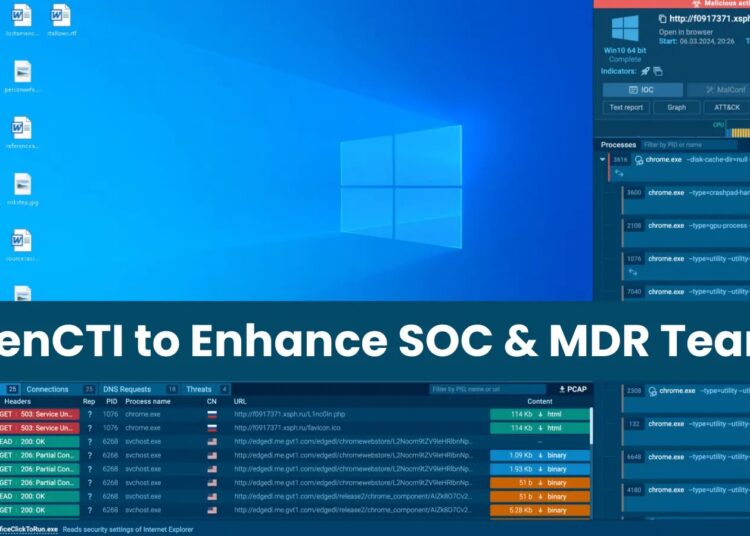
ANY.RUN integrates with OpenCTI to streamline threat analysis, which allows enriching OpenCTI observations with data directly from ANY.RUN analysis.
OpenCTI is a central hub that collects threat data from various sources, like ANY.RUN, through connectors, stores this data as “observations,” including indicators like file hashes and IP addresses.
ANY.RUN is a cloud-based malware analysis sandbox that assists security teams in investigating suspicious files that utilizes YARA and Suricata rules for initial detection within 40 seconds and offers real-time interaction with the virtual environment.
It allows analysts to bypass automated malware techniques and delve deeper into analyzing sophisticated threats and its cloud-based nature also eliminates setup and maintenance burdens for security teams.
“ANY.RUN released connectors for MITRE ATT&CK techniques and tactics, an ANY.RUN TI Feeds connector that imports data into OpenCTI once every 24 hours, and an ANY.RUN sandbox connector that you can use to enrich observations with data from sandbox analysis tasks, like malware family labels and maliciousness scores.”
The new integration offers two main functionalities:
- Automatic data import: ANY.RUN Threat Intelligence Feeds connector automatically imports data into OpenCTI daily.
- Interactive analysis and enrichment: Its sandbox connector allows enriching observations with data from malware execution in a sandbox environment that includes malware labels, malicious scores, and indicators like tactics, techniques, and procedures (TTPs) used by the malware.
This integration combines and analyzes data from different sources to provide SOCs and MDR teams with a centralized platform for faster and more comprehensive threat analysis.
Malware analysis can be fast and simple. Just let us show you the way to:
- Interact with malware safely
- Set up virtual machine in Linux and all Windows OS versions
- Work in a team
- Get detailed reports with maximum data
If you want to test all these features now with completely free access to the sandbox:
ANY.RUN enrichment connector in OpenCTI
An OpenCTI observation can be transformed into a full-fledged indicator by leveraging the ANY.RUN sandbox connector. This involves submitting the observation to ANY.RUN and creating a virtual machine to analyze the artifact’s behavior.
During this analysis, ANY.RUN extracts Indicators of Compromise (IOCs) from network traffic, memory dumps, and observed activity, then links back to the original observation within OpenCTI, enriching it with valuable threat data.
The observation, now an indicator laden with details, can be forwarded to the SIEM or SOAR system, which triggers the creation of an incident ticket, prompting further investigation by security responders.
