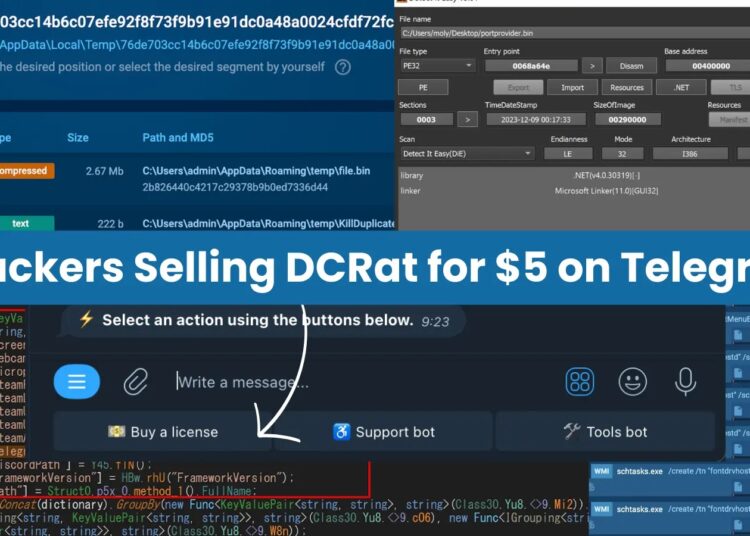
Recently, the cybersecurity researchers at ANY.RUN identified that hackers are selling DCRat subscriptions for $5 on the Telegram groups.
Hackers sell Remote Access Trojan (RAT) subscriptions to other malicious actors to generate revenue. These subscriptions provide buyers with unauthorized access to compromised computers.
This enables them to control and monitor the infected devices remotely. The underground market for RAT subscriptions allows threat actors to exploit compromised systems for various malicious activities.
ANY.RUN is a cloud-based environment for analyzing Windows malware and Linux-based samples. Malware analysts, SOC, DFIR teams can safely examine threats, simulate different scenarios, and gain insights into malware behavior to improve cybersecurity strategies.
ANY.RUN also allows researchers to understand malware behavior, collect IOCs, and easily map malicious actions to TTPs—all in our interactive sandbox.
The Threat Intelligence Lookup platform helps security researchers find relevant threat data from sandbox tasks of ANY.RUN.
Technical analysis
DCRat has been a powerful and active malware since 2018 that grants full Windows backdoor access, collects sensitive data, captures screenshots, and steals Telegram, Steam, and Discord credentials.
Underestimating the complexity of this powerful malware could risk major security breaches and data loss.
Underground sites show that DCRat is becoming more and more popular. Even though it’s cheap, it has a lot of spying features, such as the ability to access social network accounts.
