Large-scale malware distribution campaigns are abusing Google Cloud Run to transmit banking trojans, including Astaroth (also known as Guildma), Mekotio, and Ousaban, to European and Latin American targets.
With Cloud Run, you can promptly execute your code on top of Google’s scalable infrastructure due to a fully managed platform. It enables the operation of front-end and back-end services, batch processing, website and application deployment, and task queuing without requiring infrastructure management.
More than 300,000 analysts use ANY.RUN is a malware analysis sandbox worldwide. Join the community to conduct in-depth investigations into the top threats and collect detailed reports on their behavior..
In particular, after September 2023, the amount of emails related to these efforts has expanded dramatically, and experts are still routinely seeing new email distribution campaigns.
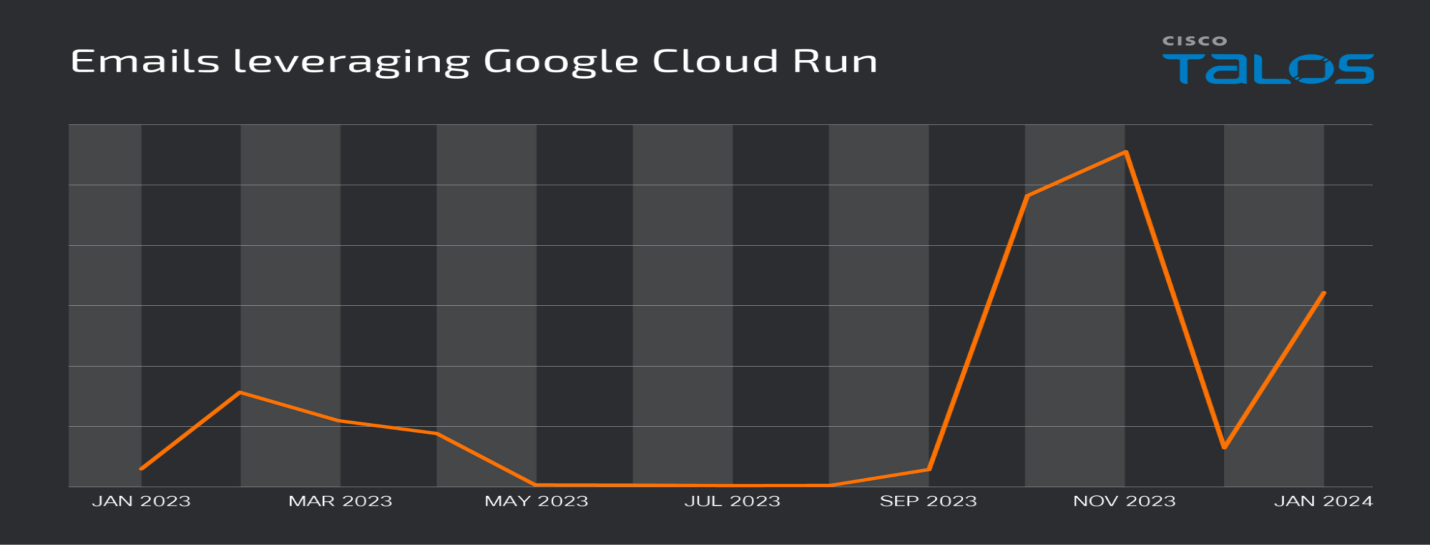
Emails Leveraging Google Cloud Run
With the vast majority of emails being sent in Spanish, the language distribution of the emails seen in these campaigns also shows a strong concentration on LATAM. It also looks like victims who speak Italian are the target of lower-volume activities.
“These emails are being sent using themes related to invoices or financial and tax documents, and sometimes pose as being sent from the local government tax agency in the country being targeted,” Cisco Talos researchers shared with Cyber Security News.
In one case, the email appears to be from Argentina’s local government tax agency, Administración Federal de Ingresos Públicos (AFIP), which has been the focus of recent malspam operations.
Using the run[.]app as the top-level domain (TLD) identifies the email URLs, leading to Google Cloud Run.
When victims click on these URLs, they are taken to the threat actors’ Cloud Run web services, where they receive the files needed to start the infection process.