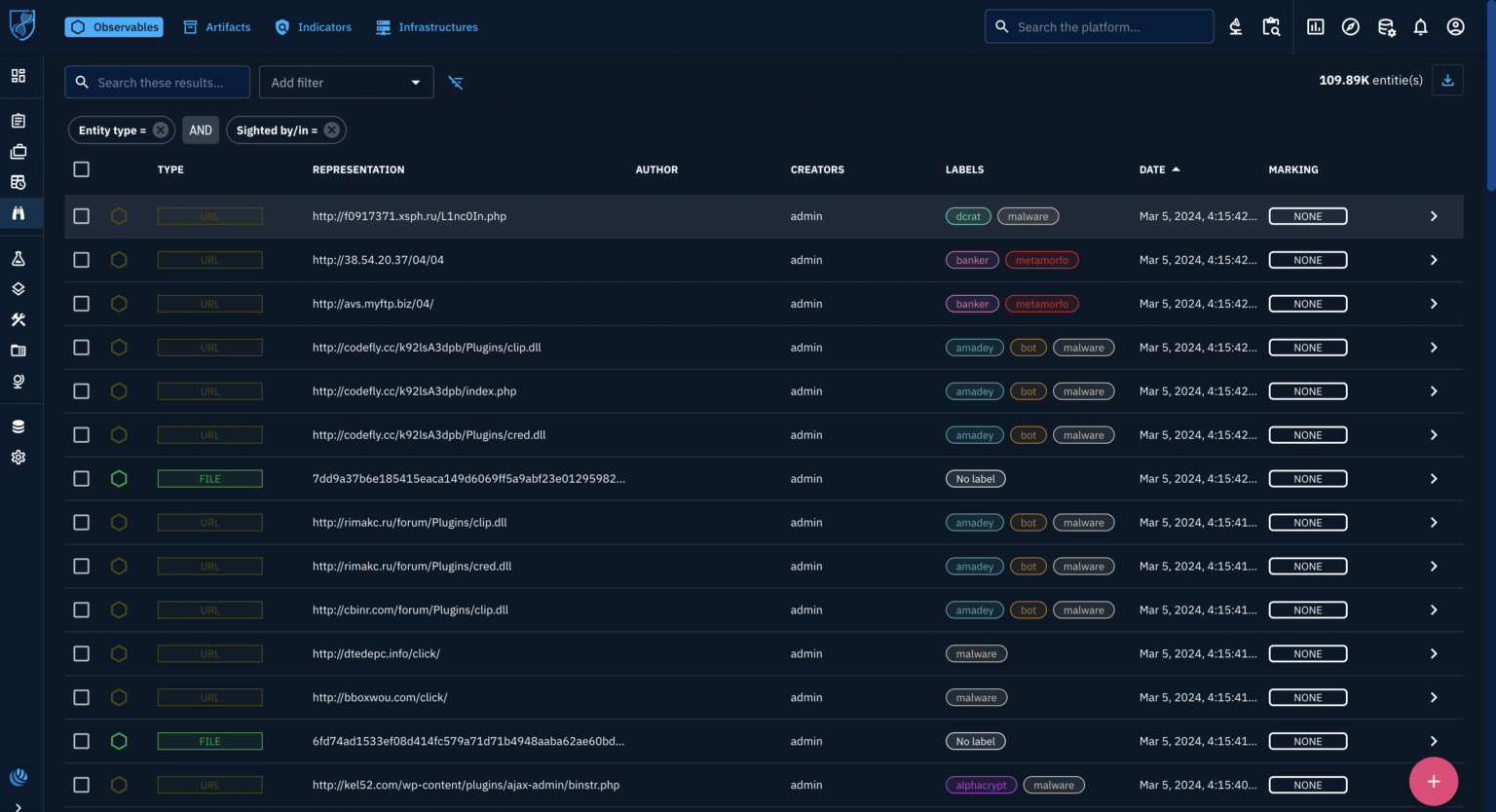
The user aims to enrich an observable (indicator) within the OpenCTI platform, navigates to the list of observables, and selects one by observing the empty malware analysis details and references they choose to leverage an enrichment connector.
