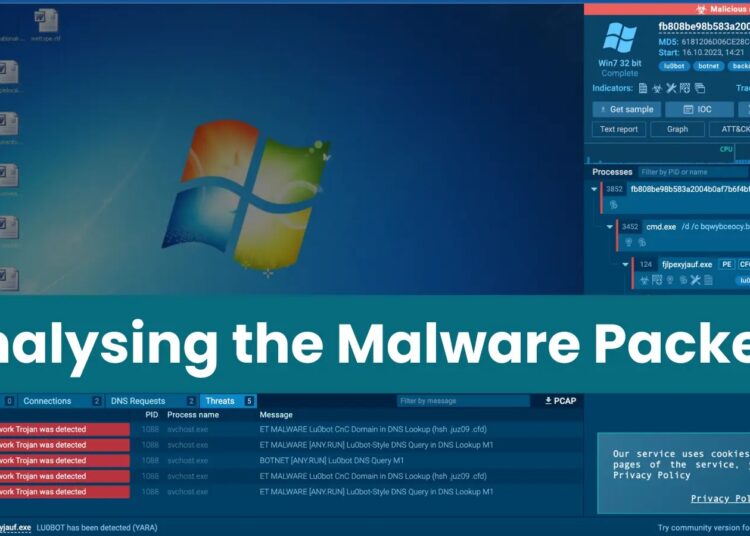
Antiviruses can quickly detect malicious executable files, but attackers can bypass this by using packers to compress and obfuscate the code, making it difficult for antivirus software to analyze.
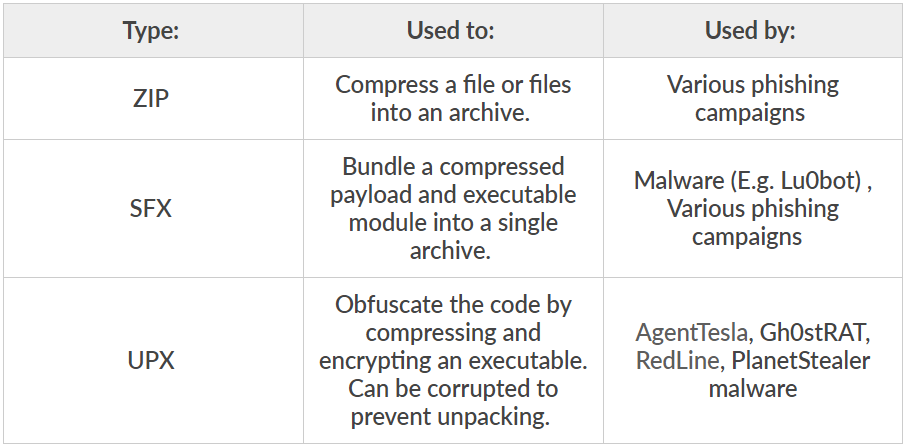
Packers are similar to compression tools like ZIP and RAR, but some packers, like UPX, specifically target executables.
Packers, including legitimate ones (VMprotect, ASpack) and custom-made ones by attackers like ZIP, SFX, and UPX, deliver malware through compressed archives.
ZIP archives compress files and can be used to hide malicious programs within legitimate files or password-protected archives.
In contrast, SFX archives are self-extracting and contain an unpacking module that triggers installation upon execution, bypassing separate extraction tools.
UPX packers compress and encrypt executable code, making it challenging to analyze and potentially preventing unpacking altogether.
These techniques compress malware payloads, potentially bypass email security measures, and can disguise malicious installation processes.
Hackers can tamper with UPX-packed archives to hinder analysis, and there are two main methods: using an unreleased version of UPX to pack the archive or modifying the l_info and p_info structures within the archive itself.
