Threat actors of Iranian origin, CharmingCypress (also known as Charming Kitten, APT42, TA453), have gathered political intelligence against international targets, with a special emphasis on journalists, think tanks, and NGOs.
CharmingCypress frequently uses novel social-engineering techniques in its phishing efforts, like emailing people and holding long-lasting discussions before delivering links to malicious content.
Recently, malware-laden VPN applications were utilized to install backdoors and limit access to fake webinar platforms.
“CharmingCypress went so far as to craft an entirely fake webinar platform to use as part of the lure. It controlled access to this platform, requiring targets to install malware-laden VPN applications before granting access”, Volexity shared Cyber Security News.
Live attack simulation Webinar demonstrates various ways in which account takeover can happen and practices to protect your websites and APIs against ATO attacks
.
Using Malware-Laden VPN Application to Deploy Malware
The latest CharmingCypress spear-phishing effort was built on a method that used a VPN application infected with malware to spread malware, as revealed by Proofpoint in July 2023.
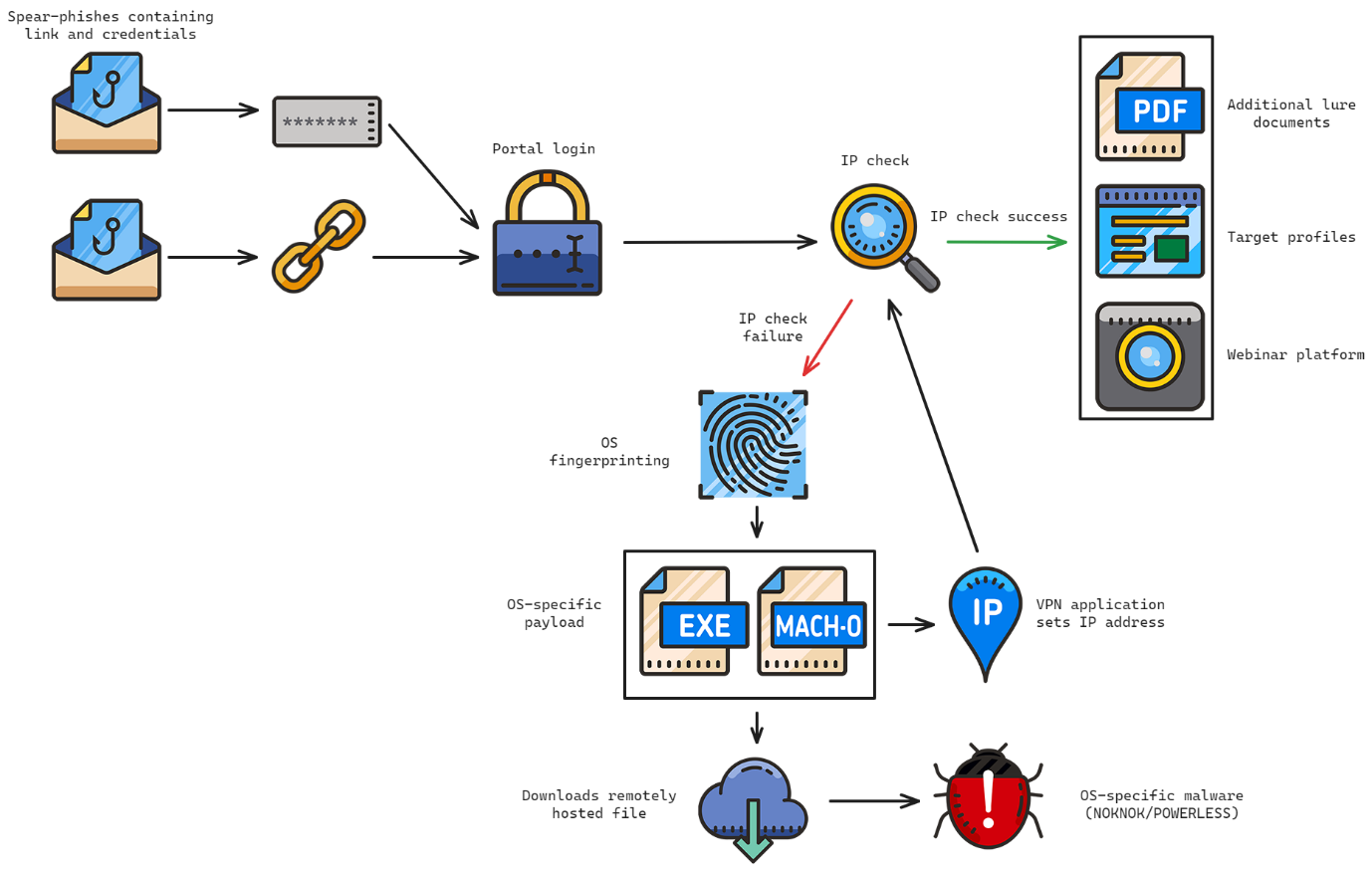
A small group of targeted individuals received emails with links to a fraudulent webinar platform and login credentials. The portal would validate the IP address and credentials used to access the website.