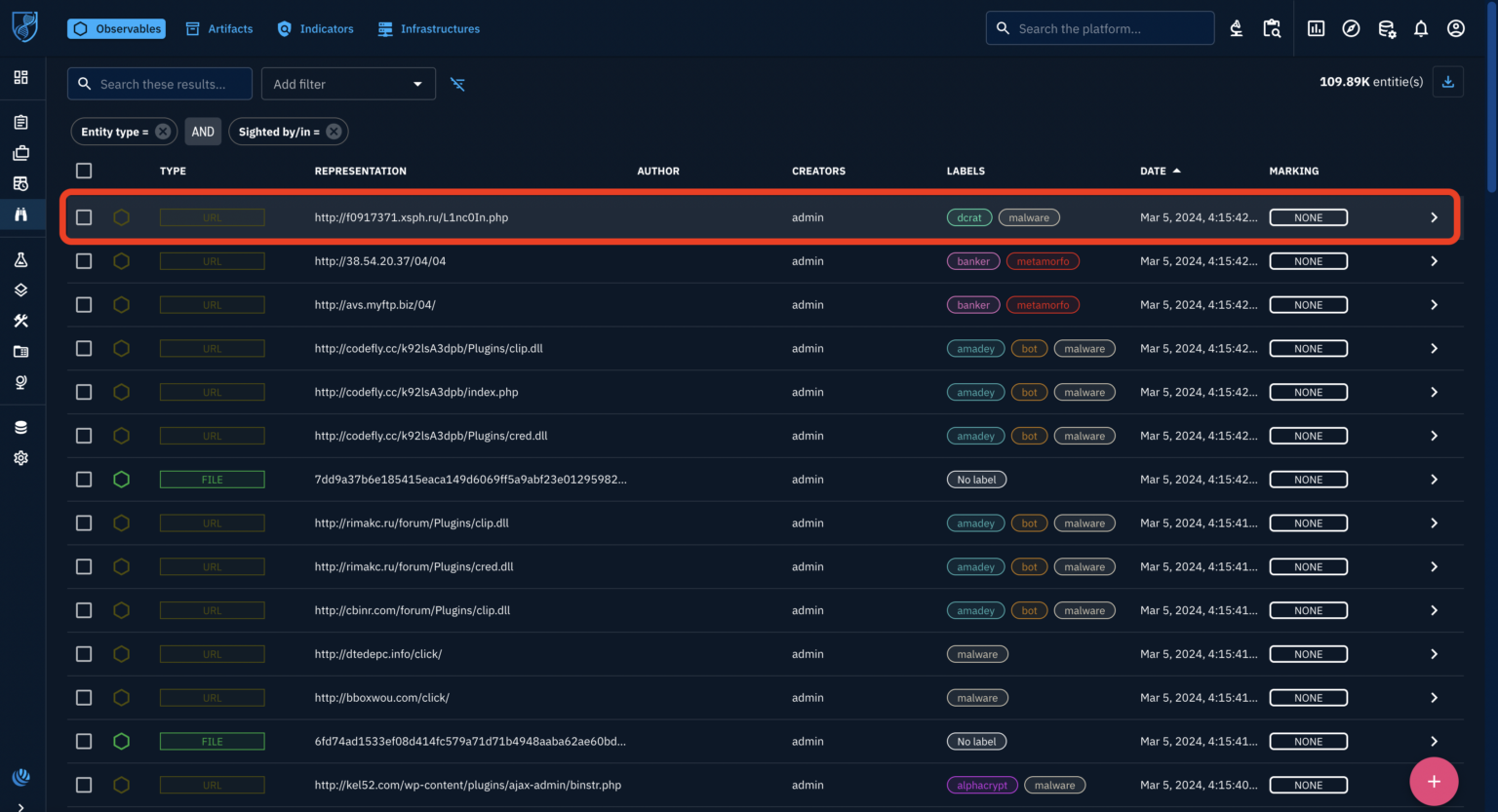
Functionality can be accessed via a button on the top right corner, enables fetching additional information from external sources, potentially including malware analysis reports and related references.
