Bazel, an open-source software used for automation of building and testing, has been discovered with a critical supply chain vulnerability that could allow a threat actor to inject malicious code into the Bazel codebase, create a backdoor, and affect the production environment of anyone that uses Bazel.
Researchers stated that millions of projects that use Bazel, such as Kubernetes, Angular, Uber, LinkedIn, Databricks, Dropbox, Nvidia, Google, and many more, could have been affected due to this vulnerability. However, this vulnerability was reported to Google, and the vulnerable workflow has been updated, which fixed it.
Trustifi’s Advanced threat protection prevents the widest spectrum of sophisticated attacks before they reach a user’s mailbox. Try Trustifi Free Threat Scan with Sophisticated AI-Powered Email Protection .
Bazel has been most widely used in multiple projects and has more than 21,000 stars on GitHub. Additionally, Bazel uses GitHub actions for testing and building new code, labeling issues, and running scheduled tasks.
Three actions interact with the build pipeline with custom actions.
- Docker actions: Runs inside a Docker container and configured using a Dockerfile or with an Image
- JS actions: Executes code and calls different functions while utilizing the GitHub actions toolkit to interact with the workflow.
- Composite actions: Combines multiple workflow steps within one action in which each step can invoke shell commands or call additional actions.
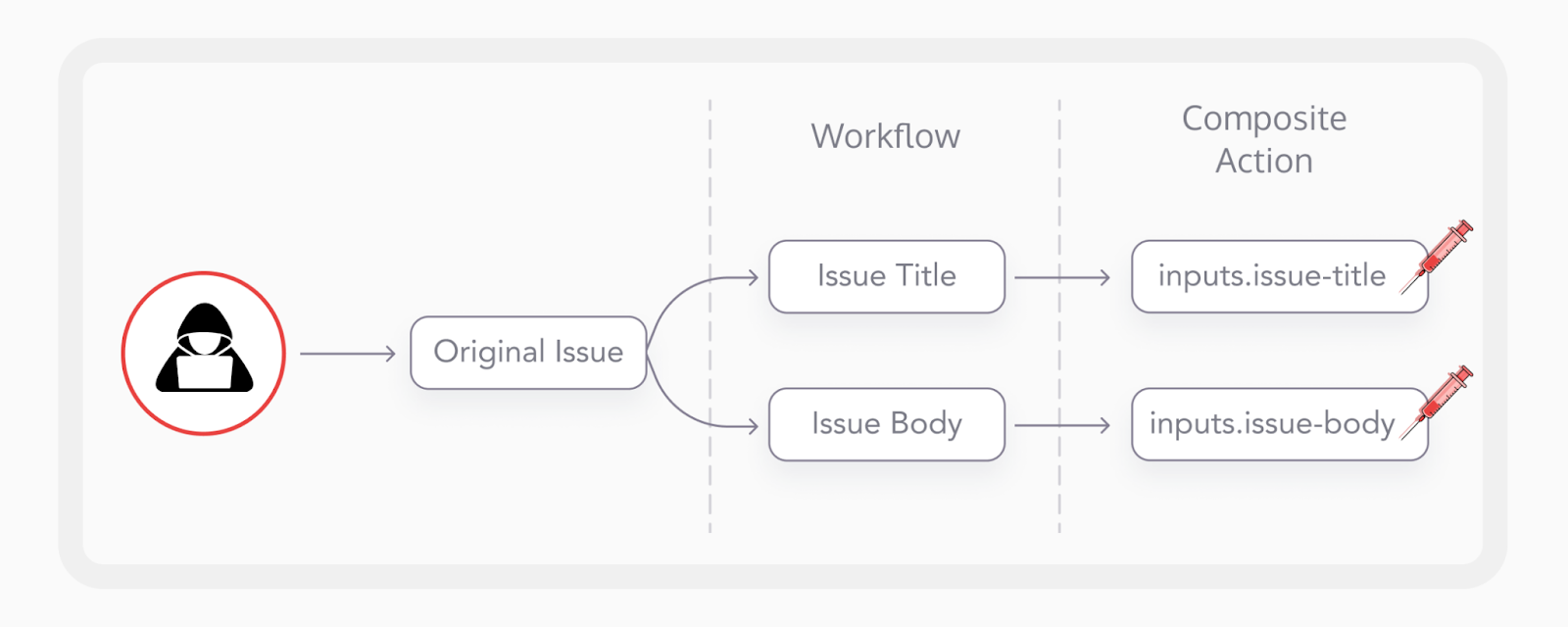
However, this supply chain vulnerability focussed on the abuse of composite actions.
