Apple users are falling prey to a sophisticated phishing campaign designed to hijack their Apple IDs through what’s known as a “push bombing” or “MFA fatigue” attack.
This method exploits the multi-factor authentication (MFA) system, bombarding users with incessant notifications to approve password changes or logins, ultimately aiming to steal passwords and gain unauthorized access to personal information and devices.
The Mechanics of the Attack
Entrepreneur Parth Patel recently became a target of this phishing scheme, experiencing firsthand the relentless flood of system notifications across all his Apple devices, urging him to approve a password reset.
This deluge of prompts is not just annoying but strategically designed to wear down the victim’s resistance or catch them off guard, leading to an accidental approval of the malicious request.
Adding a layer of sophistication to the attack, phishers follow up with phone calls masquerading as Apple Support, using caller ID spoofing to display Apple’s legitimate customer support number.
In Patel’s case, the caller provided accurate personal information, except for his real name, sourced from a people-search website known for inaccurately listing personal details.
This tactic lends credibility to the phishing attempt and aims to manipulate victims into providing a one-time password sent to their device, enabling attackers to reset the Apple ID password and lock out the user.
Krebs on Security, a well-known security blog, recently reported a series of attacks targeting Apple users, known as “MFA Bombing.”
The Role of the Phone Number
The experience shared by Chris, a cryptocurrency hedge fund owner, underscores the critical role of the phone number associated with the Apple account in these attacks.
Despite changing his passwords and even purchasing a new iPhone, Chris continued to receive the same system alerts, suggesting that the attackers exploit a vulnerability linked to the phone number on file for the Apple account.
Cybersecurity enthusiast Orbs recently tweeted about the surge of “Push Bombing” attacks being targeted towards Apple users by hackers and scammers.
A Persistent Threat
Security industry veteran Ken also received these unsolicited system alerts, which not only disrupted his peace but also raised concerns about the potential for accidental approval of malicious requests.
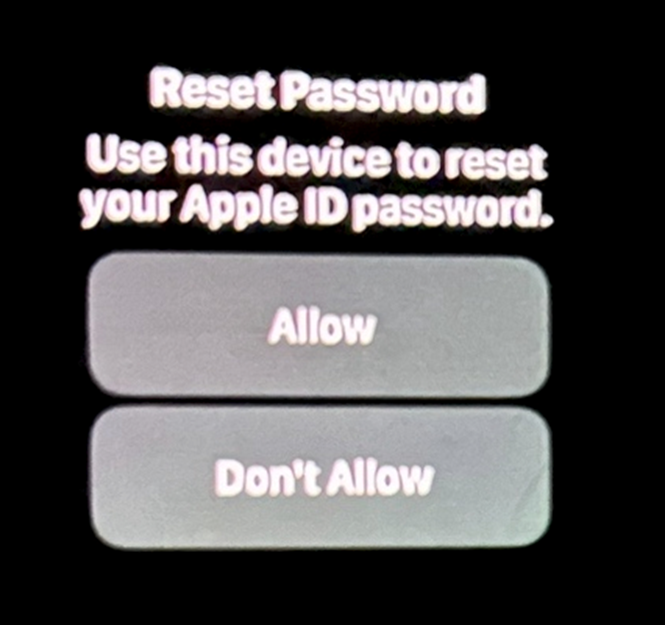
Despite taking preventive measures recommended by Apple, such as enabling a recovery key for his account, Ken found that the alerts persisted, indicating a more profound issue within Apple’s system that allows these password reset prompts to bypass security enhancements.
Apple’s Response and the Need for Enhanced Security Measures
Apple has not publicly addressed this specific phishing campaign or the apparent vulnerability in its system that allows for such “push bombing” attacks.
This situation echoes past incidents in which Apple had to implement stricter rate limiting to curb similar exploits, suggesting that the tech giant needs to reassess and fortify its authentication and notification systems against evolving phishing tactics.
The rise of “push bombing” attacks targeting Apple users highlights a growing challenge in digital security, where even robust multi-factor authentication systems can be exploited by determined attackers.
This campaign underscores the importance of vigilance among users and the need for tech companies to continuously evolve their security measures to protect against sophisticated phishing techniques.
As the digital landscape becomes increasingly fraught with threats, users and tech giants must stay one step ahead to safeguard personal information and digital lives.
This report draws attention to a critical and emerging threat in digital security, urging both users and corporations to reassess and strengthen their defenses against sophisticated phishing attacks.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.
Read the full article here

