Threat actors target Notepad++ as it is a widely used text editor among developers and users, offering a large potential victim pool.
Exploiting vulnerabilities in Notepad++ can provide access to sensitive data or even systems as well.
Besides this targeting popular software increases the likelihood of successful attacks and intensifies the impact.
Cybersecurity researchers at Kaspersky Lab recently discovered that threat actors are actively targeting and attacking developers via malicious Notepad++ websites.
Technical analysis
Malvertising lures victims via malicious ads atop search results, as the top results seem trustworthy.
Last year, RedLine stealer spread via Google Ads malvertising campaign using typosquatting.
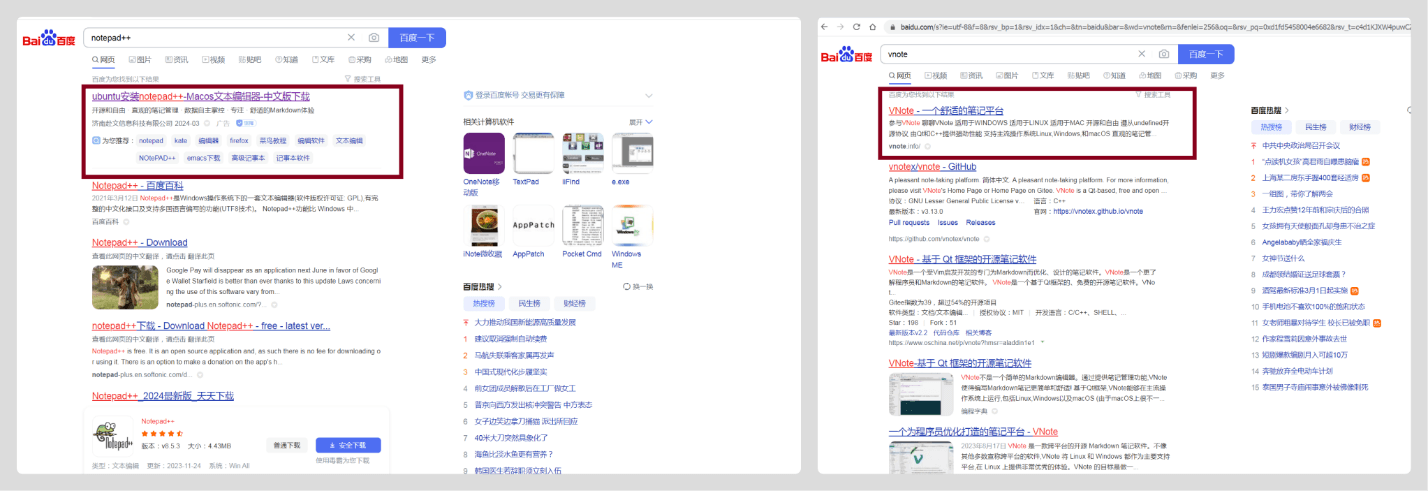
A similar threat now affects major Chinese search engines.
Threat actors are distributing modified versions of text editors, one via ad section, another atop results.
