Computers have become an indispensable part of everyday life. Computer systems store almost all important personal information and critical infrastructure data, such as government archives and bank accounts. And all that information is valuable, especially to cybercriminals. Traditional theft has evolved to become data theft. But how did cybercrime begin? Which historic threats still exist?
Early Examples of Cybercrime
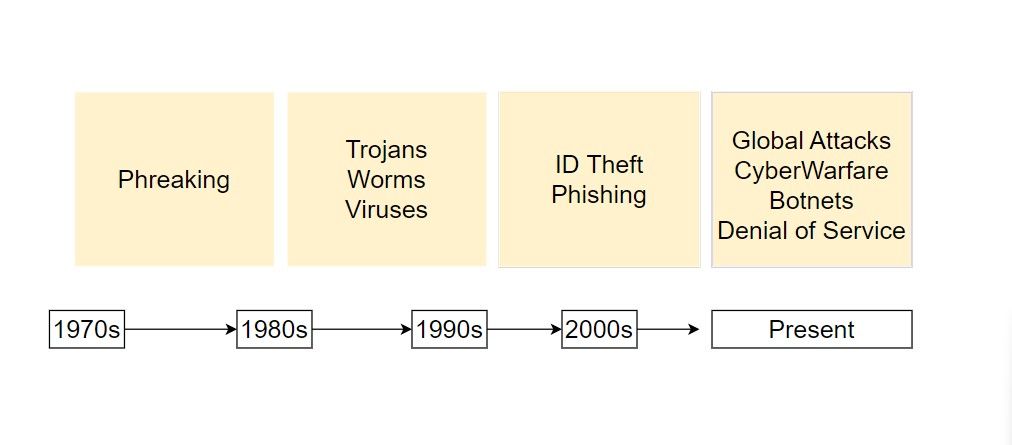
In the 1970s, the first examples of cyberattacks were via telephones. Colloquially known as “phreaking”, the goal here was to make long-distance phone calls; the attackers were actively using reverse engineering, i.e. recreating the tones used for these calls to make free phone calls anywhere in the world.
Worms appeared in the late 1980s. The name of this first worm is the Morris worm, named after its developer, Robert Morris. This wasn’t made for any malicious purpose; instead, it was developed to gauge the size of the internet. However, huge financial losses occurred as a result, amounting to tens of billions of dollars. Morris unintentionally became one of the most famous hackers.
In 1989, attackers carried out the first ransomware attack, complicating things further. This was on the health sector; the attackers claimed they had AIDS-related software, sending tens of thousands of floppy disks to dozens of countries. Victims of the AIDS Trojan were asked to send $189 to a P.O. box in Panama in order to decrypt their systems. Today, ransomware is still a critical threat.
How Has Cybercrime Evolved to the Present Day?
In the 1990s, web browsers and e-mail technologies became widespread. These were great for the everyday individual—and for cybercriminals, because it was possible to reach large masses in a very short time. Cybercriminals were now able to use the internet instead of carrying the malicious software they developed with floppy disks. Phishing attacks and attempts to defraud people hugely increased in this period. Since there were no serious security measures and laws, many cybercriminals made serious money illegally.
Social media and easier online communications welcomed in the new millennium, and identity theft via online services gained momentum. Social media sites are just databases containing the information of millions of users. Cyberattacks became systematic with hackers identifying targets and beginning to shape appropriate attack vectors.
Developers and technology companies are announcing thousands of new technologies, updates, programs, hardware, and software every day. That means cybersecurity is getting much more complicated. The best example of this is botnets. Botnets can control thousands of devices exposed to malware. Imagine attacks by a huge number of internet-connected devices on a vulnerable website, i.e. a Distributed Denial of Service (DDoS) attack.
Worms, Trojans, phishing, ID theft, ransomware, DDoS attacks: all remain big threats to our data security.
The Relationship Between IT Engineering and IoT
Information security simply means protecting data from unauthorized access. Every company needs to protect the data of itself, its customers, and registered members. That’s why large businesses employ professionals to beef up their information security.