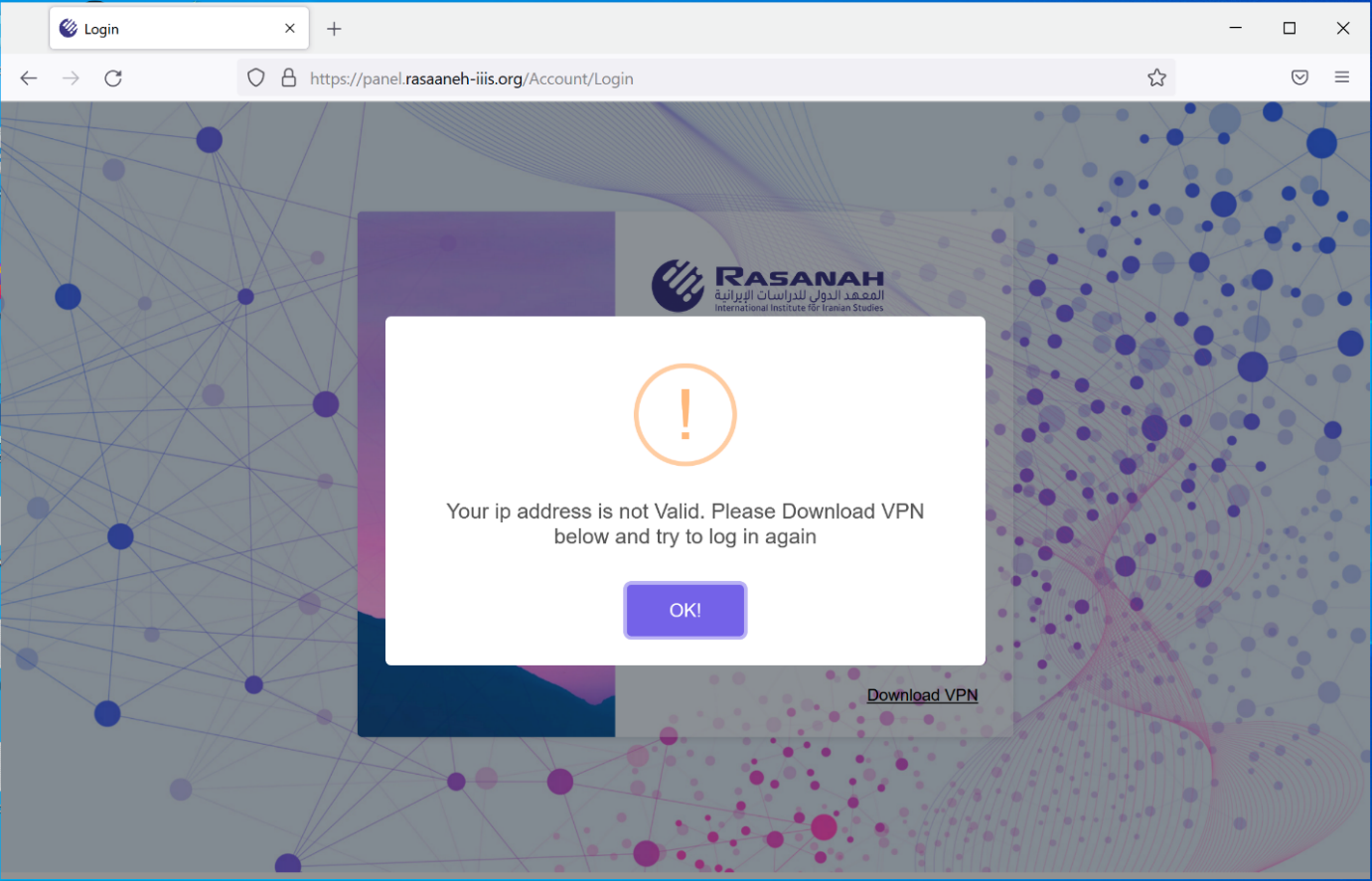
Only those utilizing the VPN client of the attacker would be able to authenticate successfully. The targets were prompted to download a VPN application if the IP address check was unsuccessful.