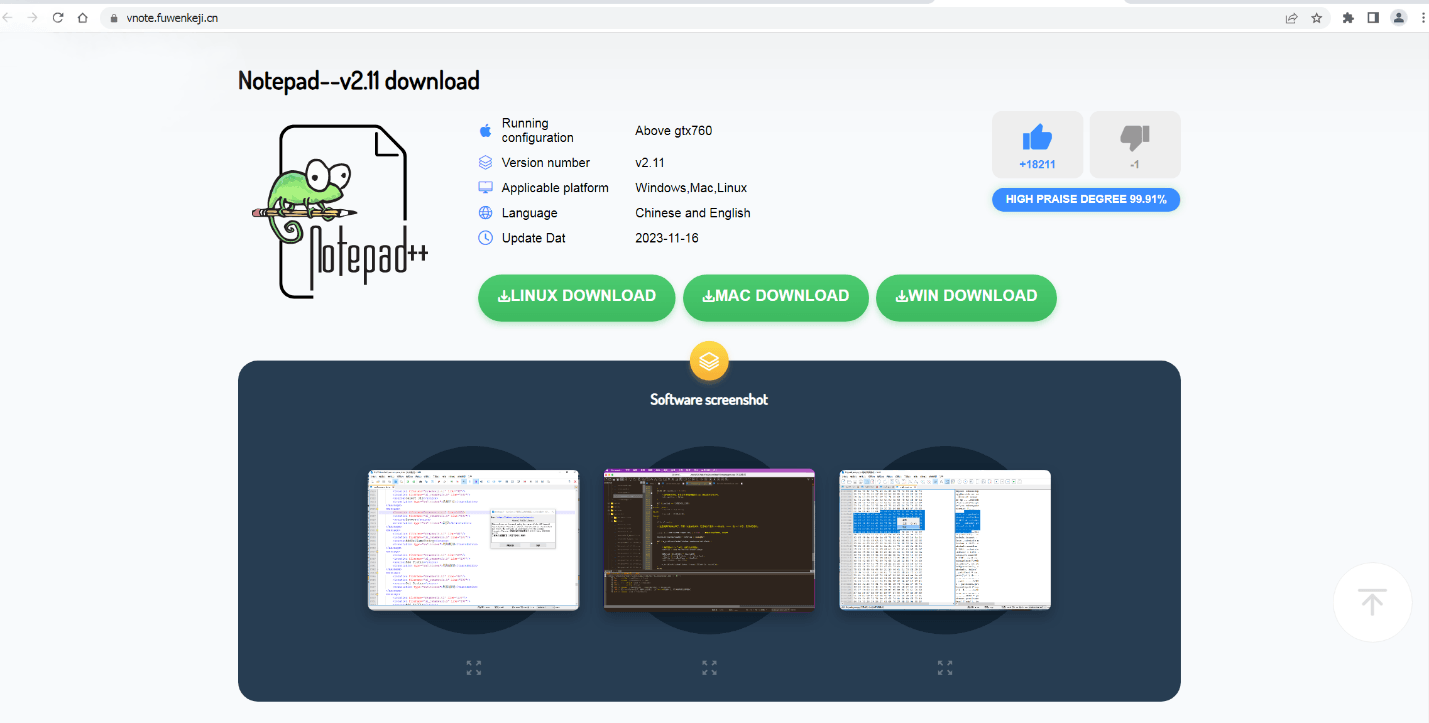
The malicious Notepad++ site uses an ad block.
The site has amusing inconsistencies – the URL mentions “vnote”, the title offers “Notepad–” (Notepad++ analog), and the image shows Notepad++.
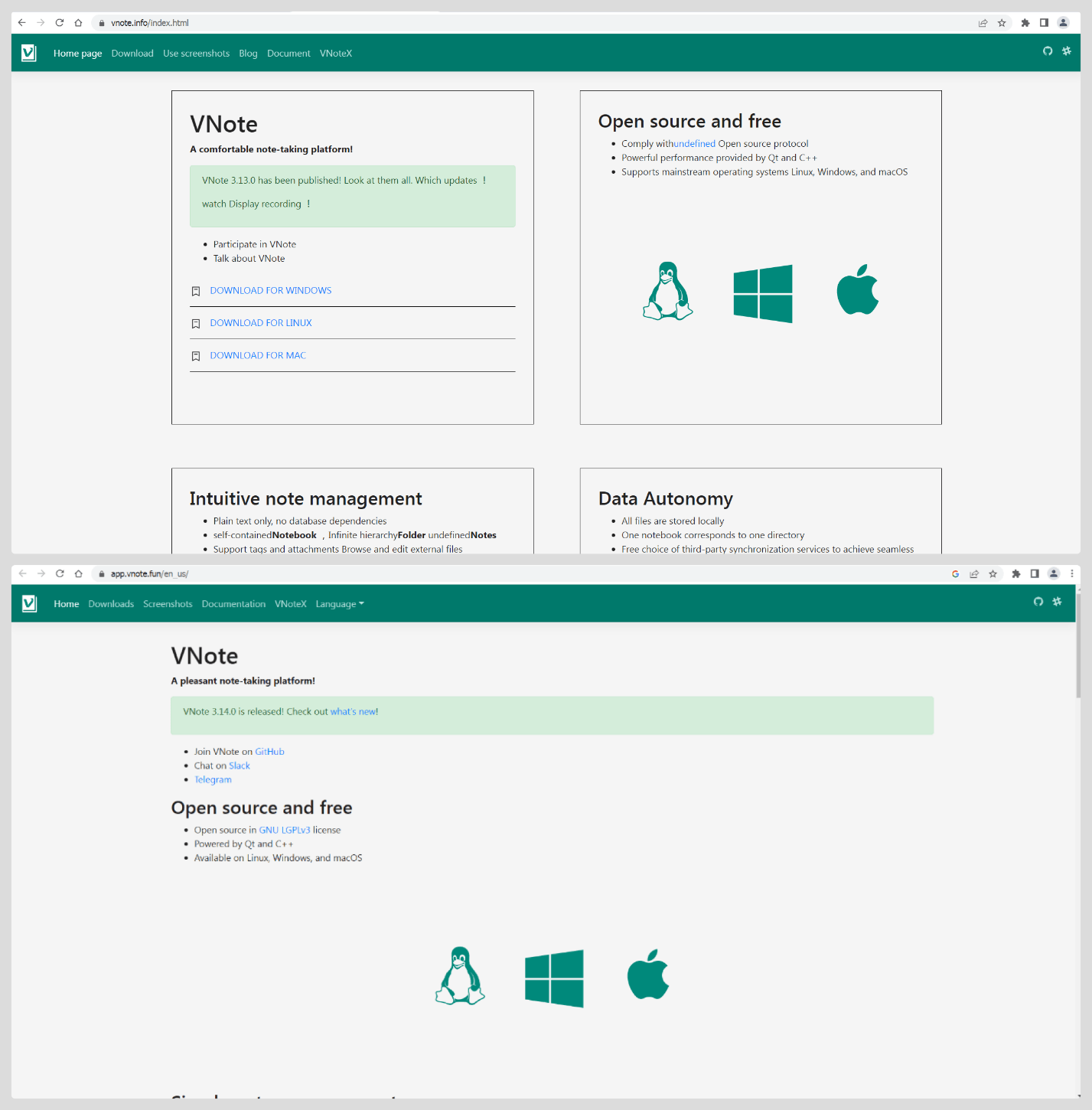
But downloads contain Notepad–, besides this, the site offers installers for Windows, Linux, and macOS but only macOS, and Linux links are malicious.
