The persistent search for money and the threat actors increasingly becoming more sophisticated are driving the alarming rate of malware change.
Every day, new types of malware are created and put into circulation at an unusual speed, using modern tricks to avoid discovery and overcome security systems, while taking advantage of the most recent system vulnerabilities.
Cybersecurity researchers at Trustwave recently identified that the operators of Agent Tesla added new tools and tactics to its arsenal.
To deliver and perform malicious activities that facilitate criminal actions, threat actors necessitate malware loaders.
These loaders use sophisticated evasion techniques to evade security measures and take advantage of different distribution networks.
On March 8th, 2024, a phishing email was identified by SpiderLabs which set off an infection chain resulting in Agent Tesla being deployed.
The infection began when a phishing email posed as a bank payment notification and delivered an obfuscated, polymorphic loader.
To avoid detection, this loader fetched its payload through proxies using different URLs and user agents before executing the Agent Tesla infostealer in memory.
All data was stolen by Agent Tesla which then sent it through hacked email accounts for secret communication purposes.
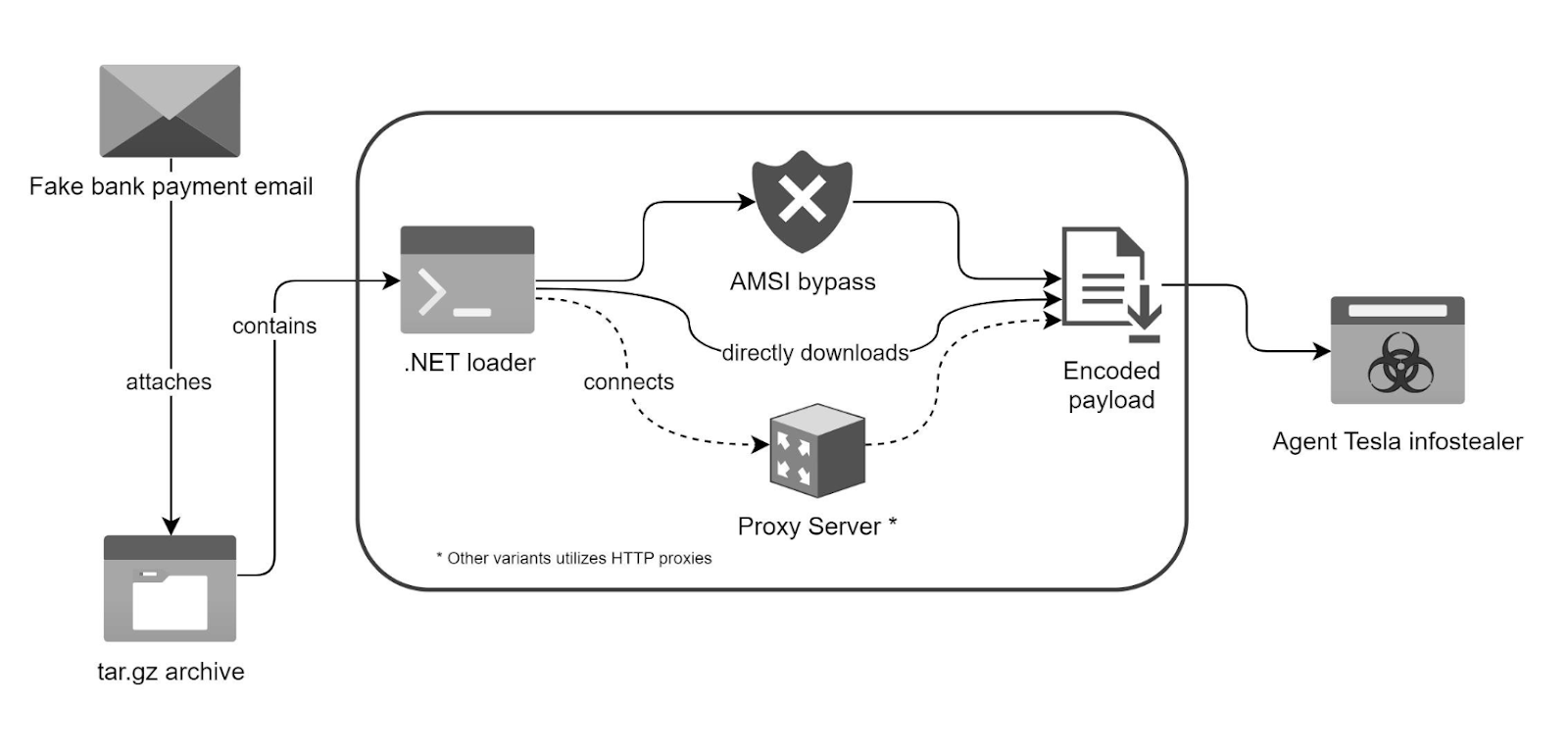
The attack employs a phishing email with a malicious .tar.gz attachment masquerading as a bank payment receipt.
