A new threat has emerged, targeting unsuspecting iPhone users through the seemingly secure iMefofferssage platform. A sophisticated Phishing-as-a-Service (PhaaS) platform known as ‘Dracula’.
This platform has been implicated in high-profile phishing attacks, leveraging the trust and widespread use of iMessage among iPhone users to perpetrate its schemes.
The Rise of Darcula
Darcula is not your average phishing tool. It represents a new breed of cybercrime, utilizing advanced technologies such as JavaScript, React, Docker, and Harbor—tools more commonly associated with high-tech startups.
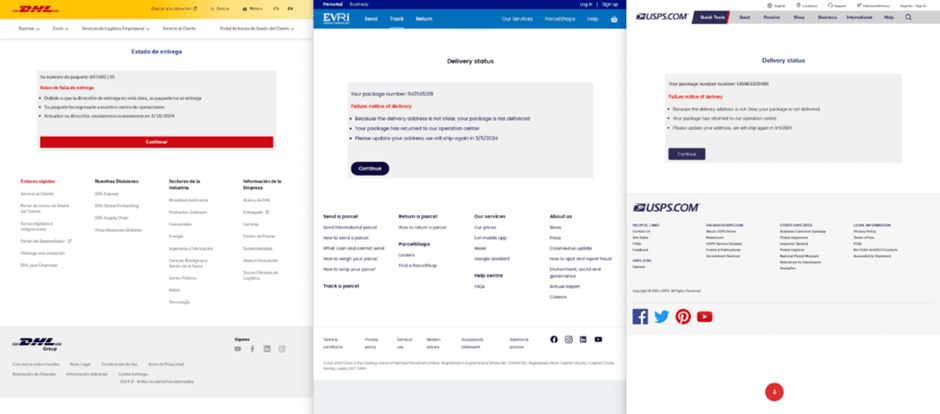
This PhaaS platform has been linked to over 20,000 phishing domains, offering cybercriminals a plethora of branded phishing campaigns at their fingertips.
Unlike traditional phishing methods relying on SMS, Dacula exploits iMessage and RCS (Rich Communication Services), bypassing SMS firewalls and leveraging users’ inherent trust in these platforms.
This approach has proven effective, with Darcula targeting established organizations and postal services in over 100 countries.
A Unique Threat
What sets Dracula apart is its method of operation. Developed by a Telegram user of the same name, this Chinese-language platform offers other criminals a monthly subscription and provides them with hundreds of templates targeting global brands.
These templates are not static; Darcula sites can update in place, adding new features and anti-detection measures without reinstallation.
According to a recent report by Netcraft, the ‘Dracula’ phishing platform, which operates in the Chinese language, uses advanced techniques to target organizations in over 100 countries.
Darcula’s phishing attacks are meticulously crafted, using purpose-registered domains that spoof relevant brand names.
The platform’s use of Cloudflare and other services to mask the underlying server’s IP address further complicates efforts to track and shut down these phishing sites.
The iMessage and RCS Connection
Darcula’s exploitation of iMessage and RCS represents a significant evolution in phishing tactics.
RCS, adopted by Google for Android devices, and iMessage, Apple’s proprietary messaging service, offer end-to-end encryption, making them more secure than traditional SMS.
However, this security feature also makes it challenging for network operators to filter out phishing attempts, playing into the hands of cybercriminals.
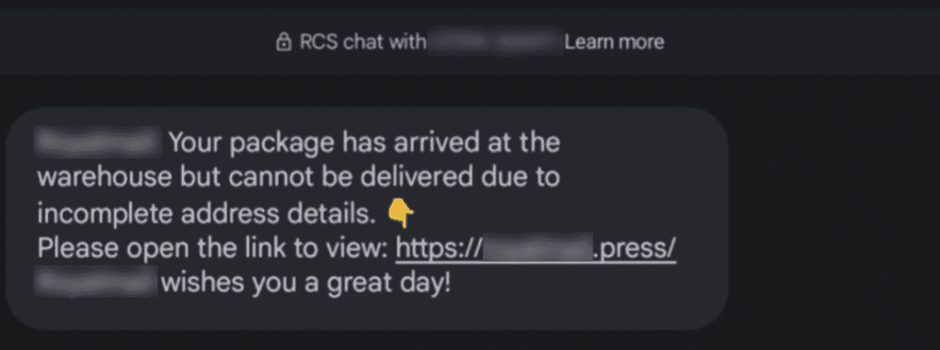
Apple and Google have implemented measures to combat such abuses, but Darcula’s operators have found ways to circumvent these protections.
For instance, they’ve crafted iMessage templates that prompt users to reply, thereby making links in the messages clickable and leading victims to phishing sites.
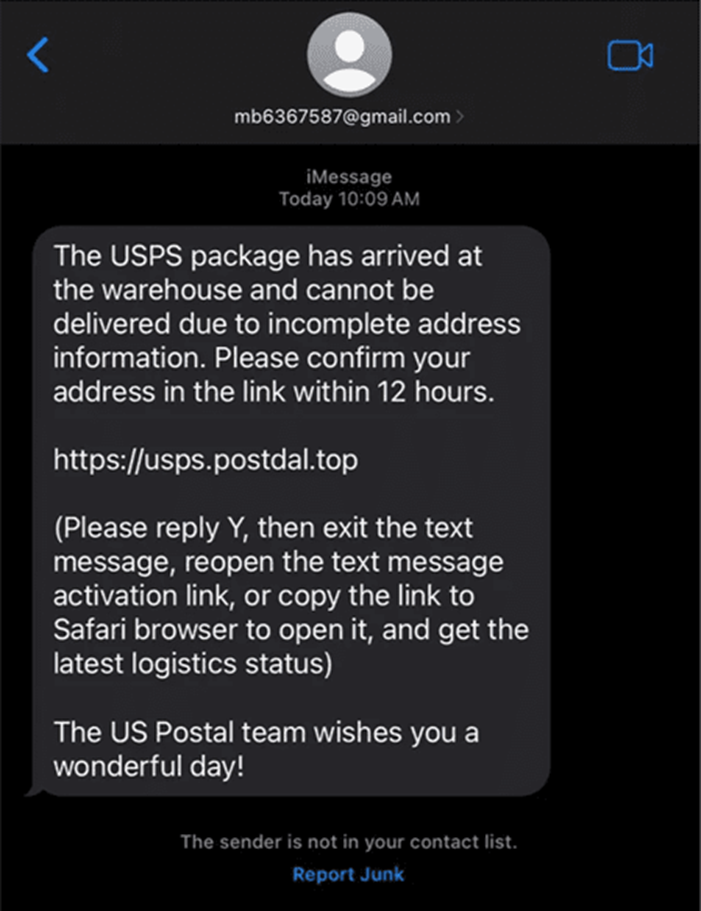
The emergence of Dracula underscores the need for vigilance when receiving unsolicited messages, even on trusted platforms like iMessage.
Users are advised to be skeptical of messages asking for personal information or prompting replies to enable links.
Regularly updating device software and utilizing built-in spam detection features can also help mitigate the risk of falling victim to these sophisticated phishing campaigns.
As the digital landscape continues to evolve, so too do the tactics of cybercriminals.
Staying informed and exercising caution remain the best defenses against the ever-present threat of phishing.
The Darcula PhaaS platform represents a significant threat to digital security, exploiting trusted communication platforms to perpetrate phishing attacks.
By understanding the nature of these attacks and taking proactive steps to protect themselves, iPhone users can help safeguard their personal information against this insidious threat.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.
Read the full article here

