In today’s digital era, AI (Artificial Intelligence) and ML (Machine Learning) applications are one of the key developments.
But, with global initiatives like the EU AI Act and U.S. AI Strategy highlight the importance of ethical AI regulation, especially in cybersecurity.
A report shared with Cyber Security News by a group of cybersecurity analysts consisting of Jose L. Hernandez-Ramos, Georgios Karopoulos, Efstratios Chatzoglou, Vasileios Kouliaridis, Enrique Marmol, Aurora Gonzalez-Vidal, and Georgios Kambourakis, revealed the latest development in the cybersecurity field, which is the decentralized learning approach known as “Federated Learning (FL).”
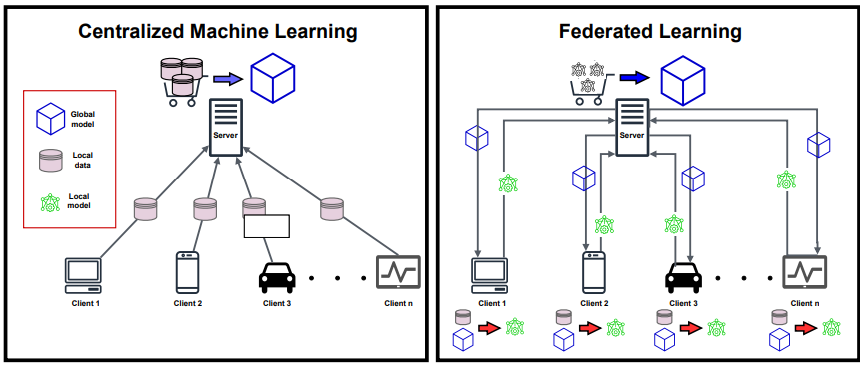
Under this decentralized approach, the ML models are built without sharing the end nodes’ data by utilizing a certain aggregation.
Federated Learning-Based IDS
For the development of systems and applications based on Machine Learning, this decentralized approach is very important, and not only that, but even this new approach also helps secure the privacy of end users.

So, it seems that the complete mechanism of this new approach, Federated Learning (FL), is comprehensive and advanced in nature, as the security systems can use this approach for better protection and defense mechanisms.
The IDS (Intrusion Detection System) detects the threats in IT/OT systems, and the FL-based IDS growth links to accurate evaluation datasets.
Besides this, the initial evolution of IDSs was mainly focused on the approaches that are signature-based, but the recent combination of IDS with an FL-based approach seems promising and far more efficient than the previous approaches.
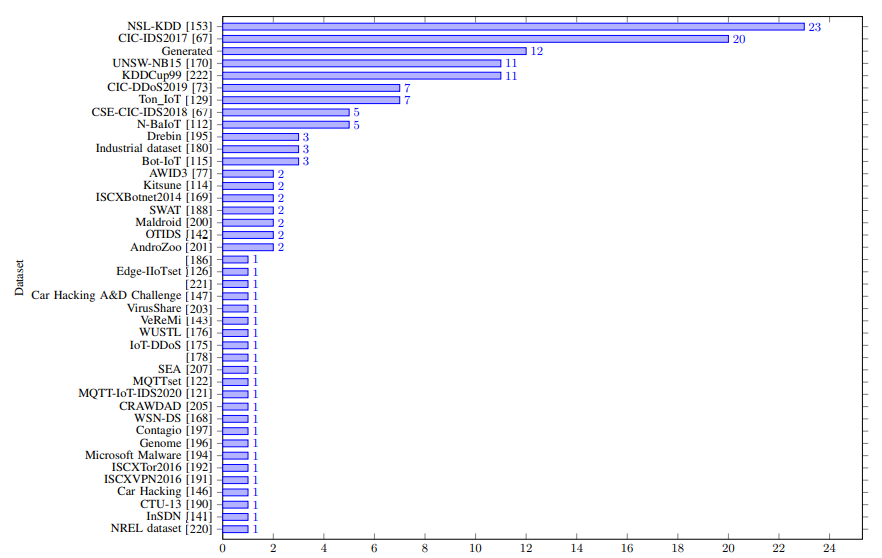
Here below, we have mentioned all the datasets:-
- CIC-IDS2017
- CSE-CIC-IDS2018
- CIDDS-001
- CIDDS-002
- CIC DoS
- PUF
- TRAbID
- Unified host and network
- N-BaIoT
- Kitsune
- Bot-IoT
- AWID3
- WUSTL-IIoT
- H23Q
- IoT network intrusion dataset
- IoTID20
- IoT-23
- IoT Healthcare Security Dataset
- e IoT DoS and DDoS Attack Dataset
- CCD-INID-V1
- X-IIoTID
- Edge-IIoTset
- MQTT-IoT-IDS2020
- MQTTset
- LATAM-DDoS-IoT dataset
- UAV Attack Dataset
- CIC IoT dataset
- Intrusion Detection in CAN bus
- Ton IoT dataset
- Car Hacking
- MedBIoT
- Car Hacking: Attack & Defense Challenge
- InSDN
- OTIDS
- Vehicular Reference Misbehavior Dataset (VeReMi)
In this scenario, the neural networks (NNs) used in IDS match the two key elements, and here below, we have mentioned them:-
Moreover, the RL (Reinforcement Learning), an ML branch, has agents learn to maximize rewards through trial and error. While it categorizes into the following methods:-
- Value-based
- Policy-based
- Model-based
Challenges Faced
Here below, we have mentioned all the challenges and future trends for FL-enabled IDS approaches:-
- Security
- Privacy
- Aggregator as bottleneck
- Data heterogeneity
- Device heterogeneity
- Computation requirements
- Communication requirements
The growth of FL in IDS is clearly notable and skyrocketed rapidly due to its following key features:-
- Decentralized
- Collaborative
- Privacy-protection
Overall, it’s been concluded that this new decentralized approach could be game-changing in the field of cybersecurity.
Keep informed about the latest Cyber Security News by following us on GoogleNews, Linkedin, Twitter, and Facebook.
Read the full article here