As the holy month of Ramadan approaches, bringing a surge in online shopping and charitable giving, cybercriminals are ramping up their efforts to exploit the festive spirit.
A recent study by Security has highlighted an increase in fraudulent activities targeting consumers in the Middle East, particularly in the Kingdom of Saudi Arabia (KSA), where consumer spending has topped $16 billion.
This article delves into the sophisticated tactics these cyber criminals employ and offers advice on staying safe online.
The Rise of Cyber Fraud During Festive Seasons
During Ramadan and Eid Fitr, there’s a notable spike in retail and online transactions. Unfortunately, this increase in activity also attracts cybercriminals looking to exploit the situation.
Free Webinar : Mitigating Vulnerability & 0-day Threats
Alert Fatigue that helps no one as security teams need to triage 100s of vulnerabilities.
:
- The problem of vulnerability fatigue today
- Difference between CVSS-specific vulnerability vs risk-based vulnerability
- Evaluating vulnerabilities based on the business impact/risk
- Automation to reduce alert fatigue and enhance security posture significantly
AcuRisQ, which helps you to quantify risk accurately:
Resecurity’s findings indicate that the financial impact of these fraudulent activities ranges between $70 and $100 million, affecting expatriates, residents, and foreign visitors alike.
Sophisticated Scams Targeting Consumers
Cybercriminals are employing increasingly complex methods to defraud individuals.
These include the “Smishing Triad,” a tactic previously identified by Resecurity, which has been used to target consumers not only in the Middle East but also in the U.S., U.K., various European Union countries, and the UAE.
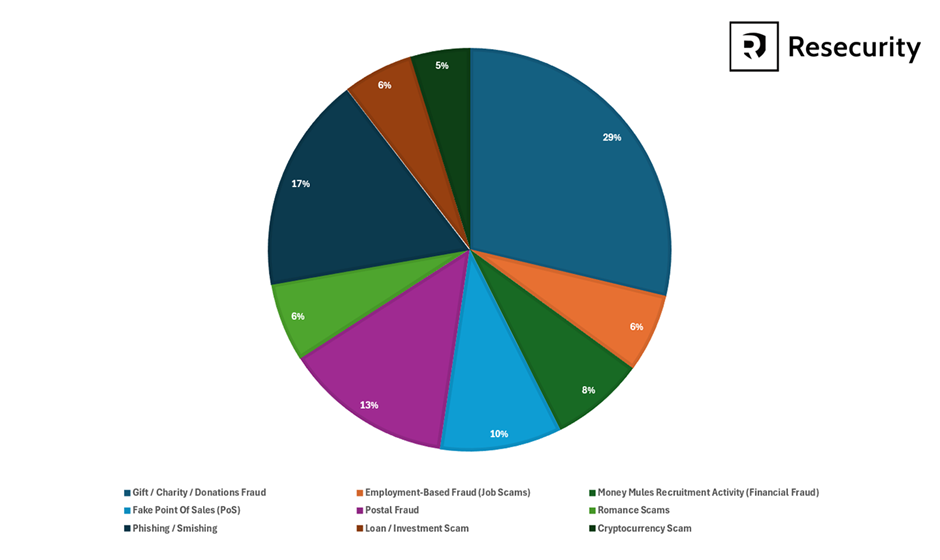
The most common types of fraudulent activities observed include:
- Gift/charity/donations fraud
- Employment-based fraud (job scams)
- Money mules recruitment activity (financial fraud)
- Fake point of sales (PoS)
- Impersonation of logistics and postal providers
- Romance scams/blackmail
- Phishing/smishing activity
- Loan/investment fraud
- Cryptocurrency scams
Impersonation of Trusted Logistics Providers
A rising trend in scams involves bogus notifications from reputable shipping companies like Aramex, SMSA Express, and Zajil Express.
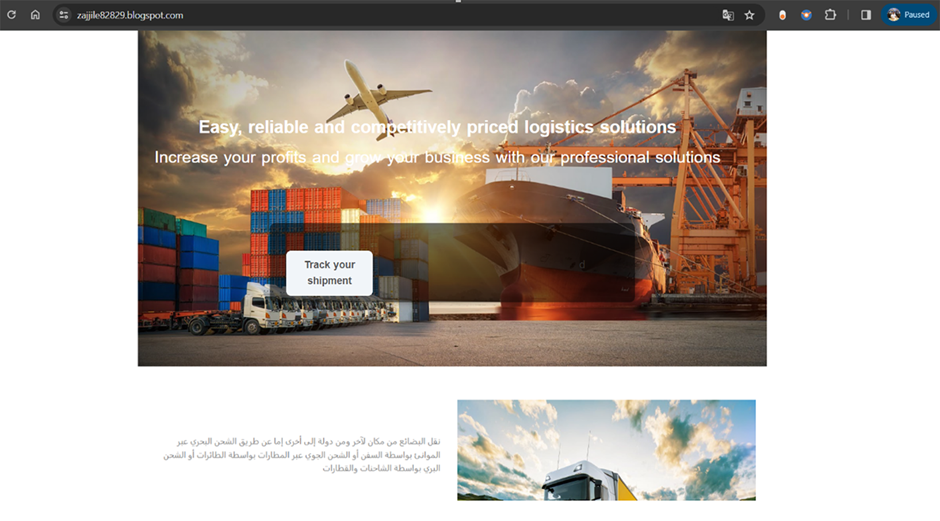
These messages falsely claim that a parcel delivery is pending due to unpaid fees, urging recipients to make immediate payments.
This method tricks individuals into believing they owe money for a delivery, prompting a quick response.
Abuse of SADAD and MUSANED Platforms
Cybercriminals have also targeted the SADAD and MUSANED platforms, creating fake websites to intercept two-factor authentication (2FA) or one-time passcode (OTP) codes.
This sophisticated phishing approach aims to bypass security measures and gain unauthorized access to victims’ accounts.
- Original SADAD website: https://www.sadad.com/
- Phishing SADAD website: https://sadad14c.softr.app/
- Original Musaned website: https://musaned.com.sa/home
- Phishing Musaned website: https://musaned2comsa3.softr.app/
Money Mules Recruitment Via Ajeer and Rental Scams Via Ejar Platform
Fraudsters are exploiting platforms like Ajeer and Ejar to offer non-existing jobs and properties, respectively.
These scams not only aim to profit from illicit activity but also to exploit workers and renters illegally.
- Original Ajeer website: https://ajeer.qiwa.sa/
- Phishing Ajeer website: https://sites.google.com/view/iger-1
- Original Ejar website: https://www.ejar.sa/
- Phishing Ejar website: https://ejar-sa-ar.netlify.app
With over 320 fraudulent sites and platforms blocked by Resecurity in the Middle East, it’s clear that cybercriminals are aggressively exploiting trusted platforms to deceive internet users.
Consumers are strongly advised to refrain from sharing personal and payment information on questionable sites or with individuals posing as bank or government employees.
Reporting suspicious resources to local law enforcement and designated contacts in these organizations is crucial in helping to prevent potential fraud risks.
As we navigate the festive season, staying informed and vigilant is our best defense against these sophisticated online scams.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.
Read the full article here