Password spraying is a technique hackers often take advantage of because it enables them to gain unauthorized access to many accounts or systems. They can potentially compromise many targets with little difficulty by using the same passwords for several accounts.
It is a low-risk and high-reward attack method that the threat actors use while trying to get into networks or steal private information as password spraying defeats account lockout mechanisms.
Recently, cybersecurity researchers at Cisco warned of password-spraying attacks that are actively targeting VPN services.
Password Spraying Attacks Exploiting VPN Services
Cisco acknowledged reports of password spraying attacks targeting RAVPN services, including its own products and third-party VPN concentrators, as noted by Talos.
Download Free CISO’s Guide to Avoiding the Next Breach
Are you from The Team of SOC, Network Security, or Security Manager or CSO? Download Perimeter’s Guide to how cloud-based, converged network security improves security and reduces TCO.
- Understand the importance of a zero trust strategy
- Complete Network security Checklist
- See why relying on a legacy VPN is no longer a viable security strategy
- Get suggestions on how to present the move to a cloud-based network security solution
- Explore the advantages of converged network security over legacy approaches
- Discover the tools and technologies that maximize network security
Adapt to the changing threat landscape effortlessly with Perimeter 81’s cloud-based, unified network security platform.
The attacks can lock accounts, leading to DoS-like conditions, depending on the environment. While this activity seems related to reconnaissance efforts.
Since VPNs provide remote access to internal networks, which makes them attractive targets for gaining unauthorized entry. Password spraying allows hackers to test many common passwords across numerous accounts without triggering account lockouts.
Successful VPN compromise can grant access to sensitive data and systems within the organization’s network. Threat actors can leverage compromised VPN accounts for further lateral movement and escalation of privileges within the breached environment.
VPN services often employ weak or reused passwords, increasing the chances of success for password spraying attacks.
Recommendations
Here below we have mentioned all the recommendations offered by the cybersecurity analysts at Cisco:-
- Enable Logging
- Secure Default Remote Access VPN Profiles
- Leverage TCP shun
- Configure Control-plance ACL
- Use Certificate-based authentication for RAVPN
IoCs
- Unable to establish VPN connections with Cisco Secure Client (AnyConnect) when Firewall Posture (HostScan) is enabled
Users attempting VPN connections with Cisco Secure Client encounter an error about Cisco Secure Desktop not being installed and this prevents the successful connections.
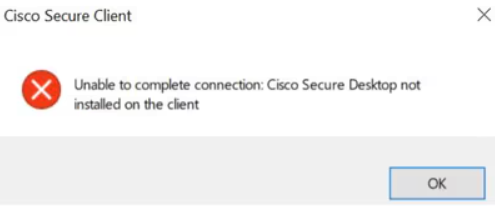
Cisco secure client (Source – Cisco)
This symptom seems a side effect of the DoS-like attacks but further investigation still continues.
- Unusual Amount of Authentication Requests
The Cisco ASA or FTD VPN headends exhibit the symptoms of password spraying, with millions of rejected authentication attempts visible in the “syslogs.”
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.
Read the full article here

