AI (Artificial Intelligence) systems can process large amounts of data and uncover threats that human beings might overlook.
This makes quick action possible, as AI can monitor network traffic, user activities, and system logs and identify abnormal actions, intrusions, and cyberattacks.
As many cybersecurity tasks could be automated. Not only this even, it also improves efficiency, and due to this, there is less probability of human mistakes.
Mitigating Vulnerability & 0-day Threats
Alert Fatigue that helps no one as security teams need to triage 100s of vulnerabilities.
:
- The problem of vulnerability fatigue today
- Difference between CVSS-specific vulnerability vs risk-based vulnerability
- Evaluating vulnerabilities based on the business impact/risk
- Automation to reduce alert fatigue and enhance security posture significantly
AcuRisQ, that helps you to quantify risk accurately:
A Spanish pentester with a “luijait” alias on Github recently unveiled an AI OSINT tool dubbed “DarkGPT” that helps detect leaked databases.
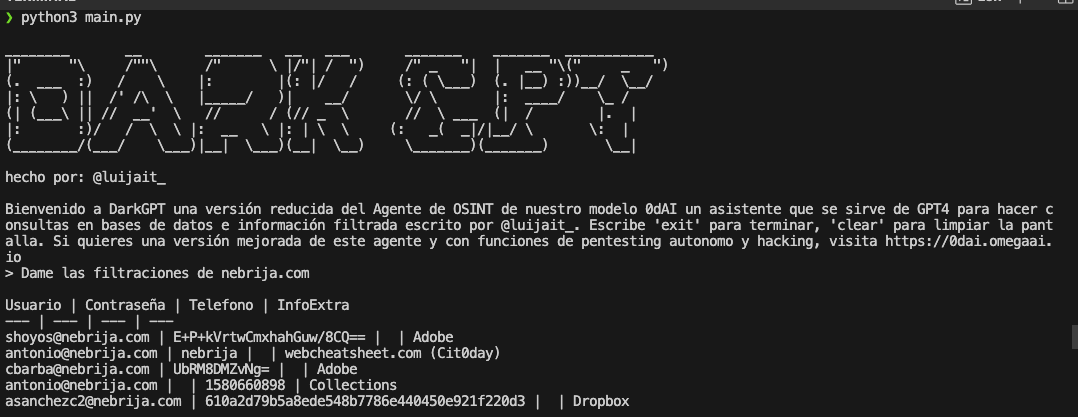
Based on GPT-4-200K, DarkGPT is an AI (Artificial Intelligence) assistant that can run queries on databases that have been compromised.
Its ability to learn and adapt is another important advantage of AI in cybersecurity.
On the other hand, as new threats come up, AI systems may be trained to identify and respond to these threats.
This is especially critical in a fast-changing cyber threat landscape where conventional security measures are often inadequate.
The security researcher affirmed that to install the AI OSINT tool, “DarkGPT,” users must have Python installed on their system, as with Python 3.8 and higher versions, this project has been tested.
Environment Setup
Here below, we have mentioned the complete setup:–
First of all, by executing the following command in your terminal, you have to clone the GitHub repository to your local machine
git clone https://github.com/luijait/DarkGPT.git cd DarkGPT
- For the script to work correctly, you have to configure the environment variables.
- Locate the .env.example file in the project directory.
- Create a new file named .env in the same directory.
- Open the .env file and add your DeHashed API key by replacing “your_dehashed_api_key_here” with your actual API key:
DEHASHED_API_KEY=”your_dehashed_api_key_here”
- Run the following command to install the required Python packages
pip install -r requirements.txt
- After that now you have to execute the main script by running
python3 main.py
The DarkGPT could be a game-changer relief tool for security researchers as it will help them in their traditional OSINT processes and make them more efficient.
With Perimeter81 malware protection, you can block malware, including Trojans, ransomware, spyware, rootkits, worms, and zero-day exploits. All are incredibly harmful and can wreak havoc on your network.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.
Read the full article here

