Fortra-owned GoAnywhere MFT (Managed File Transfer) has been discovered with a new vulnerability that could allow an unauthorized threat actor to create an admin user via the administration panel. This vulnerability has been assigned with CVE-2024-0204, and the severity has been given as 9.8 (Critical).
However, Fortra has released a security advisory for addressing this vulnerability, which mentions that the affected products were Fortra GoAnywhere MFT 6.x from 6.0.1 and Fortra GoAnywhere MFT 7.x before 7.4.1. In addition, this vulnerability was identified as an authentication bypass vulnerability.
Open Suspicious Files & Links in the ANY RUN Sandbox Safely; Try All Features for Free. Understand malware behavior, collect IOCs, and easily map malicious actions to TTPs — all in our interactive sandbox.
GoAnywhere MFT Auth Bypass
According to the reports shared with Cyber Security News, researchers have been working on recreating this vulnerability, and a proof-of-concept has been published on GitHub.
As per Fortra’s security advisory, the endpoint was stated as /InitialAccountSetup.xhtml, which can be deleted, and the service has to be restarted to mitigate the issue.
Further analyzing through the application directories, this endpoint was found to be mapped with the com.linoma.ga.ui.admin.users.InitialAccountSetupForm inside the GoAnywhere/adminroot/WEB-INF/forms-faces.xml file.
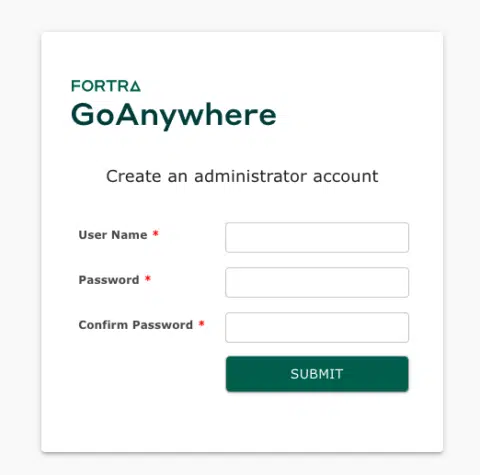
As of the GoAnywhere MFT installation, the initial setup takes the users to create a new administrative user at the endpoint /InitialAccountSetup.xhtml. However, after the administrative user has been created, this endpoint will no longer be available or accessible.
Instead, the users are directed to the /Dashboard.xhtml endpoint, followed by the /auth/Login.xhtml if the user is not authenticated.
The Authentication Bypass
As per the source code, there was another class named com.linoma.dpa.security.SecurityFilter, which performs the doFilter() function to check which endpoint is requested. Based on the endpoints, user context, and application settings, it allows the requests to be routed to the correct endpoint.
However, this SecurityFilter class has two explicit places that are vulnerable and bypassed for requesting the /InitialAccountSetup.xhtml endpoint. One was on Line 91, which is specified for two criteria, such as checking if an admin user is created and the requested path is not /wizard/InitialAccountSetup.xhtml. If these two checks are passed, it redirects to the setup page.
The second vulnerable place was on Line 102, which also had two criteria, such as checking if there is an admin user created already, and the requested path is /wizard/InitialAccountSetup.xhtml. Passing these two checks, the users will be redirected to the /Dashboard.xhtml page.
The Exploitation
So as to exploit, the researchers used logic and a path traversal code with the payload /..;/ that landed them on the setup page.
Once this page is displayed, the researchers were able to create an admin user again by submitting the request along with the path traversal payload.
Furthermore, a complete report about this exploitation has been published by Horizon3, providing detailed information about the source code, exploitation, and other information.
Indicators of Compromise
One of the easiest ways to check for exploitation is to check for any new administrative users created on the interface in the Admin Users group inside the administrator portal Users–> Admin Users section.
Additionally, the database logs can also be found in the GoAnywhereuserdatadatabasegoanywherelog*.log file, which contains the history of transactions, including adding and creating entries for users.
Read the full article here

