stages, which it downloads and decodes via PowerShell early in the execution chain.”

UNC4990, active since late 2020, is assessed to be operating out of Italy based on the extensive use of Italian infrastructure for command-and-control (C2) purposes.
It’s currently not known if UNC4990 functions only as an initial access facilitator for other actors. The end goal of the threat actor is not clear, although in one instance an open-source cryptocurrency miner is said to have been deployed after months of beaconing activity.
Details of the campaign were previously documented by Fortgale and Yoroi in early December 2023, with the former tracking the adversary under the name Nebula Broker.
The infection begins when a victim double-clicks on a malicious LNK shortcut file on a removable USB device, leading to the execution of a PowerShell script that’s responsible for downloading EMPTYSPACE (aka BrokerLoader or Vetta Loader) from a remote server via another intermedia PowerShell script hosted on Vimeo.
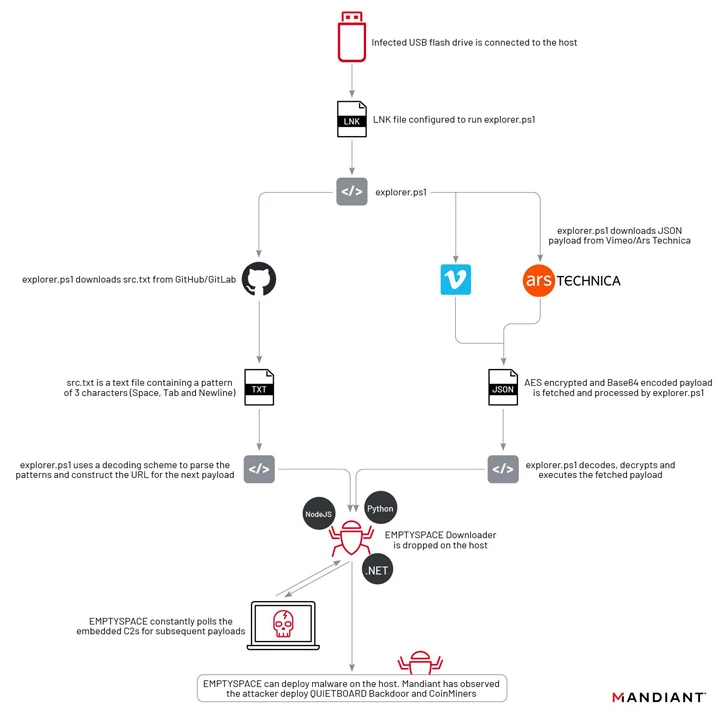
Yoroi said it identified four different variants of EMPTYSPACE written in Golang, .NET, Node.js, and Python, which subsequently acts as a conduit for fetching next-stage payloads over HTTP from the C2 server, including a backdoor dubbed QUIETBOARD.
A notable aspect of this phase is the use of popular sites like Ars Technica, GitHub, GitLab, and Vimeo for hosting the malicious payload.
“The content hosted on these services posed no direct risk for the everyday users of these services, as the content hosted in isolation was completely benign,” Mandiant researchers said. “Anyone who may have inadvertently clicked or viewed this content in the past was not at risk of being compromised.”

QUIETBOARD, on the other hand, is a Python-based backdoor with a wide range of features that allow it to execute arbitrary commands, alter crypto wallet addresses copied to clipboard to redirect fund transfers to wallets under their control, propagate the malware to removable drives, take screenshots, and gather system information.
Additionally, the backdoor is capable of modular expansion and running independent Python modules like coin miners as well as dynamically fetching and executing Python code from the C2 server.
“The analysis of both EMPTYSPACE and QUIETBOARD suggests how the threat actors took a modular approach in developing their toolset,” Mandiant said.
“The use of multiple programming languages to create different versions of the EMPTYSPACE downloader and the URL change when the Vimeo video was taken down show a predisposition for experimentation and adaptability on the threat actors’ side.”
Read the full article here