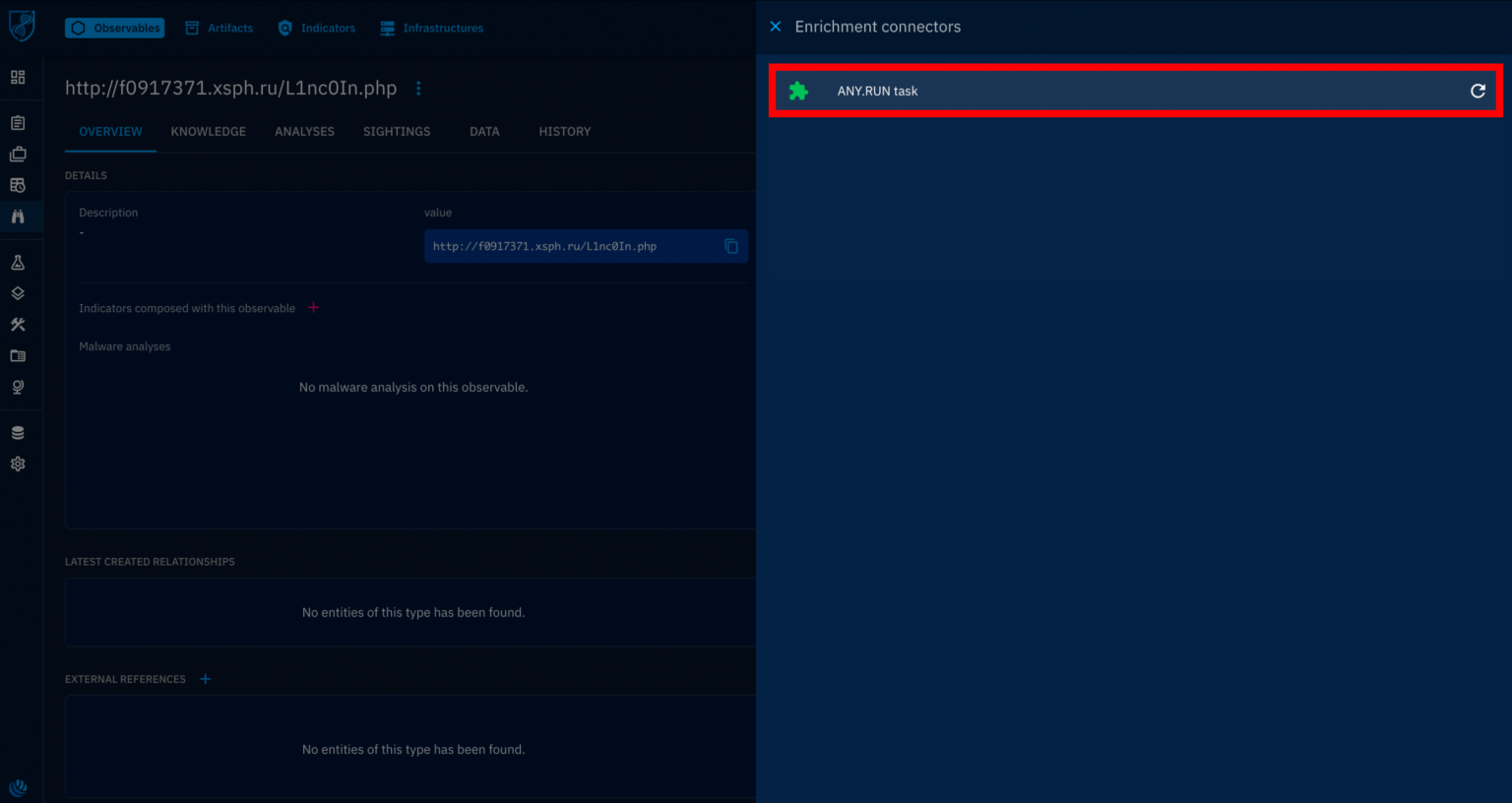
The ANY.RUN enrichment connector automatically retrieves information about a provided observable (e.g., URL, IP address) and enhances its data with additional details.
Clicking the refresh button triggers the connector to work in the background and can establish connections between the observable and known tactics, techniques, and procedures (TTPs) used by adversaries.
