Microsoft Security Copilot, a generative AI solution for security professionals, will be generally available in April 2024.
It uses threat intelligence and large language models to analyze vast amounts of data (78 trillion daily signals) and provide security teams with insights and guidance.
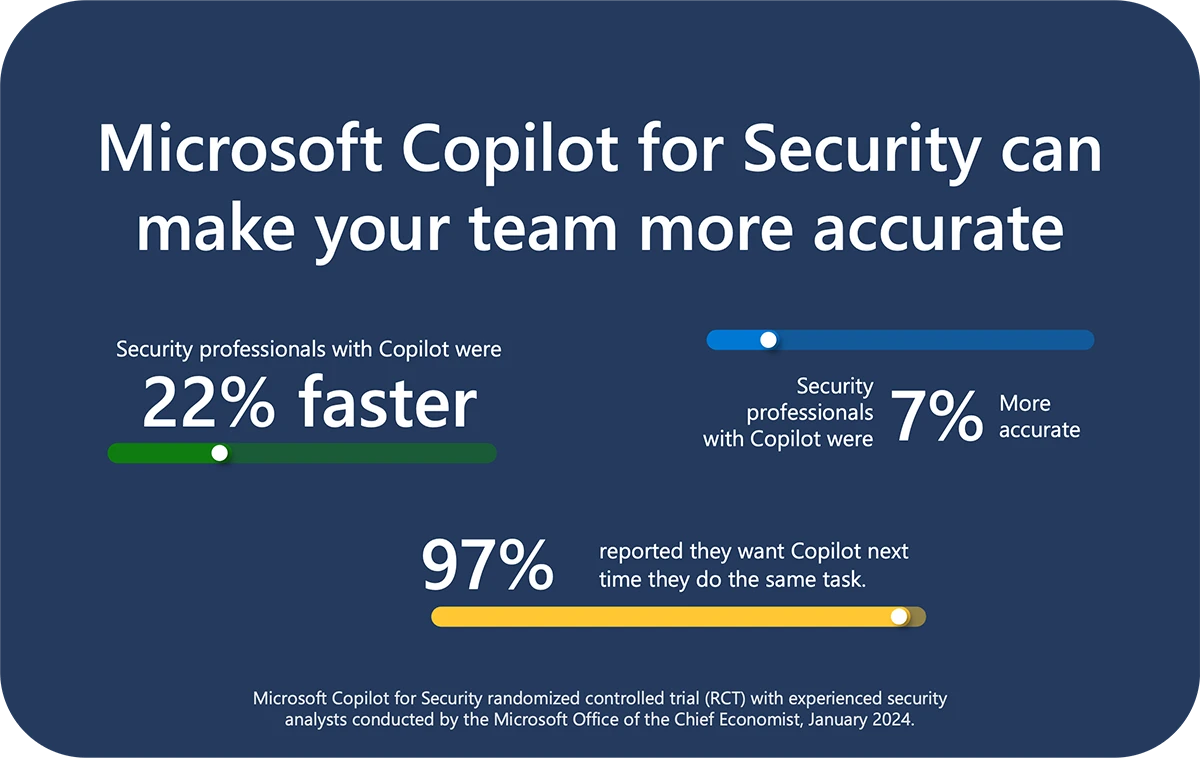
Studies show that Copilot improves efficiency (22% faster) and accuracy (7% more accurate) for experienced security analysts, with 97% wanting to continue using it.
Utilizing this technology enables security experts of varying levels of experience and encourages teamwork among team members.
Global Reach and New Product Innovations of Microsoft Copilot
Microsoft’s AI-powered security solution, Copilot for Security, will launch a pay-as-you-go licensing model on April 1, 2024, making the tool more accessible to various organizations.
Copilot can process information and respond in eight languages, and its interface supports 25 languages, catering to users across North and South America, Europe, and Asia.
A vast ecosystem of over 100 partners, including security service providers and software vendors, can assist with adoption.

A recently released AI-powered security solution offers new features, including the ability to create custom prompts for everyday tasks, integrate with existing knowledge bases, and leverage support for eight languages.
Third-party integrations, connections to external attack surface data, and insights from Microsoft Entra logs enhance threat hunting and investigation capabilities, whereas usage reporting allows for optimizing team workflows.
Expanding End-to-End Protection for Everyone in the Age of AI
Microsoft‘s generally available Copilot for Security aims to enhance security operations through AI-powered assistance that offers two interfaces: a standalone portal and an embedded experience within existing security products.
Integration with Microsoft Defender SIEM and XDR empowers analysts with functionalities like threat investigation summaries, guided response workflows, and natural language support for queries and scripts.
Copilot also assists in user risk assessment, prioritizes data security alerts, and simplifies endpoint management by providing root cause analysis and device comparisons.
According to Mario Ferket, Chief Information Security Officer, Dow:

It aims to empower businesses using AI responsibly by offering security features within their product portfolio, including threat discovery for potential data leaks and unauthorized app access.
Security teams gain capabilities to protect AI applications and the data they process, along with governing user interactions and logging activities that allow for detecting policy violations and investigating incidents.
The recent integration of threat detections for Copilot in Defender for Cloud Apps strengthens overall security, enabling secure work with both sensitive and non-sensitive data.
Microsoft has announced several new security features. Microsoft Security Exposure Management provides a unified view of an organization’s attack surface and critical assets.
Integrating Microsoft Purview and Entra Conditional Access allows for automatic responses to insider risks. Microsoft Communication Compliance now offers sentiment analysis to improve risk detection.
Microsoft Intune gained new features for application management, cloud PKI, and advanced analytics, and Microsoft Copilot for Security integrates various Microsoft security products into a single solution.
With Perimeter81 malware protection, you can block malware, including Trojans, ransomware, spyware, rootkits, worms, and zero-day exploits. All are incredibly harmful and can wreak havoc on your network.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.
Read the full article here