A security researcher reported a critical vulnerability in the WP-Members Membership Plugin that allows attackers to inject malicious scripts and potentially take over websites.
Administrators could take advantage of the unauthenticated stored XSS flaw that was present in the X-Forwarded header. To protect their users, researchers were rewarded for their responsible disclosure.
On March 7th, the plugin vendor released a partial patch (v3.4.9.2) and a full fix (v3.4.9.3) shortly after and upgraded to the latest version to mitigate the risk.
A critical vulnerability (CVSS: 7.2) exists in WordPress’s WP-Members Membership Plugin versions up to 3.4.9.2, which arises from insufficient sanitization and escaping of the X-Forwarded header.
Malicious attackers can exploit this to inject arbitrary scripts into the database, which then execute whenever a user visits the edit user page.
While a partial fix was implemented in version 3.4.9.2, a complete resolution arrived only in version 3.4.9.3. Upgrading to the latest version is crucial to addressing this security risk.
Technical Analysis Of The Vulnerability:
An attacker can exploit a cross-site scripting vulnerability in WP-Members by injecting malicious code into the X-Forwarded header during user registration.
It is achieveable by intercepting the registration request with a proxy and modifying it to include the attacker’s script, while the vulnerable plugin stores the attacker-provided script as the user’s IP address, allowing execution whenever that user information is displayed.

The `rktgk_get_user_ip` function in a vulnerable plugin relies on unsanitized HTTP headers (`HTTP_CLIENT_IP` or `HTTP_X_FORWARDED_FOR`) to determine a user’s IP address.
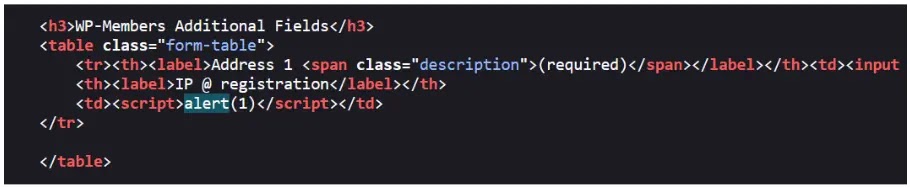
It allows attackers to inject malicious scripts into these headers, which are then stored as the user’s IP and when an administrator views or edits such a user account, the injected script executes within the administrator’s browser session due to the reflected XSS vulnerability.
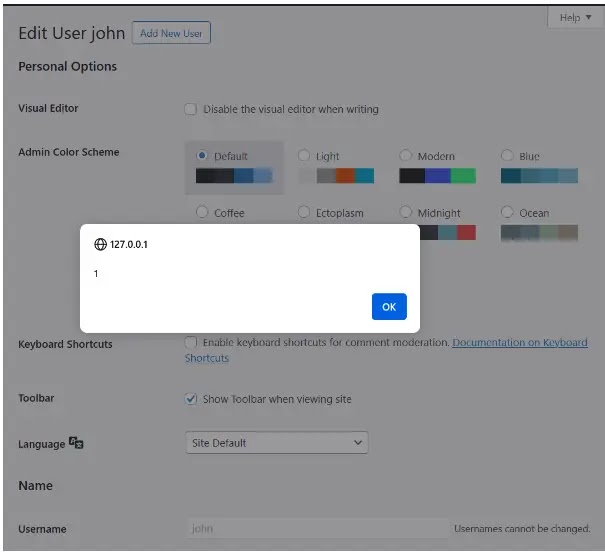
The administrator account may be compromised, malicious users may be created, or users may be redirected to websites that are harmful.
Wordfence contacted the vendor and coordinated a patch; while version 3.4.9.2 addressed part of the issue, existing payloads could still be triggered.
Version 3.4.9.3 fully patched the vulnerability; updating the plugin and advising users to share this information with others who use the plugin is recommended.
Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free Guide
Read the full article here

