In the ever-evolving landscape of cybersecurity, the need for advanced tools to simulate and test incident response is critical.
AttackGen, a cutting-edge incident response testing tool, has emerged as a game-changer in this domain.
Leveraging the power of large language models and the comprehensive MITRE ATT&CK framework, AttackGen offers a unique approach to preparing organizations against sophisticated cyber threats.
Developed by Matthew Adams, a security architect at Santander UK, AttackGen is designed to generate tailored incident response scenarios.
These scenarios are based on user-selected threat actor groups and are customized to an organization’s specific size and industry.
This level of personalization ensures that the scenarios are relevant and challenging, providing a realistic training environment for security teams.
Free Webinar : Mitigating Vulnerability & 0-day Threats
Alert Fatigue that helps no one as security teams need to triage 100s of vulnerabilities.
:
- The problem of vulnerability fatigue today
- Difference between CVSS-specific vulnerability vs risk-based vulnerability
- Evaluating vulnerabilities based on the business impact/risk
- Automation to reduce alert fatigue and enhance security posture significantly
AcuRisQ, that helps you to quantify risk accurately:
The tool’s integration with the MITRE ATT&CK framework allows users to create scenarios that focus on particular segments of the cyber kill chain or specific tactics like ‘Lateral Movement’ or ‘Exfiltration’.
This feature is particularly beneficial for mature organizations with advanced threat intelligence capabilities, enabling them to test their defenses against the latest techniques used by threat actors they are monitoring.
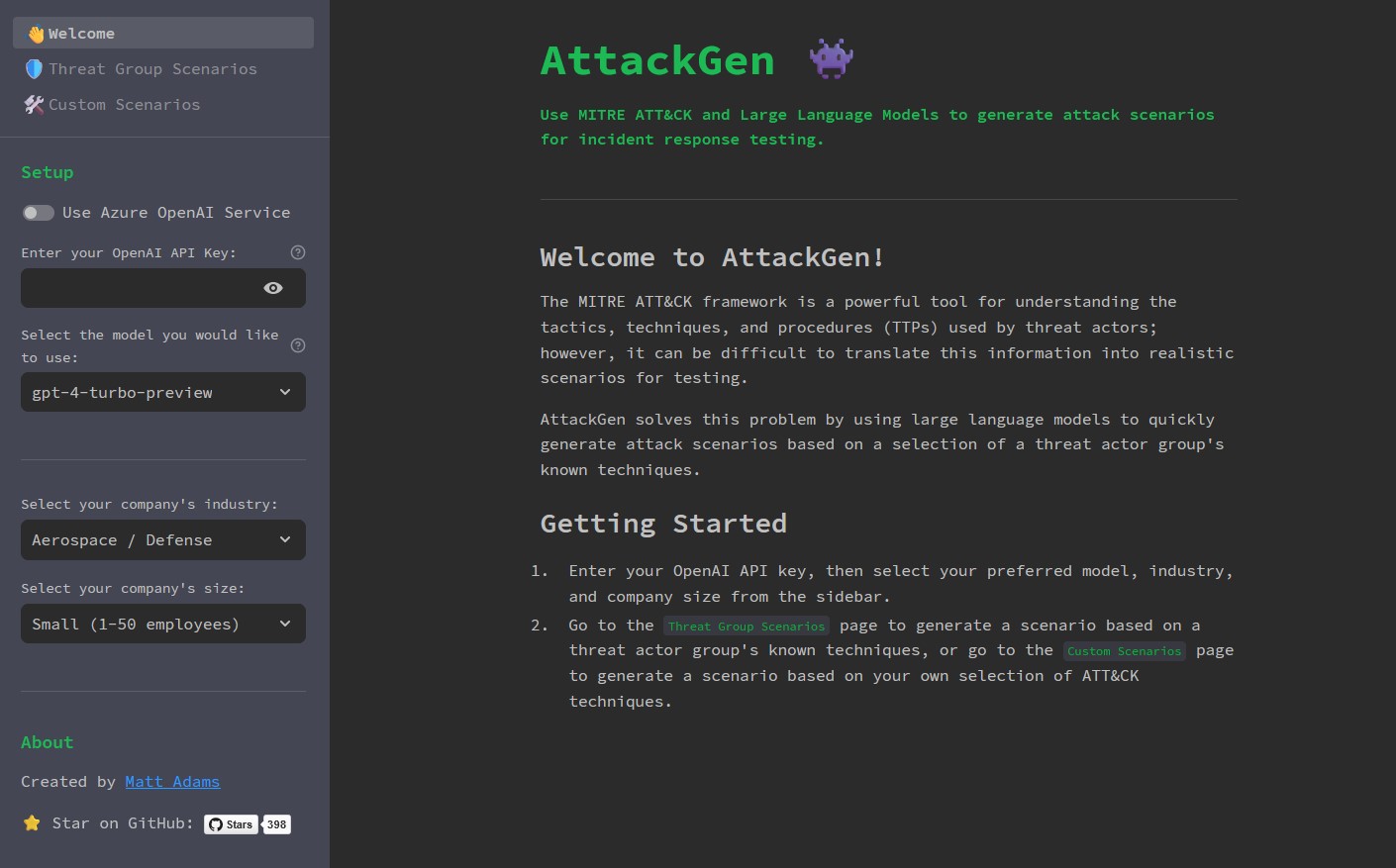
AttackGen’s latest version, v0.2, introduces several new features, including the ability to generate custom scenarios based on ATT&CK techniques and a user feedback mechanism to gain insights into model performance over time.
The improved error handling and user interface enhances the overall user experience, making it easier for teams to navigate and utilize the tool effectively.
One of the standout features of AttackGen is its flexibility. Users can choose to use either the OpenAI API or Azure OpenAI Service to generate incident response scenarios.
This choice allows organizations to select the most suitable model for their specific use case and ensures that application descriptions and other data remain within a secure environment, which is crucial for handling sensitive information.
The tool is also integrated with LangSmith, a powerful debugging, testing, and monitoring tool for model performance.
LangSmith captures user feedback on the quality of scenarios generated, providing valuable insights into model performance and user satisfaction.
AttackGen is available as a Docker container image, simplifying deployment and running the application in a consistent and reproducible environment.
This ease of deployment is particularly useful for users who want to run AttackGen in a containerized environment or deploy the application on a cloud platform.
As cyber threats continue to grow in complexity and frequency, tools like AttackGen are essential for organizations to stay ahead of attackers.
By providing a platform for rigorous testing and scenario-based training, AttackGen helps security teams sharpen their skills and improve their incident response capabilities, ultimately strengthening their cybersecurity posture.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.
Read the full article here