To be more specific, the cherry-picker workflow, which can be dissected into three parts, was explored.
Part 1: Triggers and Permission
This workflow was granted with full Read/Write permissions, which runs whenever an issue is being closed/logged. This was due to the workflow permission setting that is configured in GitHub. Nevertheless, the default workflow permissions without any modifications provide complete access to the GITHUB_TOKEN.
Part 2: The Innocent Workflow
This part relies on the cherry-picker-on-milestoned job that gets executed whenever an issue is milestoned. However, when a valuable issue is raised and gets milestoned, it calls the composite actions located at the Bazel continuous integration repository.
Part 3: The Injectable Composite Action
This part of the workflow is abused with the Pass Inputs to Shell that passes the inputs directly into the inline bash script. If a shell command uses the $( ) characters, anything inside the brackets will be treated as a command and executed.
Part 4: Attack in Action
This part provides the complete flow of the attack. A threat actor can create a new issue with the malicious payload. When this issue is cloned, the cherry-picker workflow starts, and the malicious payload gets executed.
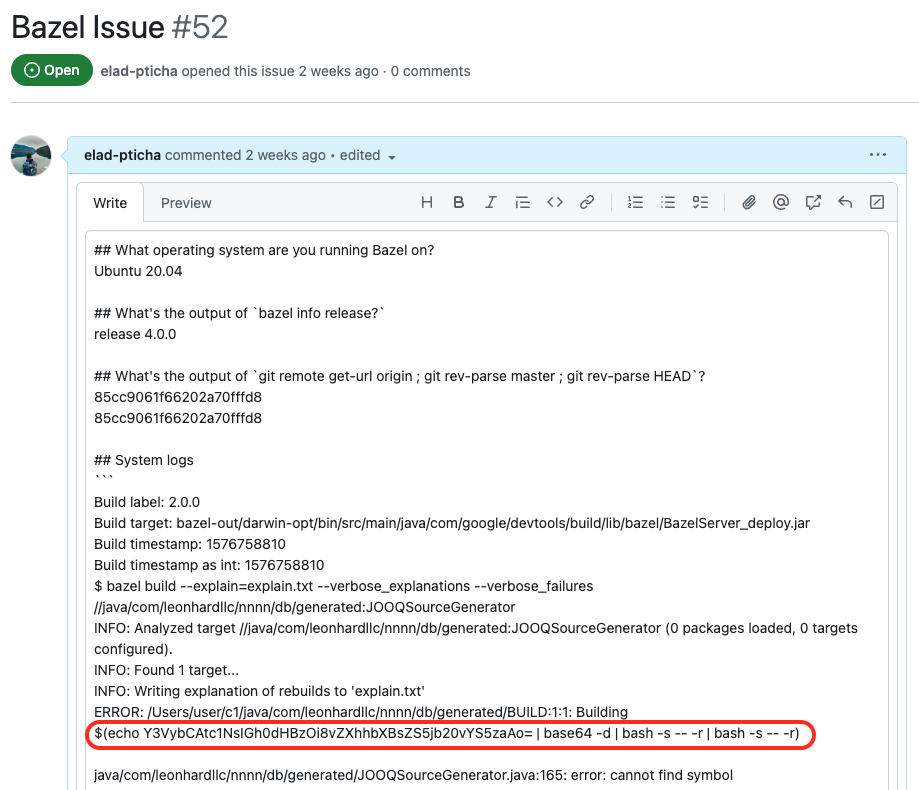
Cycode has published provides detailed information about the source code involved, Bazel repository details, workflow, and other information.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.
Read the full article here