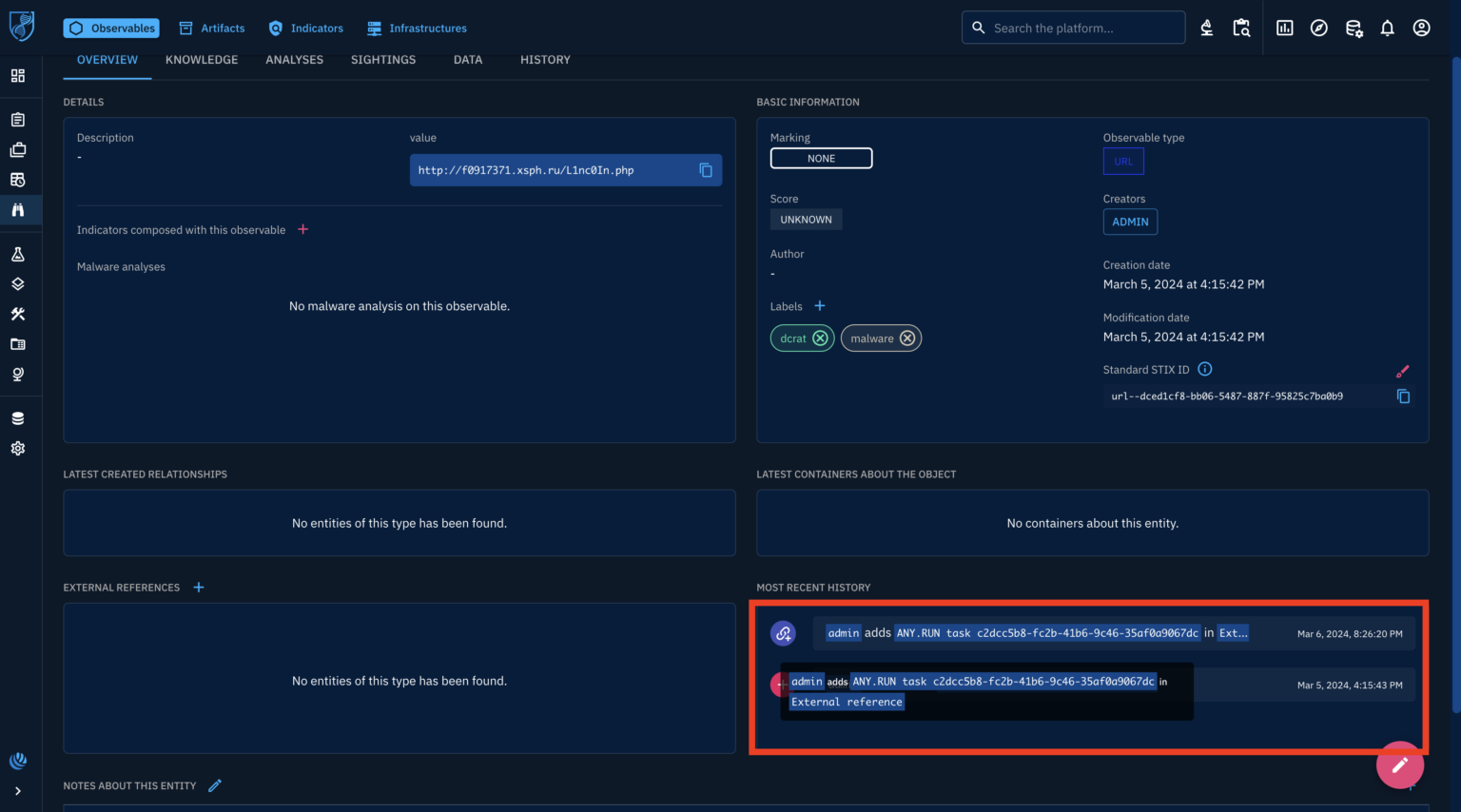
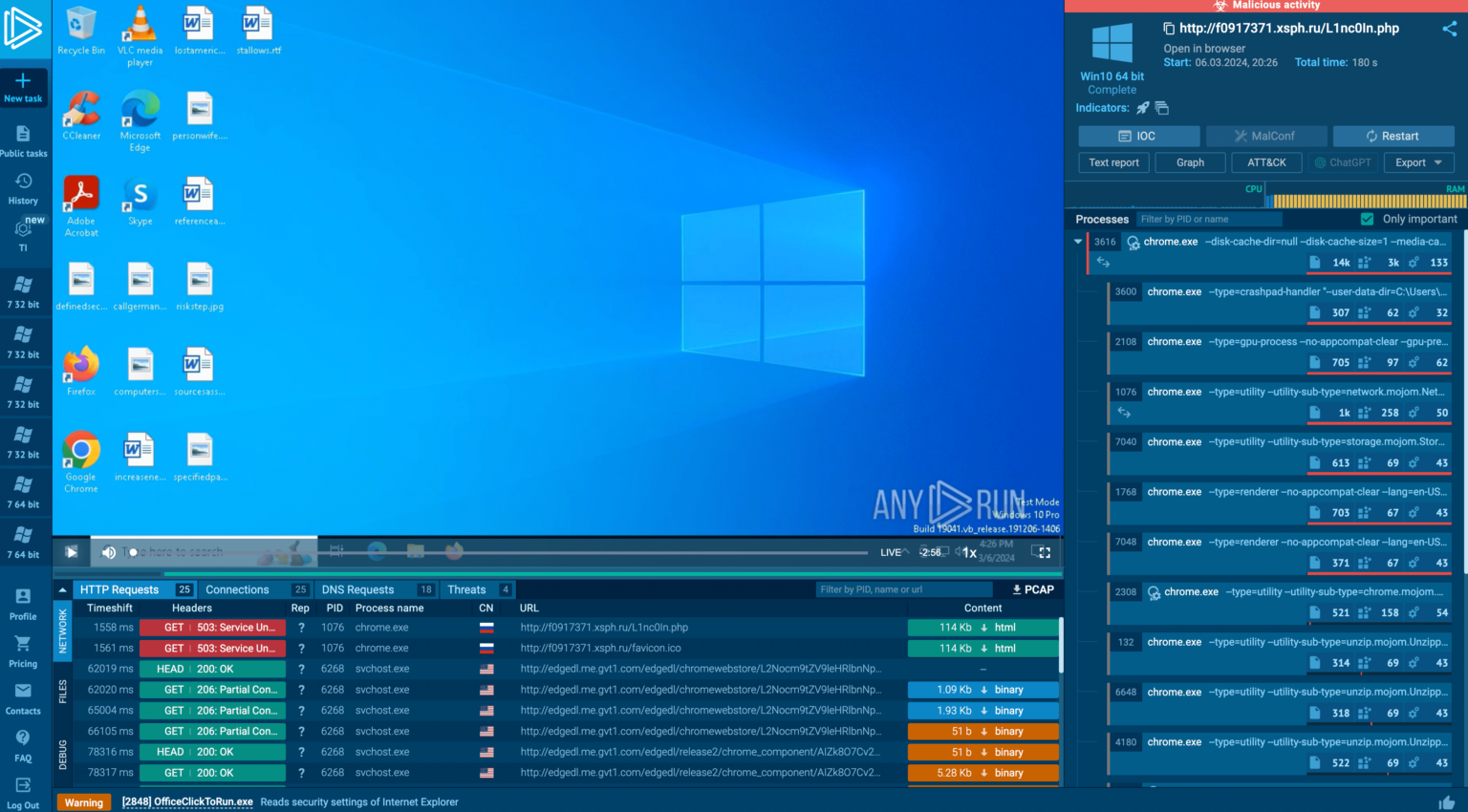
External references like sandbox tasks might be identified, allowing for further investigation by clicking the corresponding link and this task is launched in ANY.RUN.
What is ANY.RUN?
ANY.RUN is a cloud-based malware lab that does most of the work for security teams. 400,000 professionals use ANY.RUN platform every day to look into events and speed up threat research on Linux and Windows cloud VMs.
Advantages of ANY.RUN
- Real-time Detection: ANY.RUN can find malware and instantly identify many malware families using YARA and Suricata rules within about 40 seconds of posting a file.
- Interactive Malware Analysis: ANY.RUN differs from many automated options because it lets you connect with the virtual machine from your browser. This live feature helps stop zero-day vulnerabilities and advanced malware that can get past signature-based protection.
- Value for money: ANY.RUN’s cloud-based nature makes it a cost-effective option for businesses since your DevOps team doesn’t have to do any setup or support work.
- Best for onboarding new security team members: ANY. RUN’s easy-to-use interface allows even new SOC researchers to quickly learn to examine malware and identify signs of compromise (IOCs).
Are you from SOC and DFIR Teams? – Analyse Malware Incidents & get live Access with ANY.RUN -> Start Now for Free
Read the full article here