On September 22, 2022, the U.S. Patent and Trademark Office (USPTO) conducted a live meeting for its Artificial Intelligence (AI) and Emerging Technologies (ET) Partnership Series. During this meeting, panelists from industry and the USPTO provided helpful tips on drafting and prosecuting patent applications that include AI components, including special tips for the biotech industry. Key takeaways from the meeting and published materials will be summarized in our Three-Part Blog Series.
Part Two – Landscape of AI in Biotechnology
Nicholas Pairolero, Research Economist, USPTO provided an informative landscape of AI in Biotech. Overall, AI is increasingly used in biotechnology, however biotechnology AI patenting is diffusing across all technologies, owners, and inventor-patentees. The definition of AI in this panel corresponded with 8 component technologies, including planning/control, knowledge processing, speech, AI hardware, evolutionary computation, natural language processing, machine learning, and vision. Some interesting charts generated by Mr. Pairolero and presented during the panel are shown herein.
In this chart, machine learning applications, evolutionary computation, and knowledge processing in the biotechnology space corresponded with higher filing rates than patent application filings in general.
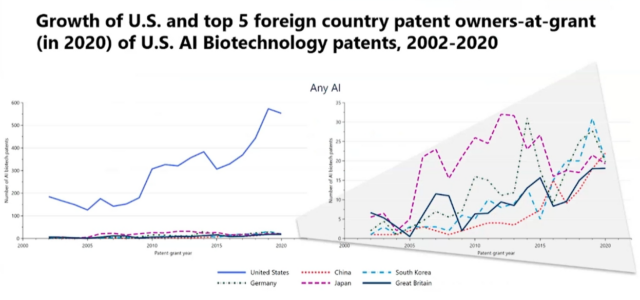
In this chart, Mr. Pairolero analyzed patent application filings in accordance with the country of the patent owner once the patent application granted. On the left, the patent owners from the U.S. that filed U.S. applications clearly outweighed patent owners from foreign countries. On the right, the patent owners filing applications related to AI Biotechnology patents is more dispersed.
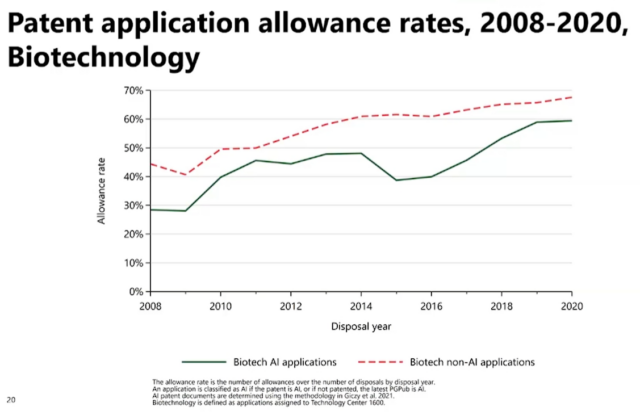
In this chart, the allowance rate of AI biotechnology patent applications and non-AI patent applications is illustrated. As shown, there is a slightly higher allowance rate for biotechnology applications when they are not associated with AI verses the applications that are associated with AI.
Copyright © 2022, Sheppard Mullin Richter & Hampton LLP.National Law Review, Volume XII, Number 278
Read the full article here