Kubernetes container scanners check containers for security vulnerabilities, misconfigurations, and compliance concerns. These scanners are essential to containerized applications and Kubernetes infrastructure security.
It provides two facilities: automation and declarative configuration. It can set the web server as per web traffic and maintain the level during production.
How Does Kubernetes Container Scanner Work?
Before you read this topic, you may be wondering what Kubernetes is. Let us tell you that it is an extensible, portable, and open-source platform that manages containerized workloads and services.
Usually, the web server hardware is located in several data centers, where Kubernetes makes up the scale and serves according to the demand.
It also has an advanced load-balancing capability, which helps control the web traffic routing and web server.
Now you know about Kubernetes, but you might wonder about its security.
Nowadays, Kubernetes is one of the best container orchestration platforms, and more than 80% of organizations are using it in some way. It automates provisioning configuration and manages the containers.
Though it is very simple, security also matters for any containerized application. You may know how to provide robust protection for the application running on the Kubernetes cluster.
Now you know about basic Kubernetes, which works by default. It assigns the IP address to the port in the cluster and provides basic security.
Sometimes, third-party open-source Kubernetes scanners can help to secure the Kubernetes cluster.
Here we will discuss a few Kubernetes Container Scanner tools that can help find security vulnerabilities and misconfigurations and provide the best security.
In this article, we detail the top 10 Kubernetes container scanners.
Table of Contents
Top 10 Kubernetes Container Scanner
Kubernetes Container Scanner Features
1. Kube Hunter
2. Kube Bench
3. Checkov
4. Anchore
5. Kubeaudit
6. Clair
7. Kubei
8. Kubesec
9. Kube Scan
10. MKIT
Kubernetes Container Scanner Features
| Kubernetes Container Scanner | Features |
|---|---|
| 1. Kube Hunter | 1. Scanning 2. Attack Vectors 3. CVE Detection 4. Privilege Escalation |
| 2. Kube Bench | 1. Benchmarking 2. CIS Compliance 3. Security Checks 4. Automated Scanning |
| 3. Checkov | 1. Infrastructure as Code (IaC) Security 2. Configuration Scanning 3. Cloud Platform Support 4. Policy Checks |
| 4. Anchore | 1. Container Image Scanning 2. Vulnerability Detection 3. CVE Analysis 4. Configuration Assessment |
| 5. Kubeaudit | 1. Kubernetes Security Audit 2. Configuration Assessment 3. Manifest Scanning 4. Best Practices Checks |
| 6. Clair | 1. Container Vulnerability Scanning 2. Image Analysis 3. CVE Detection 4. Risk Assessment |
| 7. Kubei | 1. Kubernetes Runtime Vulnerability Scanning 2. Image Scanning 3. Risk Assessment 4. Security Audit |
| 8. Kubesec | 1. Kubernetes Security Analysis 2. Manifest Scanning 3. Security Controls Evaluation 4. Risk Assessment |
| 9. Kube Scan | 1. Kubernetes Security Scanning 2. Vulnerability Assessment 3. Misconfiguration Detection 4. CIS Benchmark Checks |
| 10. MKIT | 1. Kubernetes Security Assessment 2. Cluster Configuration Analysis 3. Vulnerability Scanning 4. Risk Identification |
10 Best Kubernetes Container Scanners 2024
- Kube Hunter
- Kube Bench
- Checkov
- Anchore
- Kube audit
- Clair
- kubei
- Kubesec
- Kubescan
- MKIT
1. Kube Hunter
This Aqua Security tool is a Kubernetes cluster vulnerability scanner.
Kube-hunter is an open-source Kubernetes security tool. It simulates assaults to find Kubernetes cluster security vulnerabilities.
Kube-hunter, a Kubernetes penetration testing tool, identifies vulnerabilities and misconfigurations that attackers might exploit.
This resource is useful for promoting safer online behavior. It searches for configuration, network, and other vulnerabilities that attackers might exploit.
Optional, standardized scans include network interleaving, remote, and vulnerability identification.
The binary zip file can be downloaded and extracted in a number of ways using the available tools.