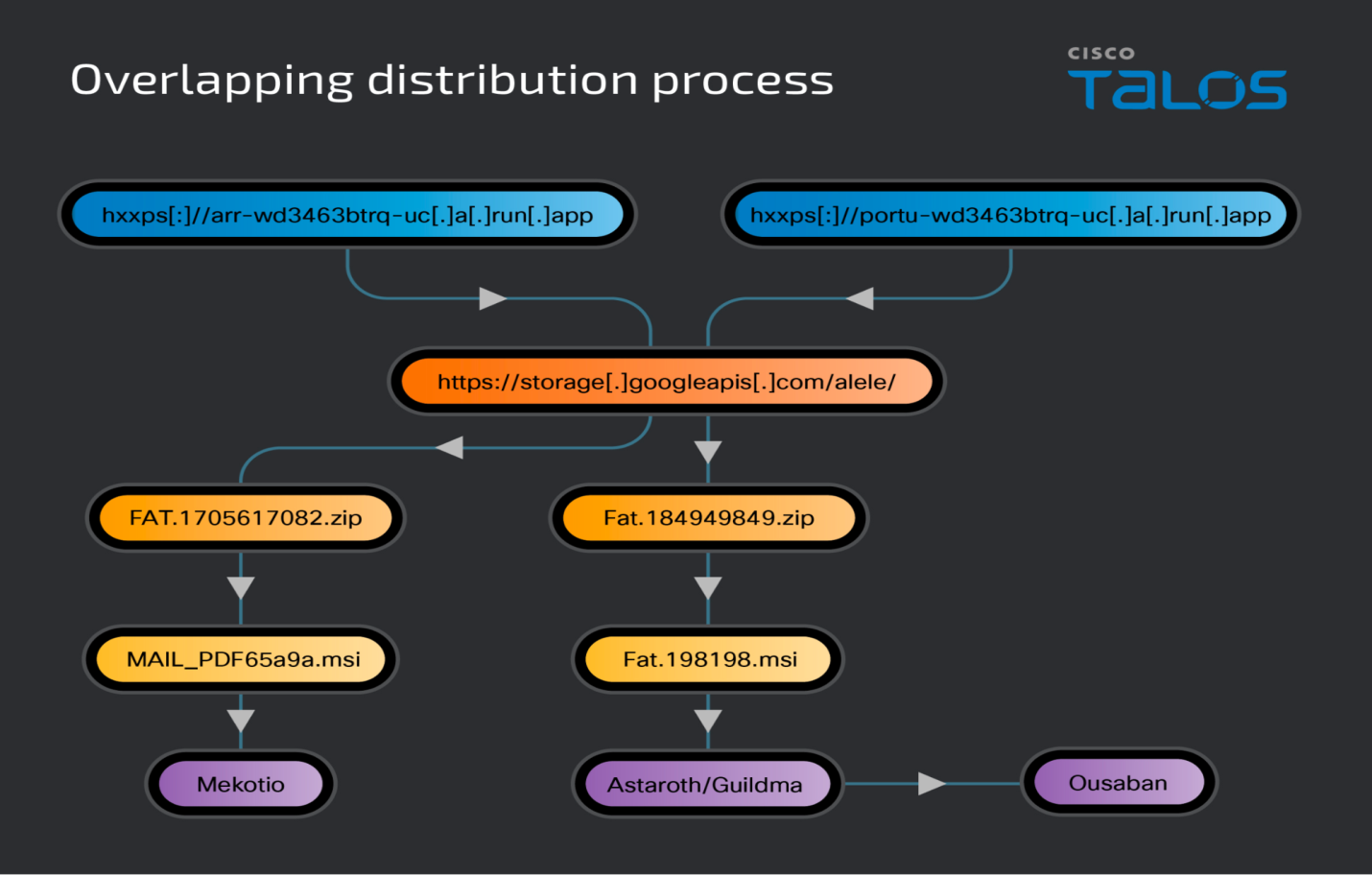
Researchers have observed the distribution of Astaroth and Mekotio in this way, where they are sent as malicious Microsoft Installers (MSI) files that act as the Stage 1 payload to start the infection process.
In the case of the Mekotio scenario shown below, the adversary’s Google Cloud Run web service is frequently the source of the MSI file delivery.
Under some circumstances, the Google Cloud Run web service replies with a 302 redirect to the Google Cloud file location (hxxps[:]//storage[.]googleapis[.]com). A malicious MSI is contained in a ZIP archive that is delivered as a result of the redirect.
According to a 2020 Cisco Talos assessment, Astaroth uses various effective anti-analysis/evasion strategies. Astaroth created a clever method of encoding and encrypting command and control communications (C2) using the descriptions of YouTube channels.
“If a target bank is open, the malware is capable of logging keystrokes and taking screenshots of the screen around the mouse pointer when the user clicks on the screen,” researchers said.
Another banking trojan that has historically targeted victims in Latin America is called Mekotio. Its purpose is to extract confidential financial data from compromised systems.
Qusaban is delivered through malicious MSI files spread in phishing emails, stealing sensitive data from financial institutions
“We have observed all three malware families being delivered during the same timeframe from the same storage bucket within Google Cloud,” researchers said.
This, in conjunction with overlapping distribution TTPs, could point to cooperation or connections between the threat actors operating the malware families’ distribution efforts.
You can block malware, including Trojans, ransomware, spyware, rootkits, worms, and zero-day exploits, with Perimeter81 malware protection. All are extremely harmful, can wreak havoc, and damage your network.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.
Read the full article here

