Over the past year, macOS users, particularly those in the cryptocurrency sector, have been increasingly targeted by infostealers. These malicious programs aim to harvest credentials and data from crypto wallets.
amf Threat Labs has been monitoring the evolution of these threats and has identified two recent attacks that have successfully deployed infostealers on victims’ macOS systems.
The first attack involves a fake sponsored ad for “Arc Browser” that leads to a malicious website, which can only be accessed through the ad link.
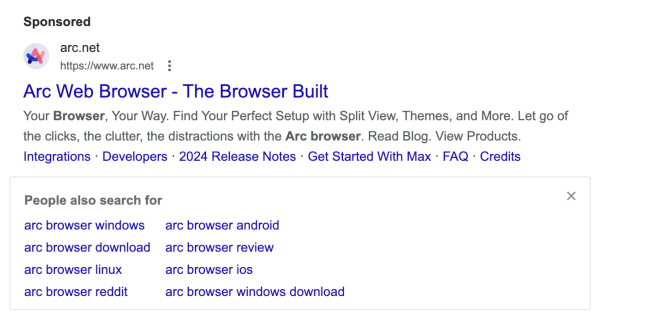
This site distributes a variant of the Atomic Stealer malware, which uses xor encoding to evade detection and employs AppleScript to steal information.
Download Free CISO’s Guide to Avoiding the Next Breach
Are you from The Team of SOC, Network Security, or Security Manager or CSO? Download Perimeter’s Guide to how cloud-based, converged network security improves security and reduces TCO.
- Understand the importance of a zero trust strategy
- Complete Network security Checklist
- See why relying on a legacy VPN is no longer a viable security strategy
- Get suggestions on how to present the move to a cloud-based network security solution
- Explore the advantages of converged network security over legacy approaches
- Discover the tools and technologies that maximize network security
Adapt to the changing threat landscape effortlessly with Perimeter 81’s cloud-based, unified network security platform.
Much like the Atomic stealer sample dissected above, this stealer also prompts the user for their macOS login password using the following AppleScript call.
Google ad services link:
hXXps://www.googleadservices.com/pagead/aclk?sa=L&ai=DChcSEwiC8Jm6-ZSFAxUIwUwCHXbYB3MYABAAGgJ0bQ&ase=2&gclid=EAIaIQobChMIgvCZuvmUhQMVCMFMAh122AdzEAAYASAAEgKHuvD_BwE&ei=0lQEZp-wCbWqptQP-Kq0mA8&ohost=www.google.com&cid=CAASJORoo4VHmMOQTyTY97tSpGDZA1DEcypIUn9R0xOdHJi1x9N3KQ&sig=AOD64_2IOygLFSykCaouP6GmJOVlWRg3AA&q&sqi=2&nis=4&adurl&ved=2ahUKEwif4Y66-ZSFAxU1lYkEHXgVDfMQ0Qx6BAgJEAEThe malware prompts users for their macOS password to access keychain data and sends the stolen information to the attacker’s server.
Attack 2: Meethub Application
The second attack uses a fake Meethub application, which poses as a virtual meeting platform. The attackers, who have a significant online presence, lure victims through direct messages on social media, discussing topics like podcast recordings or job opportunities.