Kube Hunter must be installed immediately to ensure the system has sufficient network access.
The cluster is now ready to begin vulnerability scanning. Kube Hunter may be run inside a Docker image.
You can scan the clusters immediately after installing it directly on the machine via the local network.
The active and passive tests for determining where in the cluster vulnerabilities lie are provided here.
Features
- Finds frequent Kubernetes cluster configuration issues that might compromise security.
- Finds API server, kubelet, and other Kubernetes security issues.
- Simulates attacks to test cluster resilience and uncover vulnerabilities.
- Checks the cluster’s compliance with corporate security best practices and CIS standards.
| What is Good ? | What Could Be Better ? |
|---|---|
| Vulnerability Detection | Needs to be done by hand |
| Open Source | Not enough tracking in real time |
| Active Development | |
| Easy to Use |
Demo video
Price
You can get a free trial and personalized demo from here…
Kube Hunter
2. Kube Bench
The CIS Security Benchmark must be met for your deployment to pass the inspection of this open-source quality security tool.
Aqua Security created Kube-bench to verify Kubernetes cluster security setup. It helps administrators and businesses verify Kubernetes deployments satisfy security best practices and benchmarks.
Furthermore, it finds the mistakes and provides assistance in correcting them. One aspect of the job is coming up with solutions.
The correct permission and authentication of data is also guaranteed by this instrument. It also guarantees deployment, which is essential for CIS leaders.
You should complete the application by entering the required information.
The YAML definition format is required for all tests and allows for simple updates and additions.
Features
- Compare CIS Kubernetes Benchmark to Kubernetes security settings.
- checks for vulnerabilities and improper configurations against CIS Kubernetes Benchmark recommended practices.
- You may test groups running different Kubernetes versions.
- Automated scanning makes frequent security tests and cluster protection easier.
| What is Good ? | What could Be Better ? |
|---|---|
| Security Best Practices | Few options for reporting and logging |
| Comprehensive Security Checks | No ways to send alerts |
| CIS Kubernetes Benchmark Checks | |
| Automated Scanning |
Demo video
Price
You can get a free trial and personalized demo from here…
Kube Bench
3. Checkov
.webp.jpeg)
It’s another Kubernetes Container Scanner tool for avoiding mistakes in code during development (in languages like Terraform, serverless framework, cloud formation, and so on).
This Python-based language has two primary goals: improve security and guarantee best-practices compliance.
Only it is simple and completely open-source enough to construct with over 500 different security policies.
It provides guidance on the most effective use of AWS, GCP, and Azure.
The input folder, which may contain Terraform or CloudFormation files, is also scanned.
It’s also useful for checking out cd production lines.
It also works with numerous file types, including CLI, JSON, JUnit XML, and so on.
Features
- Checks Terraform, CloudFormation, and Kubernetes IaC files for security and compliance.
- It can perform comprehensive IaC scanning in AWS, Azure, Google Cloud, and Kubernetes.
- Best practises, industry standards, and security frameworks like HIPAA, CIS, and PCI-DSS inform its many guidelines.
- Users can create rules to meet their organization’s security and compliance needs.
| What is Good ? | What Could Be Better ? |
|---|---|
| Infrastructure as Code (IaC) Security | Limited Runtime Security Coverage |
| Wide Range of Built-in Policies | Limited Language Support |
| Easy Integration | |
| Extensibility and Customization |
Demo video
Price
You can get a free trial and personalized demo from here…
Checkov
4. Anchore
Anchore is a container security platform that helps companies ensure their containerized apps are safe, compliant, and complete.
It does this by giving them tools and services. Anchore has features that can be used during both the build and live stages of deploying containers.
The Docker image is analyzed in great detail. The level of safety is also communicated.
Any orchestration platform, such as Rancher, Docker Swarm, or Amazon ECS, can use this engine independently. The CI/CD pipeline provides access as well.
To verify the safety of your Kubernetes deployment, you’ll need a scanner.
The docker image must be provided for analysis and reporting purposes.
Custom security can also be used for testing purposes.