The primary goal of IT security engineers is to apply security principles to information technology. With the Internet of Things (IoT), everything with an online connection can be attacked by cybercriminals—it’s not just websites and apps that are subject to cyberattacks. Refrigerators, ovens, and even air conditioners in your home now need protection too. Since each of these devices can have its own IP address, they can also have potential security vulnerabilities.
And if you think that a device that does not communicate with an online network is safe, you are wrong. It is possible to use carriers such as a USB to attack devices that do not connect to the internet directly. Corporate companies in particular need professional and qualified IT experts to consider any potential IoT vulnerabilities.
Security teams must adopt the principles of confidentiality, integrity, and availability, integrating these principles and requirements into systems after successful test results. As such, this is of critical importance for the developer, the manufacturers, and IT engineers.
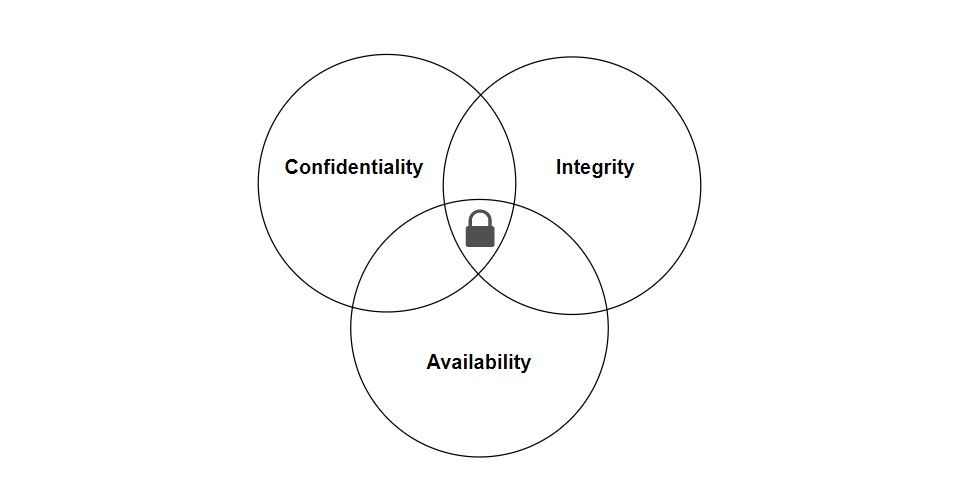
Developers, manufacturers, and IT teams might seem to be independent of each other, but actually, they are parts of an inseparable system. Information assurance should follow a certain system for each transaction, so a regular and predetermined network is essential to ensure consistency between the testing team, IT engineers, and developers. A lot needs to be decided in advance. You should develop a product, which will have these determined requirements, in line with the approaches of the CIA triad, i.e. confidentiality, integrity, and usability. So what’s the importance of these?
The Importance of the CIA Triad
One of the fundamental principles underlying information security is the CIA triad. You can think of the CIA triad as immutable articles of a constitution. IT professionals think in line with the principles set out in the CIA triad.
- Confidentiality: Is the information kept secret? It is necessary to use various encryption techniques to prevent the data from becoming unusable with any unauthorized access.
- Integrity: Storing information correctly is just as important as keeping it confidential. It is necessary to take action against data that is changed in an unauthorized way.
- Availability: Of course, the data needs to be available to those who really need access to it too! It is important to access not only software but also hardware information.
Protect Yourself From Cybercrime
As a result of increasing technological developments, today’s cybercrime is increasing with ever-greater acceleration. Staying up to date and knowing the importance of your passwords and data is vital in protecting yourself from cybercriminals. If you do not have professional knowledge on this subject, get support from experts and take into account the recommendations made about data security.
Most devices you use contain important and confidential information about you. You don’t want any private data falling into the wrong hands. Even if devices do not have these, they have the potential to cause material damage. That’s why it’s important you know how cybercrime develops and its trajectory; that way, you can take some steps to protect yourself.
Read the full article here