It contains a polymorphic .NET loader that obfuscates and encrypts its configuration data using different decryption routines across variants.
The loader decrypts strings by index-based matching of encrypted data with keys.
It evades detection through techniques like packing, obfuscation, memory permission modifications, and AMSI bypassing.
Key terms reveal it reflectively loads further payloads from a URL specified in the encrypted configuration, reads the report.
To facilitate stealthy payload execution, the loader bypasses AMSI, prepares memory space, and retrieves the payload from a specific URL using a defined user-agent string.
One variant employs an open-source proxy list for obfuscated payload delivery.
The loader extracts the encoded payload from HTML using delimiters, decrypts it via XOR with an embedded key, and reflectively loads the Agent Tesla infostealer into memory by invoking its entry point – all while avoiding disk artifacts for evasiveness.
Agent Tesla is a memory-resident info stealer that conducts keystroke logging, credential theft, and data exfiltration via SMTP, often leveraging compromised email accounts for stealthy communication.
This new Agent Tesla variant employs a .NET loader using deceptive attachment phishing, obfuscation, polymorphic decryption, AMSI bypassing, and reflective loading for evasive payload execution solely in memory.
The versatile loader’s evolution suggests the potential for deploying other malware payloads beyond just Agent Tesla going forward.
IoCs
Loader (Variant 1)
MD5 b69f65b999db695b27910689b7ed5cf0
SHA256 ab9cd59d789e6c7841b9d28689743e700d492b5fae1606f184889cc7e6acadcc
Loader (Variant 2)
MD538d6ebb40197248bc9149adeec8bd0e7
SHA256a02388b5c352f13334f30244e9eedac3384bc2bf475d8bc667b0ce497769cc6a
Packed Agent Tesla
MD52bd452c46a861e59ac151a749047863f, 63f802e47b78ec3d52fe6b403bad823f
SHA256 e3cb3a5608f9a8baf9c1da86324474739d6c33f8369cc3bb2fd8c79e919089c4, f74e1a37a218dc6fcfabeb1435537f709d742505505a11e4757fc7417e5eb962
Unpacked Agent Tesla
MD5 3637aa1332b312fe77cc40b3f7adb8dc, 37b38ae2d99dd5beb08377d6cbd1bccd
SHA256 3a1fe17d53a198f64051a449c388f54002e57995b529635758248dc4da7f5080, a3645f81079b19ff60386cb244696ea56f5418ae556fba4fd0afe77cfcb29211
SMTP Exfiltration
Sender email: merve@temikan[.]com[.]tr
Receiver email: frevillon[.]acsitec@proton[.]me
Download URLs
hxxps[://]artemis-rat[.]com/get/65f0e7dd5b705f429be16c65
hxxps[://]artemis-rat[.]com/get/65eb0afe3a680a9851f23712
User-Agent
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, killer Gecko) Chrome/58.0.3029.110 Safari/537.3
List of Proxy Servers
hxxps[://]github[.]com/TheSpeedX/PROXY-List/blob/master/hxxp[.]txt
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter
Read the full article here