A user would be provided with various applications based on their operating system. The end product was a VPN client that functioned but was infected with malware. An infection chain ending in POWERLESS would be offered to Windows victims, whereas an infection chain ending in NOKNOK would be served to macOS victims.
The Windows VPN application uses the provided credentials and an OpenVPN configuration file to connect to a VPN endpoint that is operated by CharmingCypress.
“Attempting to log on to the portal while connected to the VPN successfully passes the IP address check and allows access to the fake webinar portal,” researchers said.
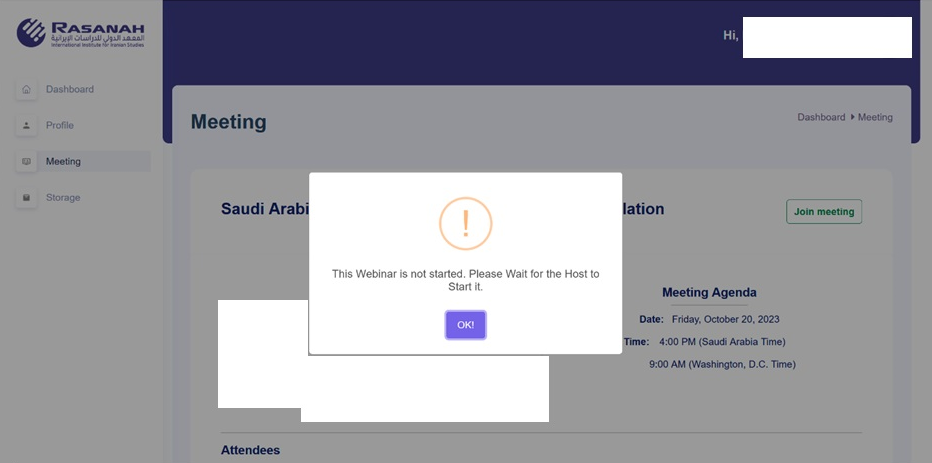
“Within the portal, profiles of 16 individuals were populated and associated with a specific webinar. All 16 individuals are experts in policy regarding the Middle east”, researchers said.
This campaign discusses comparable tactics reported in a January Microsoft post.
Volexity has noted the following malware families: POWERSTAR, POWERLESS, NOKNOK, BASICSTAR, and EYEGLASS throughout 2023 and into early 2024.
POWERSTAR uses spear-phishing techniques to deploy malware. POWERLESS is the backdoor used by the malware-laden VPN application infection chain’s Windows version, and NOKNOK is used on macOS. BASICSTAR is utilized by the RAR + LNK infection.
EYEGLASS had been set up as the default handler for the TIF file extension. In this case, it was intended only as a backup C2 mechanism.
CharmingCypress employs additional tools to aid in data theft, such as Nirsoft Chrome History Viewer, RATHOLE, SNAILPROXY, CommandCam, and Command-line copies of WinRAR and 7-Zip.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.
Read the full article here