It deploys the potentially harmful image while accurately defining the policies.
It also encrypts the image so that it may develop an orchestration platform.
Features
- Anchore checks container pictures for bugs and security holes.
- Works with CI/CD processes to check for security automatically while images are being built.
- It works with container registries to look at and scan pictures while they are being pushed or pulled.
- Makes reports that show policy violations and security holes.
- Takes care of the whole container picture lifecycle, including tracking and versioning.
| What is Good ? | What Could Be Better ? |
|---|---|
| Container Image Security | Dependency on Vulnerability Database Updates |
| Comprehensive Vulnerability Analysis | Chance of getting motion sickness |
| Policy-Based Scanning | |
| Continuous Monitoring and Alerting |
Demo video
Price
You can get a free trial and personalized demo from here…
Anchore
5. Kubeaudit
Such a program is an example of a free auditing tool.
The incorrect configuration is located, and the necessary steps to correct it are provided.
The Go language tool is one example of a command-line tool that is commonly used.
Putting it on the PC and using it requires only one command after installation.
It displays a currently running application to which only the superuser has read/write access.
It also aids you in avoiding additional privileges, which helps it avoid typical security issues.
Three distinct modes are available, each with their own set of features.
Built auditing containers, namespaces, pods, etc., can be any of the three levels of severity.
Features
- looks at Kubernetes groups to find security risks and possible holes.
- Checks the settings of Kubernetes objects like pods, deployments, and services to make sure they follow security best practices and rules.
- Helps you fix security problems and make the cluster safer by giving you suggestions and instructions.
- Checks security standards and best practices, such as CIS measures, to ensure the cluster follows the rules.
| What is Good ? | What Could Be Better ? |
|---|---|
| Kubernetes-specific Security Assessment | Limited Scope |
| Lightweight and Easy to Use | Limited Runtime Monitoring |
| Comprehensive Security Checks | |
| Customizable Assessments |
Demo video
Price
You can get a free trial and personalized demo from here…
Kubeaudit – Trial / Demo
6. Clair
Clair is a free and open-source tool for checking the security of container files. Clair isn’t a Kubernetes tool in and of itself, but it can be used with Kubernetes settings to make containers safer.
It provides vulnerability scanning in addition to static security. This API-driven analysis engine ensures the smooth operation of all security-related processes.
You not only need to develop the service but also need to monitor it so that it continuously can do the vulnerability.
Clair can be added to Kubernetes settings to check container pictures before they are deployed. In CI/CD processes, it is often used to make sure that only safe container files are sent to a Kubernetes cluster.
It alerts you to the container’s potential vulnerability and relies only on CVE and related databases.
The National Vulnerability Database will issue a comprehensive report in the event of any impending danger that it is capable of mitigating.
Features
- Clair is made to have conversations that feel normal and involve both parties.
- Clair is very good at understanding what people say.
- Depending on what is being said, Clair can understand and react.
- Clair has access to a lot of data and can give you answers that are useful.
| What is Good ? | What Could Be Better ? |
|---|---|
| Container Vulnerability Scanning | Limited to Known Vulnerabilities |
| Wide Range of Supported Languages | Limited Customization |
| Integration with Container Registries | |
| Detailed Vulnerability Reports |
Demo video
Price
You can get a free trial and personalized demo from here…
Clair
7. Kubei

Most of it is developed in the Go programming language, and it displays imminent danger in the cluster.
Everything included in the CIS Docker benchmark is covered.
Application pods, system pods, and Kubernetes clusters are all scannable options.
The scan can be modified in terms of its speed, depth, and sensitivity.
With the help of GUI, you may observe anything and mitigate them.
It monitors the public’s perception and gives updates in real time.
It has a web-based interface and supports multi-scanning.
Features
- Sees pictures of containers to find risks and vulnerabilities like known holes in software.
- Sees if there are any mistakes, vulnerabilities, or ways to attack Kubernetes setups.
- It lets you always keep an eye on Kubernetes operations and container files to find and report security issues.