DCRat (aka Dark Crystal RAT) is a dangerous Remote Access Trojan (RAT) and information stealer. Its dual functionality, modular architecture, and low $5 price make it versatile and accessible.
This RAT is customizable for specific objectives and its constantly mutating code helps threat actors in evading signature-based detection.
Due to these key versatilities, it’s been actively used by both beginner and expert threat actors.
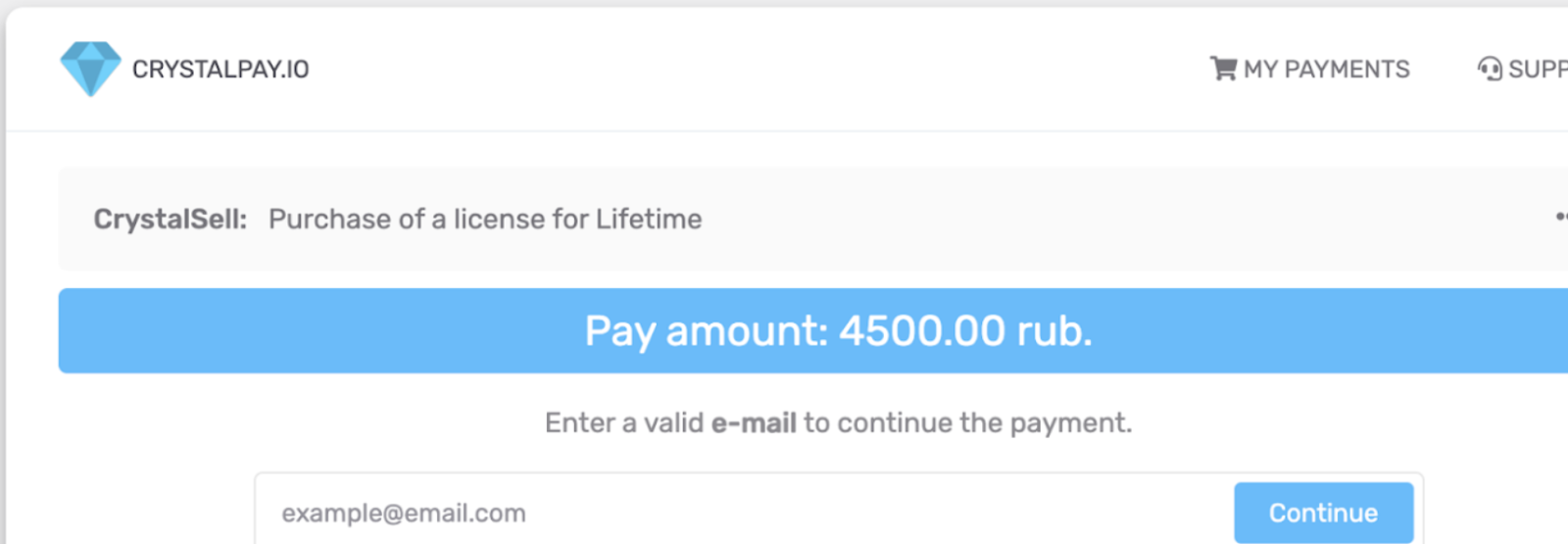
Here below we have mentioned the payment page for DCRat that was hosted on:-
The team behind DCRat is quite cautious about their OPSEC, and for this:-
- They do all communication through Telegram.
- They only accept crypto payments to burner wallets.
- They use crystalpay[.]io to anonymize transactions further.
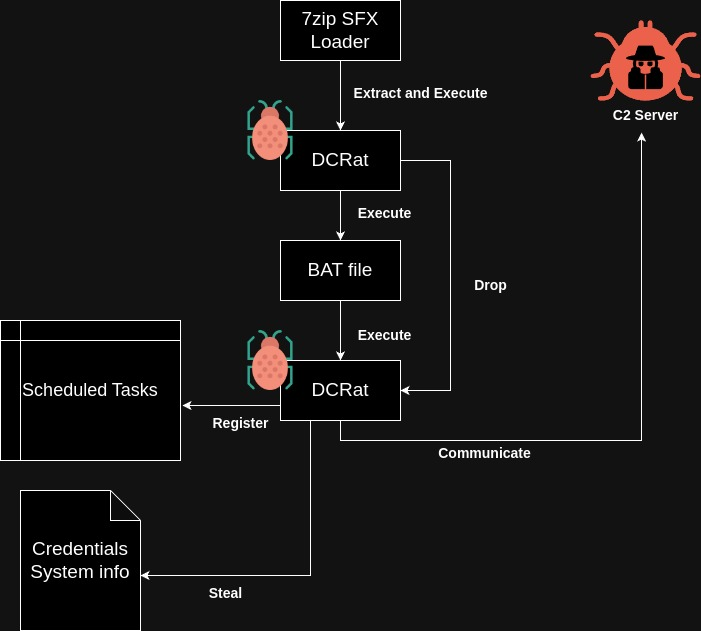
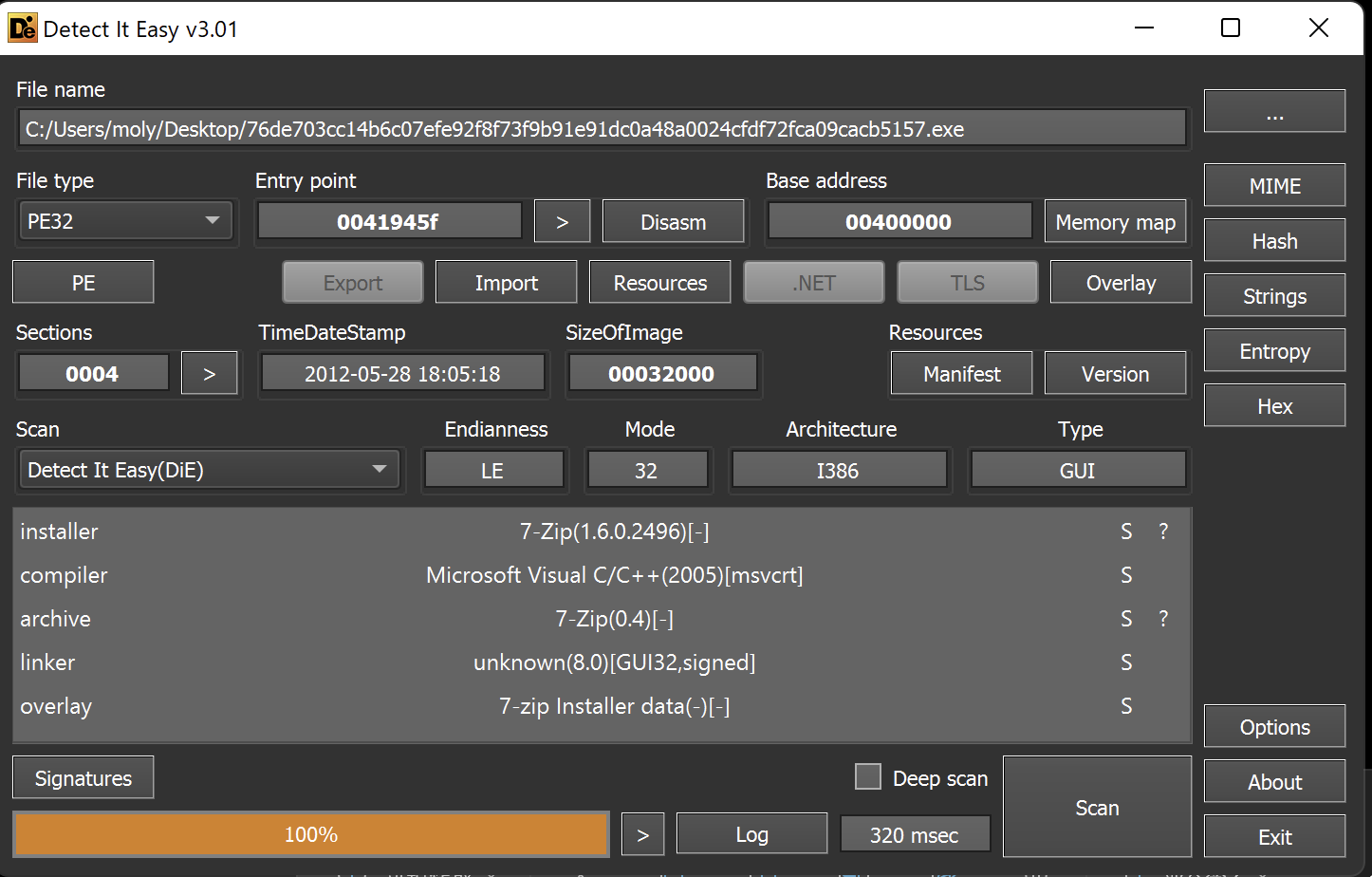
DCRat loader is identified as an SFX file by tools like “Detect It Easy.” The SFX files are typically used for software installation and execute embedded scripts to extract and run files without user knowledge.
The .NET app obfuscation alters source code to hide the understanding, though tools like DnSpy aid analysis. While studying DCRat’s “Upload” function, it reveals the C2 server address by examining decompiled source code.
Decompiled .NET code has unique namespaces for security and communication functions. Namespace ns12 decrypts malware configuration, while dgz handles C2 communication decryption.
