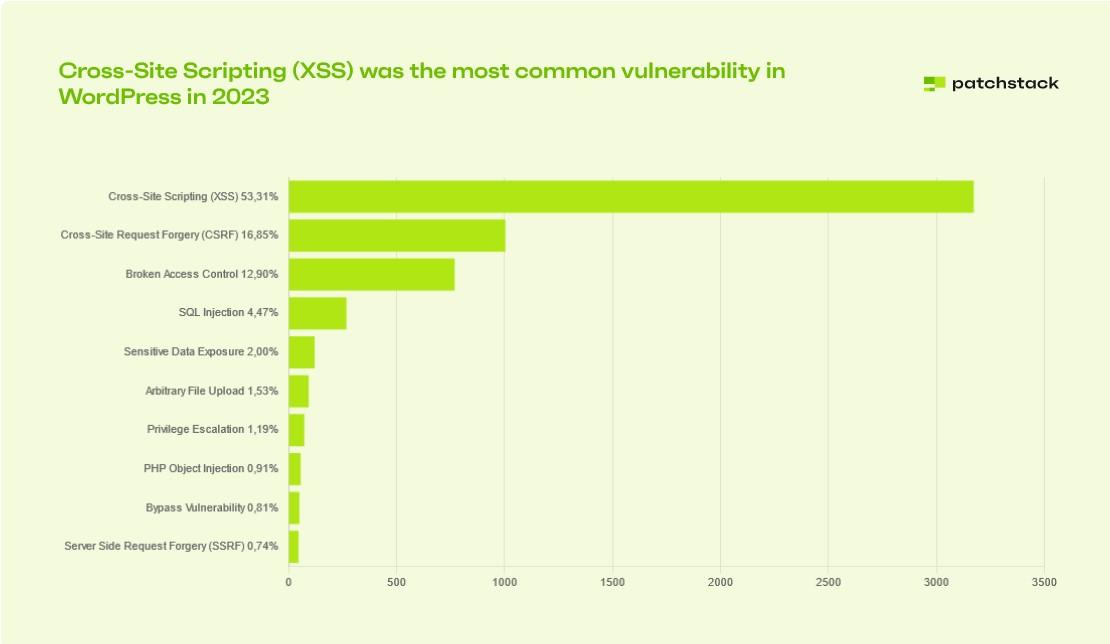
Of all the security flaws discovered in the WordPress ecosystem, cross-site scripting (XSS) vulnerabilities accounted for about 53.3% of the total.
As of last year, XSS accounted for 27% of all security vulnerabilities, a significantly higher rate than in 2022.
Cross-site scripting (XSS) is a security flaw in which an attacker can insert malicious code into a website.
After that, the malicious code can be used to do undesirable acts like redirect traffic or steal confidential data, which could provide the attacker with control over a website.
Why is XSS the Most Common Kind of Vulnerability?
According to the PatchStack Security report, a flaw in the Freemius framework, a third-party managed eCommerce platform, was the source of a significant number of CSRF vulnerabilities in 2022.
Trustifi’s Advanced threat protection prevents the widest spectrum of sophisticated attacks before they reach a user’s mailbox. Try Trustifi Free Threat Scan with Sophisticated AI-Powered Email Protection .
The framework’s widespread use meant that it affected a large number of plugins.
Of those XSS vulnerabilities, researchers can trace more than 1,200 of them back to Freemius.
“This year we saw once again how a single cross-site scripting vulnerability in the Freemius framework resulted in 1,248 plugins inheriting the security vulnerability, exposing their users to risk”, the report said.
“21% of all new vulnerabilities discovered in 2023 can be traced back to this one flaw.
Developers need to choose their stack carefully and promptly apply security updates when these become available.”
Additionally, 42.9% of newly discovered vulnerabilities have a severity level of high or critical overall.
The proportion of vulnerabilities with high and critical severity is much larger than it was in 2022. 56.6% of vulnerabilities this year were categorized as “only” medium severity concerns, compared to 84% last year.
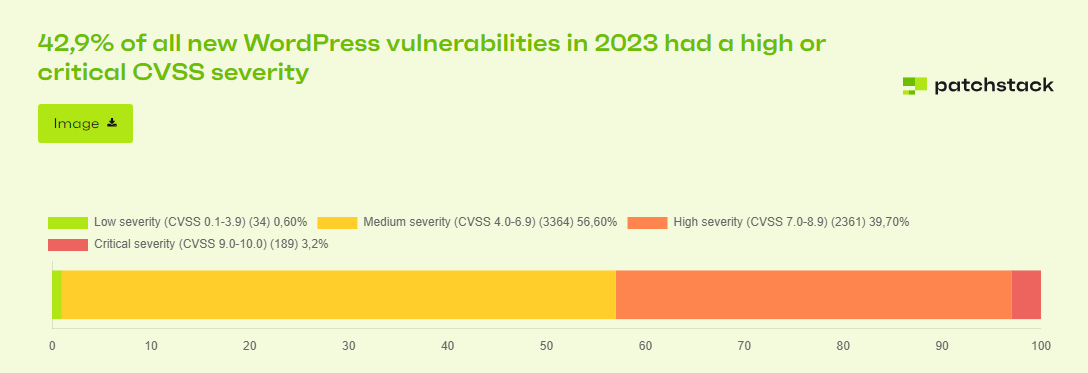
A high risk of 13.6% of newly discovered vulnerabilities necessitated quick action. 34.7% had a “Medium” priority level, which means that while they might be used in targeted attacks, they were severe enough to receive a virtual patch.