The downloaded apps differ from the originals, and the malicious Linux and macOS versions have similar functionality.
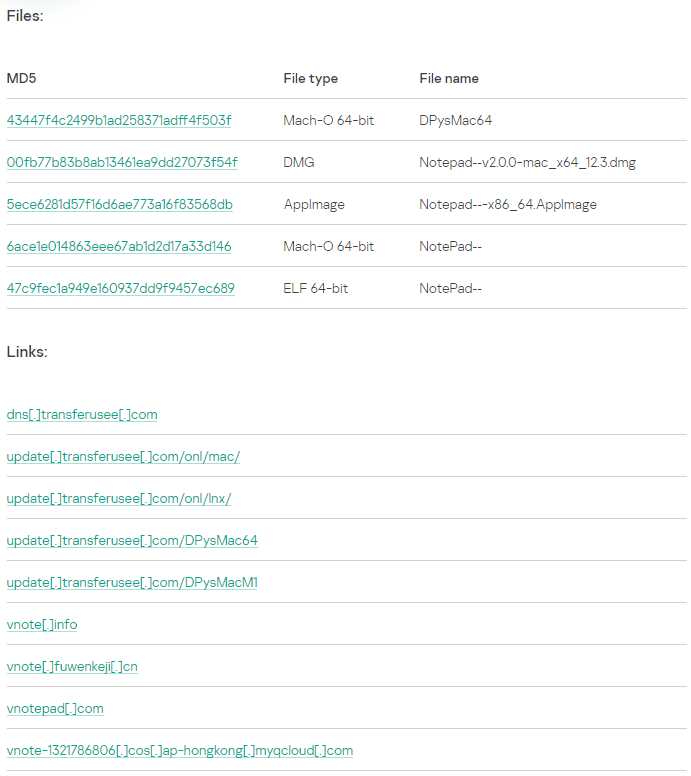
On examining the macOS version (MD5: 00fb77b83b8ab13461ea9dd27073f54f) – it’s been found that the DMG image contents are identical to the original 2.0.0, except executable NotePad– (MD5: 6ace1e014863eee67ab1d2d17a33d146).
