In recent years, Android users have been experiencing a rise in the incidence of the GodFather banking trojan, mainly targeting European users.
This GodFather android malware was discovered in March 2022 and was described as one of the notorious trojans by Cyble Research & Intelligence Labs (CRIL) actively targeting Android bank users all over the world.
There have been several samples of GodFather Android apps found recently that masquerade as MYT applications. MYT Müzik is the name of the application, which is written in Turkish.

Technical Analysis of Android Malware
Therefore, it appears that this application is targeted at Android users in Turkey who use Android devices. To evade detection by the anti-virus products, the samples analyzed for GodFather were encoded using custom and complex encryption techniques.

Analysts were able to detect that this application had been installed in a manner similar to another legitimate application, and this app disguised itself as MYT Music. There have been more than 10 million downloads of this app from the Google Play Store which is hosted on Google’s servers.
After it has been successfully installed on the victim’s device, the GodFather Android malware achieves the ability to steal the following sensitive data and perform illicit activities:-
- SMSs
- Basic device details
- Installed apps data
- Device’s phone number
- Manipulate the device screen by using the Remote Desktop
- Forward incoming calls from a victim’s device
- Inject banking links into the device’s browser
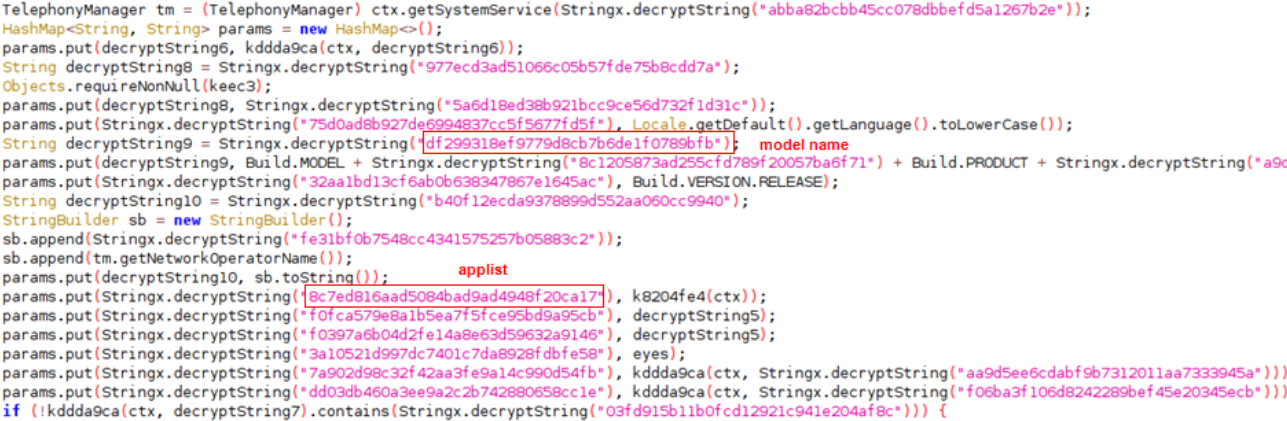
Here below we have mentioned the APK metadata:-
- App Name: MYT Müzik
- Package Name: com.expressvpn.vpn
- SHA256 Hash: 138551cd967622832f8a816ea1697a5d08ee66c379d32d8a6bd7fca9fdeaecc4
Permissions Requested
There are 23 different permissions that the malware requests from the user, and at least six of those permissions are abused by the malware.
Here is a list of these dangerous permissions:-
- READ_CONTACTS: Access phone contacts
- READ_PHONE_STATE: Allows access to phone state, including the current cellular network information, the phone number and the serial number of the phone, the status of any ongoing calls, and a list of any Phone Accounts registered on the device.
- CALL_PHONE: Allows an application to initiate a phone call without going through the Dialer user interface for the user to confirm the call.
- WRITE_EXTERNAL_STORAGE: Allows the app to write or delete files in the device’s external storage
- DISABLE_KEYGUARD: Allows the app to disable the keylock and any associated password security
- BIND_ACCESSIBILITY_SERVICE: Used for Accessibility Service
Using the code below, the malicious application hides and unhides the icon of the program from the display of the device.