- Checks for flaws by connecting to well-known sources to get the most up-to-date information and find out how dangerous container pictures are.
| What is Good ? | What Could Be Better ? |
|---|---|
| Runtime Security Scanning | Additional Operational Overhead |
| Container Image Scanning | Resource Intensive |
| Active Monitoring and Alerts | |
| Comprehensive Security Checks |
Demo video
Price
You can get a free trial and personalized demo from here…
Kubei
8. Kubesec
This security risk analysis tool configures and validates the manifest files that get used for cluster operations and deployment.
Users can install this with container images.
As an open-source tool, it comes with a bundle of HTTP servers where it comes with a background at 8080 by default.
It has the capacity to run the service via HTTPS at v2.kubersec.io/scan.
It also scans multiple YAML documents, but it must be a single input file.
Features
- scans Kubernetes configurations to identify security risks and potential vulnerabilities.
- assigns risk scores to configurations based on their security posture, allowing for prioritization of remediation efforts.
- evaluates configurations against best practices and security standards to ensure adherence to industry guidelines.
- provides recommendations on how to mitigate identified security risks and improve the security of Kubernetes configurations.
| What is Good ? | What Could Be Better ? |
|---|---|
| Kubernetes-specific Security Assessment | Limited to Configuration Assessment |
| Simple and Lightweight | Limited Customization |
| Comprehensive Security Checks | |
| Integration with CI/CD Pipelines |
Demo video
Price
You can get a free trial and personalized demo from here…
Kubesec
9. Kube Scan
It is packaged in a container since it is a container scanner.
This can be installed in a fresh cluster, and after scanning the workload, a risk score and further information will be presented in a web-based user interface.
It also delivers a score between zero and ten, with ten indicating the highest danger.
This is a free, publicly available, and governed by the same principles as KCCSS.
More than 30 different security options, including capabilities, privilege level, risk baseline, etc., work analogous to CVVSS.
Exploitation is made simpler due to the correlation between the risk score and the risk baseline.
This rescan happens every 24 hours, and it operates in a container to deliver the best result.
Features
- looks through Kubernetes systems to find security holes and incorrect settings.