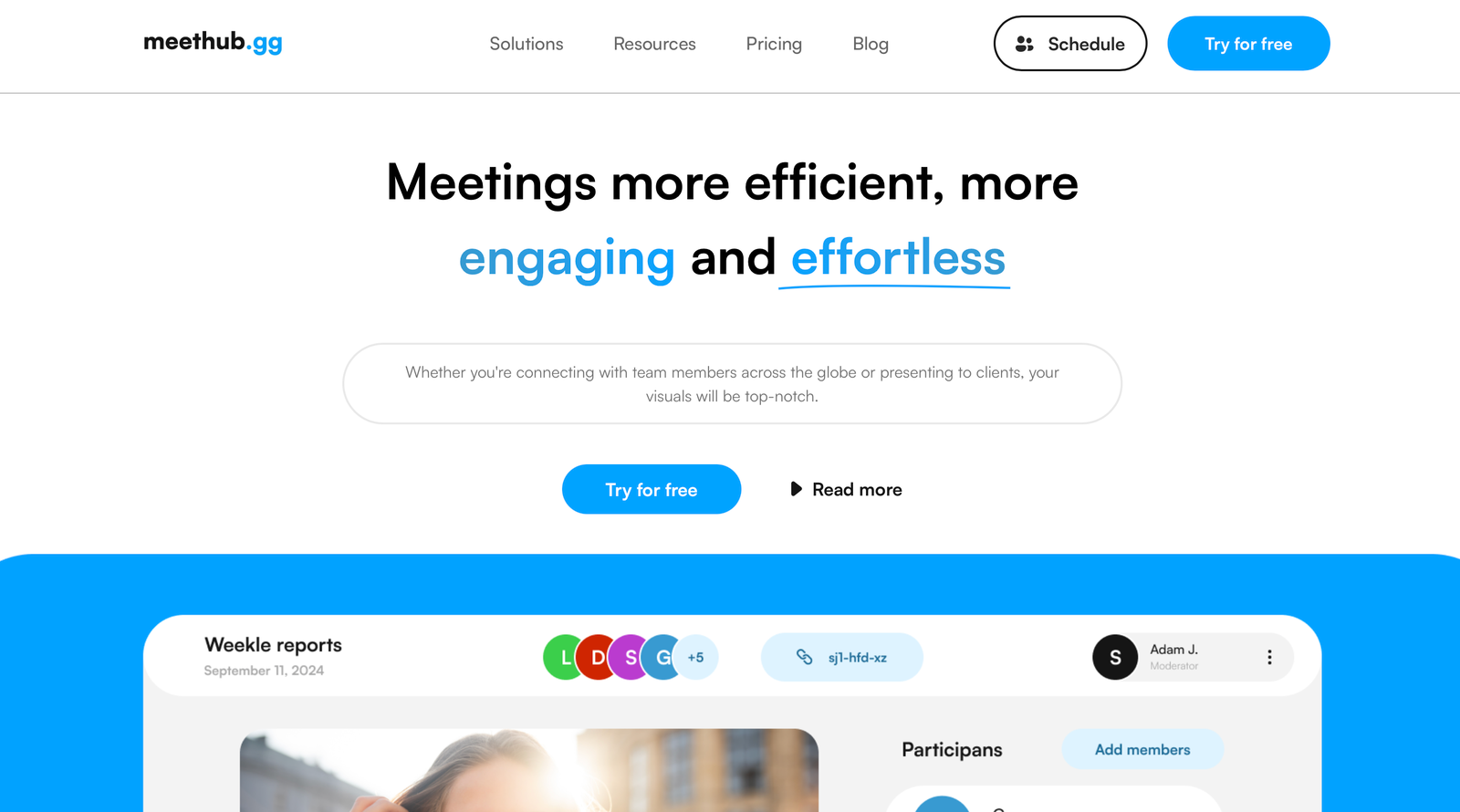
The unsigned Meethub application, once downloaded, prompts users for their macOS password and uses various tools to extract sensitive data, including:
- collection of usernames and passwords from browser login data
- the ability to pull credit card details
- stealing data from a list of installed crypto wallets, among which are Ledger and Trezor
The stolen data is then sent to the attacker’s server.
According to the report, these attacks highlight the growing trend of targeting macOS users in the cryptocurrency industry.
Attackers use sophisticated social engineering techniques to build rapport and gain trust before deploying their infostealers.
Users must remain vigilant and cautious of unsolicited communications, especially cryptocurrency-related ones. They should always verify the legitimacy of applications and be wary of providing sensitive information or credentials.
Are you from the SOC and DFIR Teams? – Analyse linux Malware Incidents & get live Access with ANY.RUN -> Start Now for Free.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.
Read the full article here