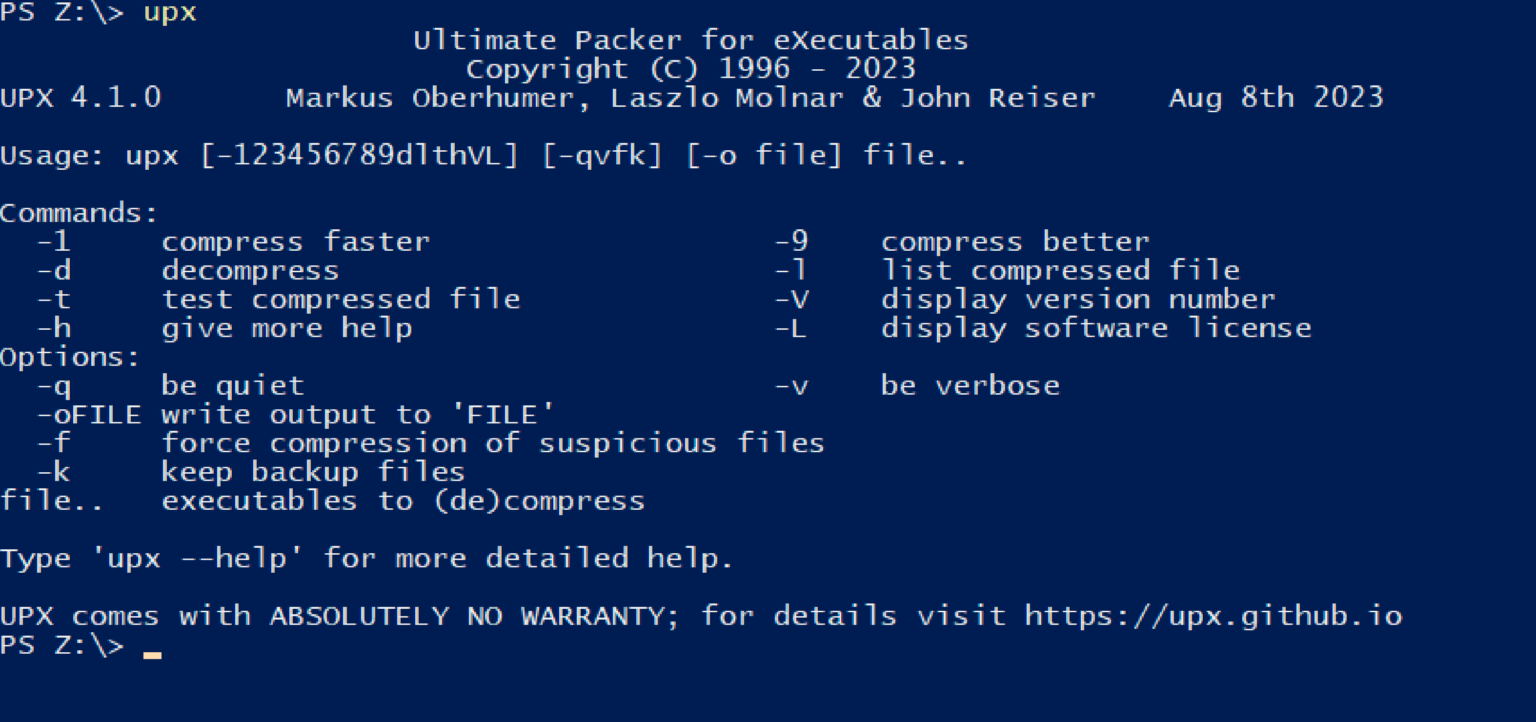
Both techniques achieve the same outcome: the packed archive becomes undetectable by standard UPX unpackers and signature-based security systems.
It can be problematic for researchers who rely on unpacking tools to analyze the archive’s contents and for security software that uses signatures to identify malicious code.