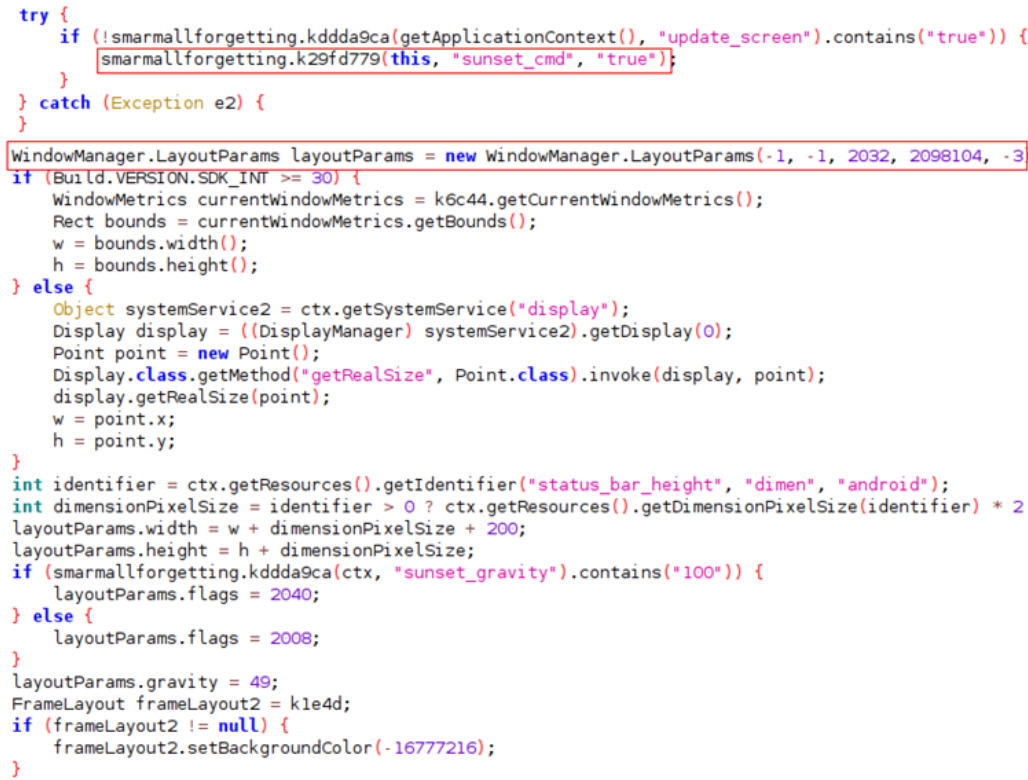
As soon as it receives sunset_cmd from the C&C server of the threat actors, the malware injects HTML phishing pages, and then in the OnAccessibilityEvent method, it constructs an overlay window.
It is from this telegram channel that the malicious application gets the URL of the C&C server:-
- hxxps://t[.]me/varezotukomirza
It uses this channel in order to communicate with the TAs so that it can receive commands and send the stolen data from the device through this channel.
Commands used by the Malware
In order to steal sensitive information from the users’ devices, the malware uses the below commands:-
- startUSSD
- sentSMS
- startApp
- startforward
- killbot
- send_all_permission
- vnc_open
- keylog_active
- unlock_screen
- sunset
- startscreen
Recommendations
Here below we have mentioned all the recommendations:-
- The only official app stores should be used for the download and installation of software.
- Make sure that all of your connected devices are protected by a reputable anti-virus and internet security program.
- Whenever possible, make sure that strong passwords are used and that multi-factor authentication is enforced.
- Make sure that the biometric security features are enabled.
- If you receive any links via SMS or email that are delivered to your phone, make sure that you do not open them without validating their authenticity.
- If your Android device is protected by Google Play Protect, ensure that it is enabled.
- Whenever you enable any permission, make sure you do so with caution.
- Make sure that the operating system, applications, and devices on your computer are up-to-date.
- Ensure that applications installed on mobile devices are in compliance with the amount of mobile/Wi-Fi data they use on a regular basis.
- Ensure that you stay on top of anti-virus notifications and Android OS alerts and take appropriate action when needed.
- Ensure that the Wi-Fi/Mobile data is turned off when they are not in use.
- You should make a backup of all the media files that you own.
- You should report any fraudulent transactions as soon as possible to your bank in case there is a problem.
- In order to prevent malware attacks in the future, banks and other financial institutions need to educate their customers on how to protect themselves via telephone, SMS, or email.
Penetration Testing As a Service – Download Red Team & Blue Team Workspace
Read the full article here