More than 300,000 analysts use ANY.RUN is a malware analysis sandbox worldwide. Join the community to conduct in-depth investigations into the top threats and collect detailed reports on their behavior..
Subscription Model
Through a Telegram group, the sales of DCRat occur; in this Telegram group, the sales are held often. Besides this, it also uses a subscription model with the following typical prices:-
- 2 months: 5$
- 1 year: 19$
- Lifetime: 39$
If we talk about the price tags then it’s completely not complainable, as the price tags are already inexpensive.
However, the price is reduced even further, and the developers behind this RAT deploy a Telegram bot to offer DCRat “licenses.”
About ANY.RUN
ANY.RUN is an interactive cybersecurity service that enables professionals to analyze malware and understand its behavior in a safe, controlled environment. The service is dedicated to providing comprehensive analysis tools to combat digital threats.
Trusted by over 400,000 security specialists, ANY.RUN empowers SOC and DFIR teams to investigate threats efficiently through its cloud-based malware sandbox.
You can analyze a malware file, network, module, and registry activity with the ANY.RUN malware sandbox.
IOCs
- DCRat SFX: 76de703cc14b6c07efe92f8f73f9b91e91dc0a48a0024cfdf72fca09cacb5157
- DCRat: 5fe993c74d2fa4eb065149591af56011855a0a8f5471dab498d9e0f6641c6851
- C2 domain: 019214cm[.]nyashland[.]top
- C2: hxxp://019214cm[.]nyashland[.]top/EternalLineLowgameDefaultsqlbaseasyncuniversal[.]php
Read the full article here