Integrate ANY.RUN in Your Company for Effective Malware Analysis
Are you from SOC, Threat Research, or DFIR departments? If so, you can join an online community of 400,000 independent security researchers:
- Real-time Detection
- Interactive Malware Analysis
- Easy to Learn by New Security Team members
- Get detailed reports with maximum data
- Set Up Virtual Machine in Linux & all Windows OS Versions
- Interact with Malware Safely
If you want to test all these features now with completely free access to the sandbox:
Essentially, tampering with the archive’s internal structure renders it unreadable by standard UPX tools while the packed malicious payload remains fully functional.
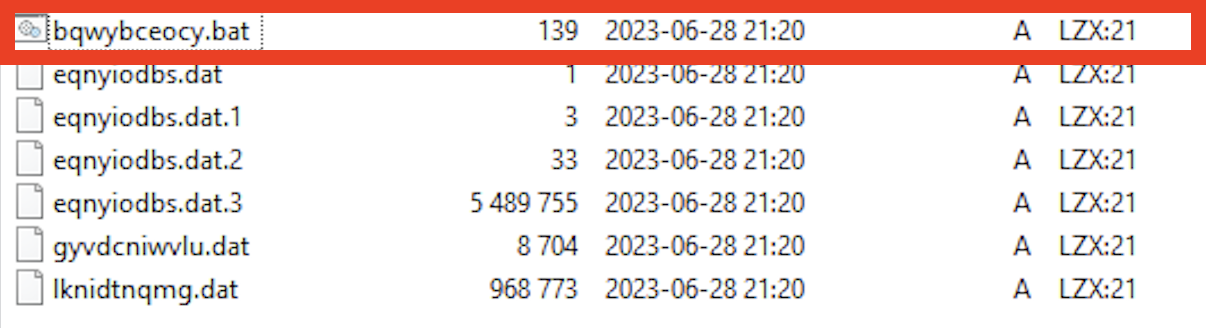
To identify the type of archive you’re dealing with, especially for less common formats like SFX and UPX, use file identification tools like the “file” command on Unix. At the same time, TrID is a utility for both Windows and Linux that provides detailed file information.
Hex editors such as xxd and hexdump allow manual inspection by viewing the file’s magic bytes.