“Looking at all new security vulnerabilities found in 2023, 58.9% did not require any authentication to be exploited.
These vulnerabilities are inherently more dangerous because they can be exploited automatically and en masse”, researchers said.
On the other hand, 13.4% of the newly discovered vulnerabilities could only be exploited with the administrator role.
The Increase of Abandoned Plugins
The high number of abandoned plugins is another important source of vulnerabilities.
However, 827 plugins and themes in all were submitted to the WordPress team in 2023.
After that, 481 susceptible components were abandoned and taken out of the plugin repository.
To raise awareness of the “zombie plugin pandemic” in WordPress, researchers reported 404 of those plugins in a single day.
These “zombie” plugins are parts that, while first appearing secure and up-to-date may have unpatched security flaws.
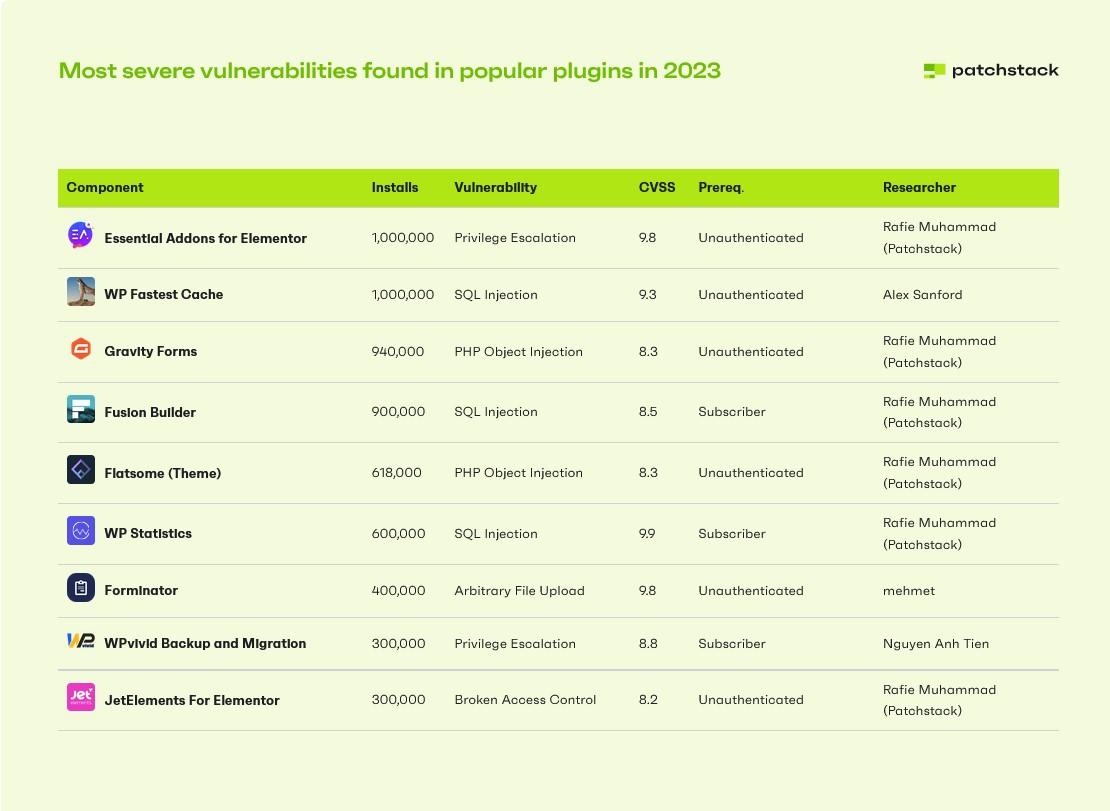
Top 5 Newly Discovered Vulnerabilities with the Most Attempted Exploits
- tagDiv Composer plugin – Unauthenticated Stored XSS vulnerability
- WooCommerce Payments plugin – Unauthenticated privilege escalation vulnerability
- Ultimate Member plugin– Unauthenticated Privilege Escalation
- Essential Addons for Elementor plugin– Unauthenticated Privilege Escalation
- HT Mega Absolute Addons for Elementor plugin– Unauthenticated Privilege Escalation
Still, the rise does not indicate a deteriorating security scenario inside the WordPress platform.
Instead, it demonstrates that security is a higher priority for both plugin producers and security researchers.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.
Read the full article here

