Over a million WordPress websites have been at risk due to a critical SQL Injection vulnerability discovered in the popular LayerSlider plugin.
The flaw, CVE-2024-2879, could allow unauthenticated attackers to extract sensitive data, including password hashes, from websites’ databases.
The vulnerability, tracked under the identifier CVE-2024-2879, has been assigned a CVSS score of 9.8, categorizing it as critical.
Trustifi’s Advanced threat protection prevents the widest spectrum of sophisticated attacks before they reach a user’s mailbox. Try Trustifi Free Threat Scan with Sophisticated AI-Powered Email Protection .
The Common Vulnerability Scoring System (CVSS) score reflects the severity of the risk, with this particular score indicating that the vulnerability could have a devastating impact on affected websites.
The security flaw was responsibly reported by a researcher named AmrAwad through the Wordfence Bug Bounty Program.
AmrAwad’s diligent work earned them a bounty of $5,500.00, marking the highest payout in the program’s history.
The discovery underscores the importance of collaborative efforts between security researchers and companies to enhance the security of the web.
A recent tweet from Wordfence shared that the SQL Injection vulnerability in the LayerSlider plugin was disclosed.
Technical Breakdown
The technical analysis of the vulnerability revealed that the LayerSlider plugin versions 7.9.11 to 7.10.0 were susceptible to SQL Injection via the ls_get_popup_markup action.
function ls_get_popup_markup() {
$id = is_numeric( $_GET['id'] ) ? (int) $_GET['id'] : $_GET['id'];
$popup = LS_Sliders::find( $id );
if( $popup ) {
$GLOBALS['lsAjaxOverridePopupSettings'] = true;
$parts = LS_Shortcode::generateSliderMarkup( $popup );
die( $parts['container'].$parts['markup'].'<script>'.$parts['init'].'</script>' );
}
die();
}The flaw stemmed from insufficient escaping of user-supplied parameters and inadequate preparation of SQL queries.
The vulnerable code snippet, as detailed in the Wordfence report, shows how the id parameter could be manipulated if not a number, leading to the potential for SQL injection.
Swift Response and Patch Release
Upon notification of the vulnerability, the Kreatura Team, developers of LayerSlider, responded promptly.
They released a patch within two days, with the updated version 7.10.1 addressing the security issue. Users are urged to update their sites with this latest version as soon as possible to mitigate the risk.
Wordfence has assured its users, including those with Premium, Care, and Response plans and those using the free version of the plugin, that they are protected against exploits targeting this vulnerability.
The Wordfence firewall’s built-in SQL Injection protection is designed to detect and block malicious SQL queries.
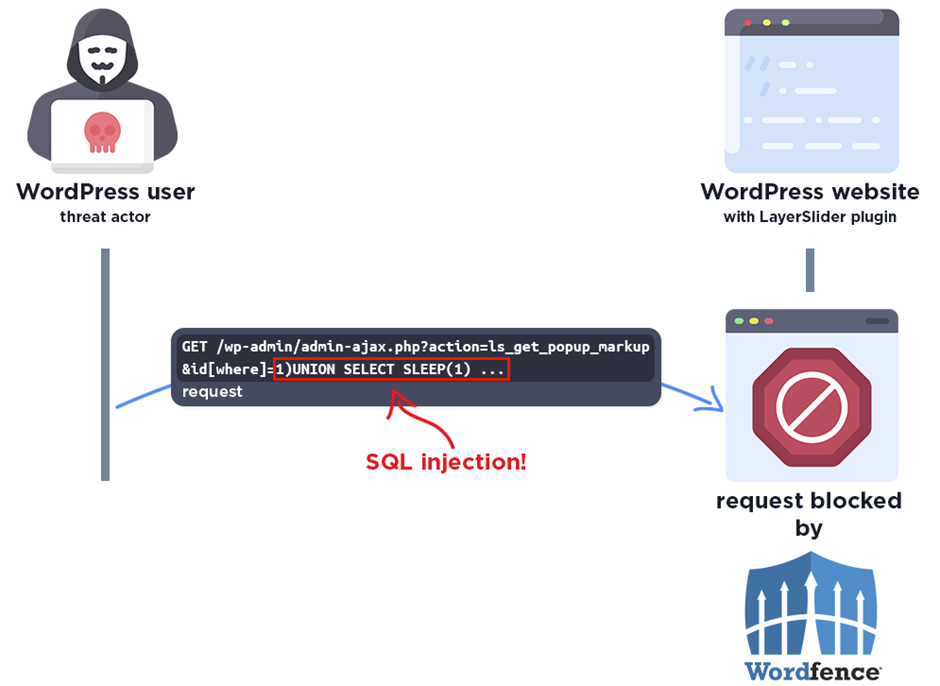
The SQL Injection vulnerability within LayerSlider posed a significant threat to over a million WordPress sites. However, a crisis was averted thanks to the quick actions of the security researcher and the Kreatura Team.
It is a stark reminder of maintaining up-to-date security measures on all web platforms.
WordPress users are encouraged to check their sites and ensure they run the fully patched version of LayerSlider. Sharing this advisory with others who use the plugin is also recommended to help maintain a secure web environment.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.
Read the full article here