- checks whether Kubernetes clusters’ security settings are in line with best practices and industry norms.
- Finds known security holes in Kubernetes parts like the API server, kubelet, and more.
- checks against security standards, like CIS standards, to make sure that the cluster is following the rules.
| What is Good ? | What Could Be better? |
|---|---|
| Lightweight and Easy to Use | Expertise Required |
| Comprehensive Security Scanning | Maintenance and Updates |
| Open Source | |
| Continuous Integration and Deployment (CI/CD) Integration |
Kube Scan
10. MKIT
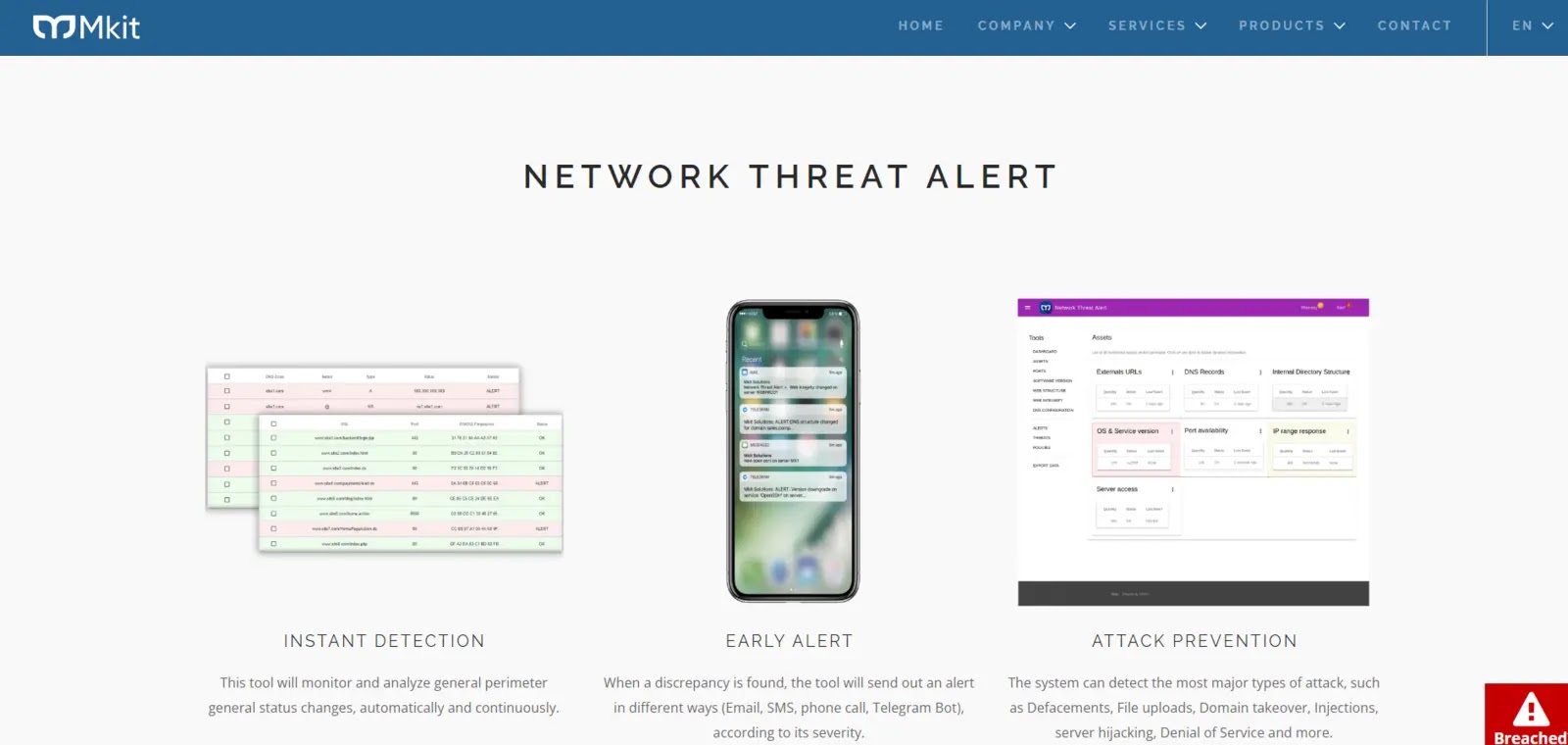
This tool is very helpful for the quick identification of security risks.
It keeps the cluster and its resources.
There is a quick and easy way to find out the misconfiguration in the cluster.
The interface for this Kubernetes Container Scanner tool is present, and it runs by default.
It helped you to see the passed and failed checks.
You can also know the reason behind the affected resource in detail by clicking on the affected resource section.
This software is straightforward to install and helps to build open-source libraries.
It also provides the support of multiple Kubernetes like AKS, EKS, and GKE.
It can also store sensitive data in the container.
Features
- Designed to check how safe controlled Kubernetes services like Amazon EKS, Azure AKS, and Google GKE are.
- Checks managed Kubernetes systems for security holes, incorrect settings, and problems with compliance.
- looks at different Kubernetes parts, like the API server, kubelet, and others, to find possible vulnerabilities.
- checks the cluster’s access control methods, like RBAC, to make sure they’re working right and lower the risk of someone getting in without permission.
| What is Good ? | What Could Be Better ? |
|---|---|
| Kubernetes Security Assessment | Limited to Managed Kubernetes Environments |
| Comprehensive Security Checks | Learning Curve and Expertise Required |
| Compliance Auditing | |
| Customizable Assessments |
Demo video
Price
You can get a free trial and personalized demo from here…
MKIT
Final Thoughts
The above Kubernetes Container Scanner tools aim to secure the cluster so that hackers can not break it.
This scanner helps to deploy the application and helps to identify vulnerabilities.
To quickly discover and fix security concerns in Kubernetes, container scanners must be integrated into CI/CD pipelines and frequently scanned base images and runtime environments.
Choose a Kubernetes container scanner based on functionality, integration, and community support.
Also Read
Read the full article here