Before launch, a suspicious Uplocal class was initialized which is absent in the source code.
Researchers couldn’t analyze the downloaded file as it was unavailable.
However, the server has subdomain dns[.]transferusee[.]com accessed by Mach-O file DPysMac64 (MD5: 43447f4c2499b1ad258371adff4f503f), previously uploaded to VirusTotal but undetected during investigation.
The same server hosts a mysterious updater download and DPysMac64 file, suggesting that the updater leads to DPysMac64 loading.
DPysMacM1 is identical to DPysMac64 for Apple Silicon processors.
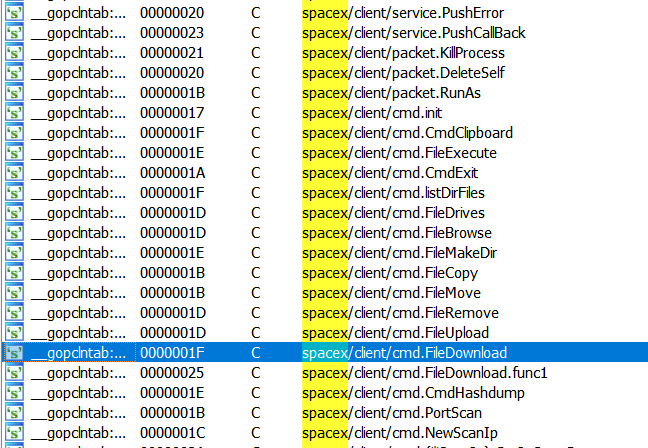
It’s a CobaltStrike-like backdoor, open-source Geacon implementation written in Go with matching code/functions despite Geacon references being removed.
Moreover, it has normal and service launch modes, C2 comms via HTTPS to dns[.]transferusee[.]com.
Threat actors named the remote command execution functionality “spaces.”
While uncertain about prior vnote[.]info downloads, it’s been found that both sites distribute the same applications.
Interestingly, the modified NotePad– executable had “About” text linking to vnotepad[.]com – another vnote[.]info copy with invalid cert issued for vnote[.]info, confirming the connection between cases.
![Certificate used by the site vnotepad[.]com (Source - Kaspersky Lab)](https://cyberaffairs.com/wp-content/uploads/2024/03/N-Qnl2KQS9rCZrl6d20YAOVOlRO9EOquwIrWL0Z4XvaN9w75DZL_wFR30nzLk18_TGm9uT29jqY-S6Z3X58sgfbRMv92MwHAHUaGB0g-frRgfflhwgKTs0GK84KgTxDvni9vALuMrwasQkHDquDkqi4.png)
There is a high probability that modified VNote editors aim to deliver the next infection stage, like NotePad–. Identical Linux/macOS app changes suggest a possible Linux backdoor mirroring macOS one.
IoCs
With Perimeter81 malware protection, you can block malware, including Trojans, ransomware, spyware, rootkits, worms, and zero-day exploits. All are incredibly harmful and can wreak havoc on your network.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.
Read the full article here