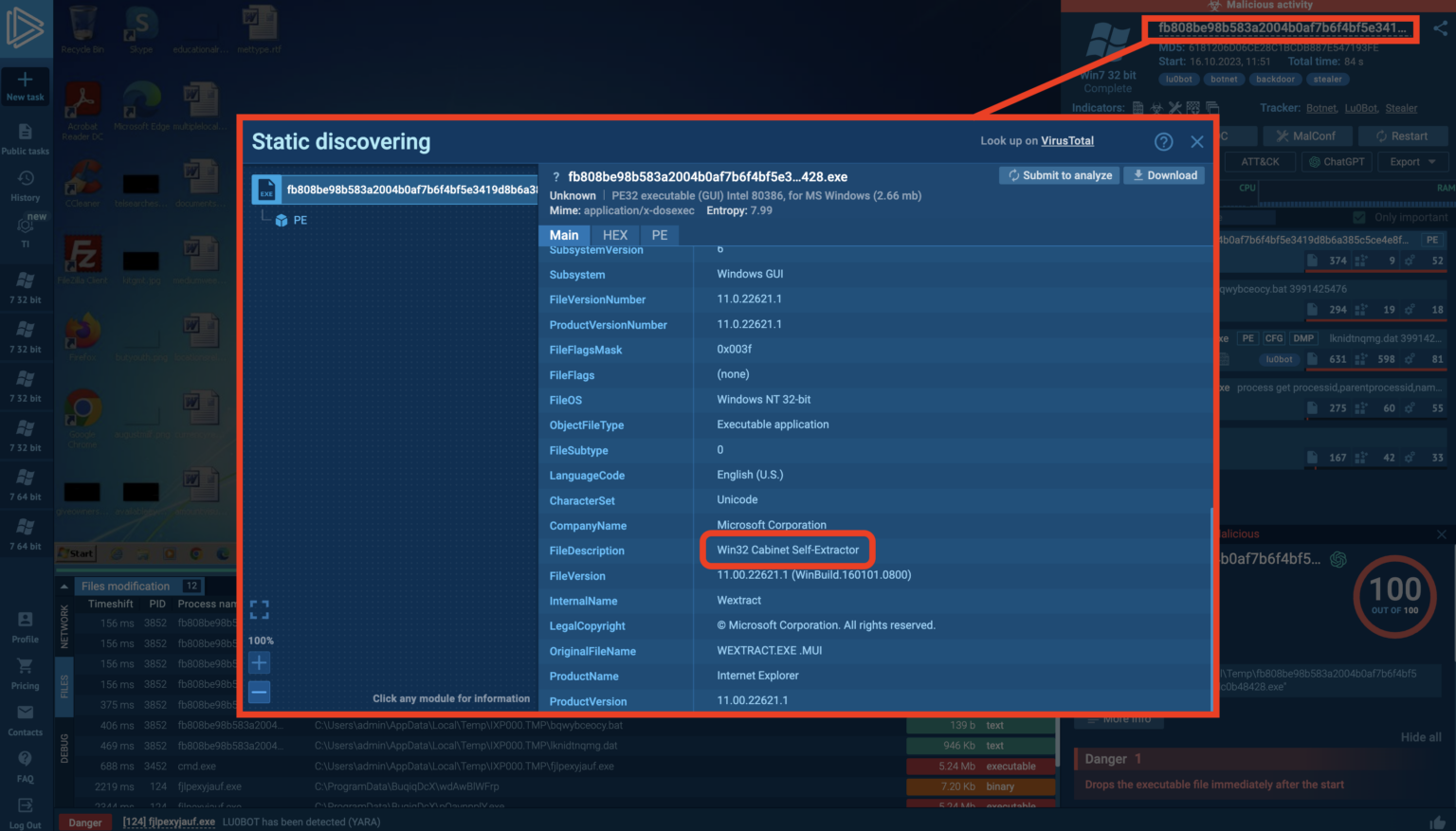
Identifying an SFX archive and UPX file in ANY.RUN
ANY.RUN can be used to identify packing methods for malware samples, and the Static Discovery window displays file information. In the case of SFX archives, the description will indicate the compression type (e.g., “Win32 Cabinet Self-Extractor”).
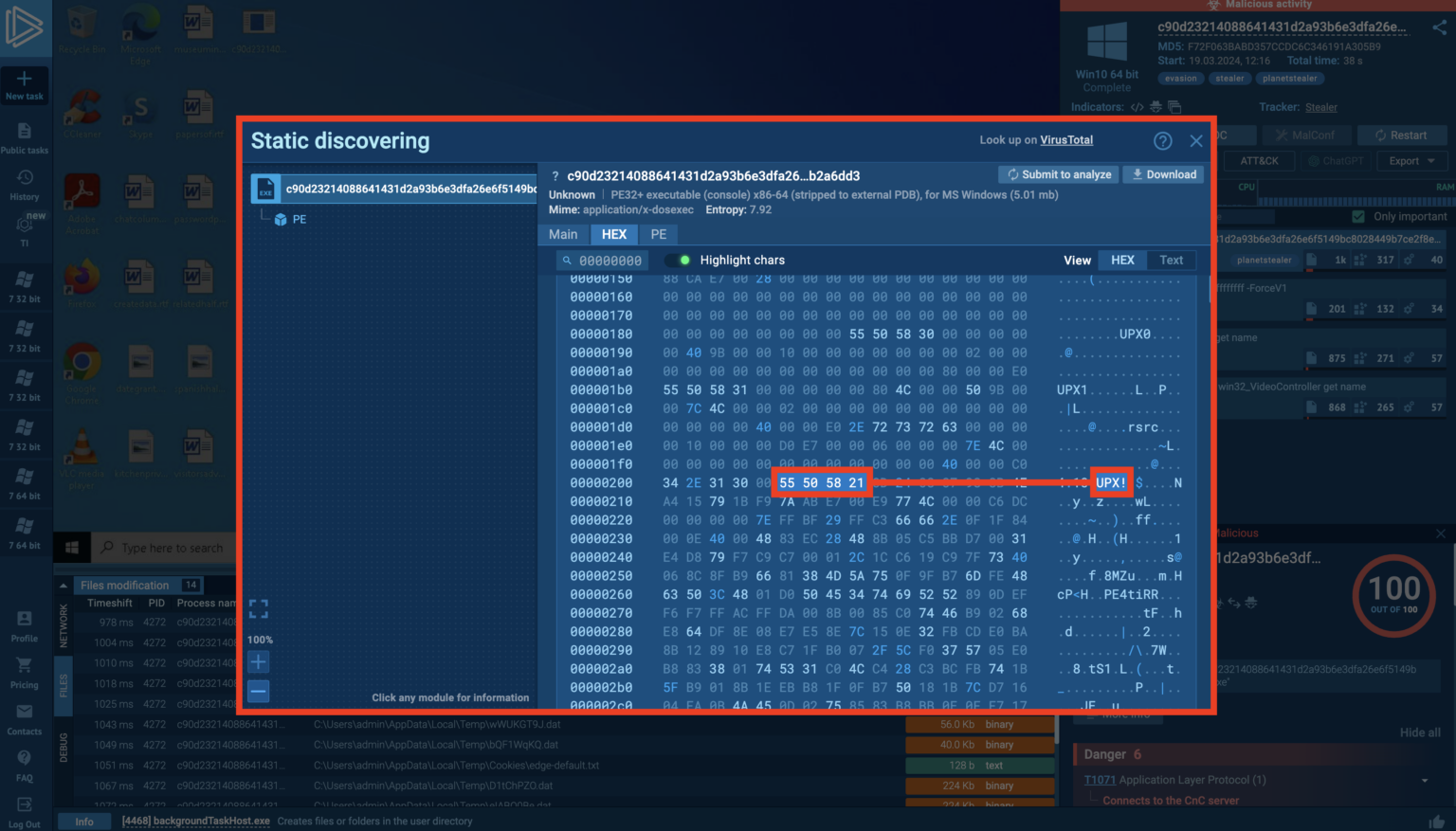
UPX packed files can be identified by examining the Hex Editor tab within Static Discovery. ANY.RUN converts hex data to text, which allows to search for strings like “UPX0”, “UPX1”, or “UPX!” at the beginning of the file to confirm UPX packing.
ZIP and SFX archives bundle malicious executables with innocuous files, evading email security., whereas UPX encrypts the executable and decrypts it in memory during execution. Examining file headers (aside from ZIP) for packer signatures can reveal packed malware.
What is ANY.RUN?
ANY.RUN is a cloud-based malware lab that does most of the work for security teams. 400,000 professionals use ANY.RUN platform every day to look into events and speed up threat research on Linux and Windows cloud VMs.
Advantages of ANY.RUN
- Real-time Detection: ANY.RUN can find malware and instantly identify many malware families using YARA and Suricata rules within about 40 seconds of posting a file.
- Interactive Malware Analysis: ANY.RUN differs from many automated options because it lets you connect with the virtual machine from your browser. This live feature helps stop zero-day vulnerabilities and advanced malware that can get past signature-based protection.
- Value for money: ANY.RUN’s cloud-based nature makes it a cost-effective option for businesses since your DevOps team doesn’t have to do any setup or support work.
- Best for onboarding new security team members: ANY. RUN’s easy-to-use interface allows even new SOC researchers to quickly learn to examine malware and identify signs of compromise (IOCs).
Are you from SOC and DFIR Teams? – Analyse Malware Incidents & get live Access with ANY.RUN -> Start Now for Free
Read the full article here