Researchers at Akamai have unveiled a new technique that could potentially put millions of Windows domains at risk.
This technique exploits the Dynamic Host Configuration Protocol (DHCP) administrators group to escalate privileges within Active Directory (AD) environments, a cornerstone of network management in numerous organizations worldwide.
The DHCP server, a critical component in network management, is responsible for assigning IP addresses to devices on a network.
However, when this server role is installed on a Domain Controller (DC), it opens up a Pandora’s box. Researchers have found that this configuration can be manipulated to grant attackers domain admin privileges, essentially handing them the keys to the kingdom.
Microsoft DHCP Servers
This technique does not exploit a vulnerability in the traditional sense but abuses legitimate features, making it a particularly insidious threat.
With Microsoft DHCP servers running in approximately 40% of the networks monitored by Akamai, the potential impact is vast.
Beyond privilege escalation, the technique can also be used to create a stealthy domain persistence mechanism.
Free Webinar : Mitigating Vulnerability & 0-day Threats
Alert Fatigue that helps no one as security teams need to triage 100s of vulnerabilities.
:
- The problem of vulnerability fatigue today
- Difference between CVSS-specific vulnerability vs risk-based vulnerability
- Evaluating vulnerabilities based on the business impact/risk
- Automation to reduce alert fatigue and enhance security posture significantly
AcuRisQ, that helps you to quantify risk accurately:
This means that attackers can maintain their foothold within a network undetected, posing a significant threat to organizational security.
Given the nature of this technique, there isn’t a straightforward fix such as a patch. However, Akamai researchers have outlined detailed steps for mitigation and detection to help organizations protect themselves.
These include identifying risky DHCP configurations, mitigating relay attacks against AD Certificate Services (AD CS), practicing DHCP administrator’s group hygiene, using network segmentation, and identifying DNS anomalies, researchers said.
DHCP Coerce Technique
Dubbed “DHCP Coerce,” the technique allows attackers to coerce a DHCP server into authenticating with a machine under their control.
This can then be leveraged in a Kerberos relay attack to gain control over the server.
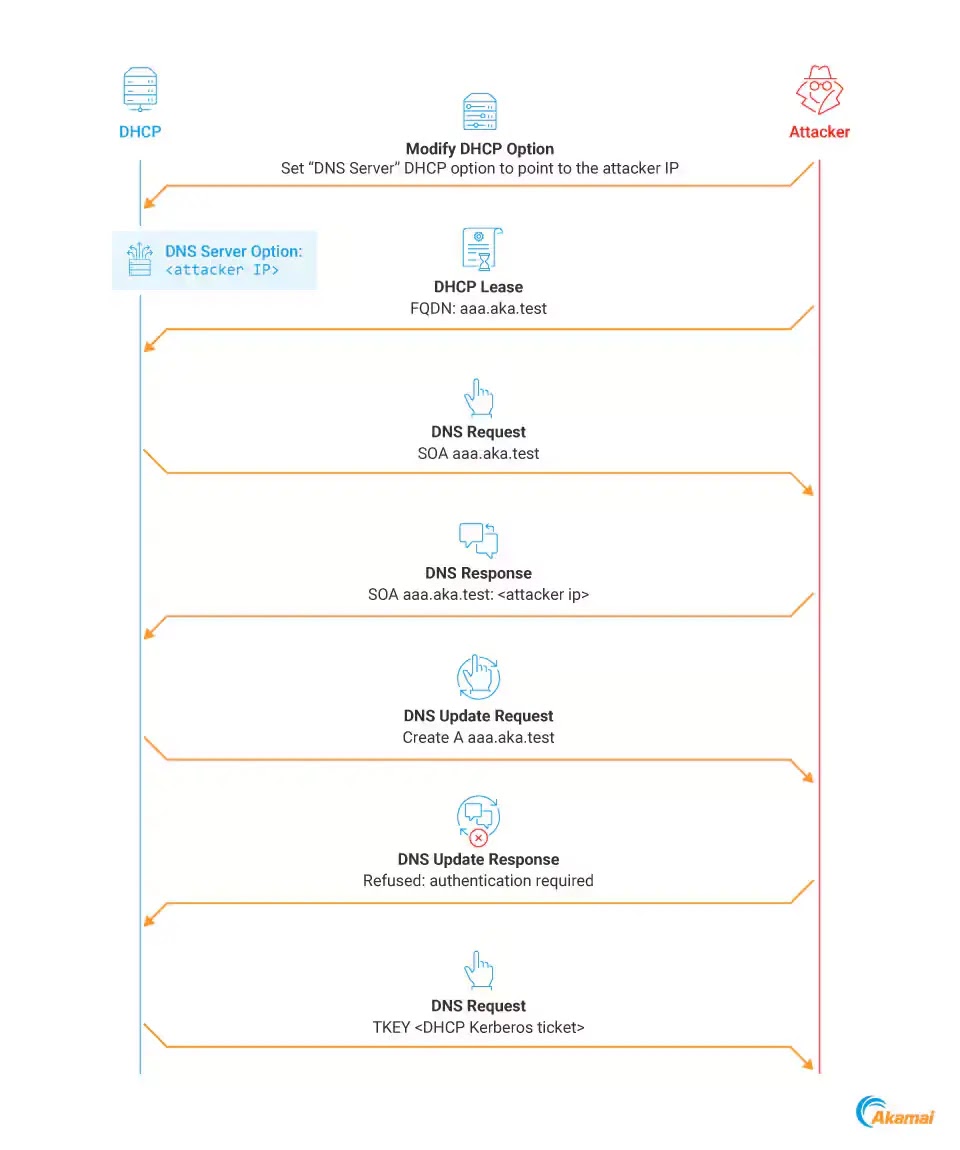
The implications are particularly dire if AD Certificate Services are used within the environment, as this can lead to a full domain compromise.
This discovery serves as a stark reminder of the importance of vigilance in network security.
Organizations are urged to review their DHCP server configurations, particularly those installed on DCs, and implement the recommended defensive measures.
As the digital landscape continues to evolve, so too do the tactics of those with malicious intent.
It is incumbent upon security professionals to stay ahead of these threats, ensuring the integrity and security of their networks.
The DHCP administrators group provides essential functionality, it also presents a potential risk if not managed with caution.
Akamai’s research highlights the need for a balanced approach to access management, one that secures the network without hindering operational efficiency.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.
Read the full article here

