At Google’s LLM bugSWAT event in Las Vegas, researchers uncovered and reported bugs in the company’s Bard AI (formerly known as Gemini) and received a $50,000 reward.
Roni Carta, Justin Gardner, and Joseph Thacker worked together to hack on Bard and Google Cloud Console.
In particular, the security flaws the researchers found might have allowed for DoS attacks, the exfiltration of user data, and access to uploaded images belonging to a specific user.
“The vision function is designed to process and describe any uploaded image.
We observed, however, a major flaw. When we exploited this flaw, it granted us access to another user’s images without any permissions or verification process”, Roni Carta wrote on his blog.
Hack on Bard
The researcher stated that by deceiving Bard into describing a photo published by a different user, an attacker could effectively obtain unauthorized visual access to any image uploaded by the target.
Malware analysis can be fast and simple. Just let us show you the way to:
- Interact with malware safely
- Set up virtual machine in Linux and all Windows OS versions
- Work in a team
- Get detailed reports with maximum data
If you want to test all these features now with completely free access to the sandbox:
Additionally, considering Bard’s optical character recognition (OCR) skill, this can also result in the unwanted disclosure of confidential textual information—such as emails, notes, and revenue—in the victim’s photographs.
Bard can render the markdown during user conversations.
The researcher’s idea was straightforward:
What if we could get Bard to summarize our files on disk, emails, and other data, then use markdown to extract it? The researcher considered infiltrating through photos.
Content Security Policy (CSP) is designed here to prevent Cross-Site Scripting (XSS) and data injection threats by allowing the backend server to designate which domains a browser should accept as legitimate sources of executable scripts, pictures, styles, and so on.
All in all, anything that causes an origin to send an HTTP request.
Researchers successfully obtained their victims’ email accounts. After quickly alerting Google to this vulnerability, Justin and Roni were rewarded with a $20,000 bounty and an additional $1,337 for the third-coolest bug of the event!
Hacking the Google Cloud Console
Within the framework of the event, researchers also had access to recently released AI features on the Google Cloud Console, which they could attack.
Roni Carta launched his proxy right away and examined every contact that took place between the front end and the back end. GraphQL was one of the API endpoints, and it was operational on cloudconsole-pa.clients6.google.com.
When researchers discovered they were utilizing GraphQL, they right away checked for a Denial of Service (DoS).
Directive overloading happens when a query is intentionally crafted with an excessive number of directives.
This can be done to exploit the server’s processing of each directive, leading to increased computational load.
The backend would take longer to reply to requests when researchers added more directives.
When taking advantage of DoS circumstances that can affect the target’s availability.
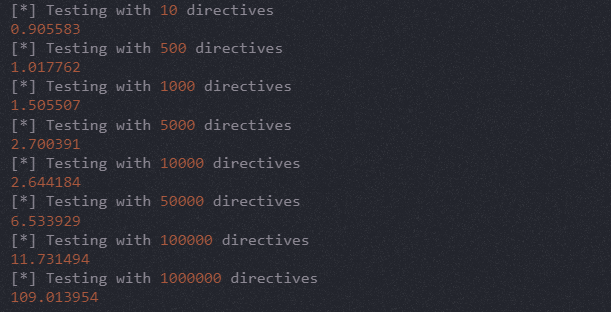
“A malicious actor could easily compute a request with millions of directives and send thousands of requests per minute to hang some part of Google’s Backend,” researchers said.
Researchers were awarded $1,000 by the Bug Bounty Team, with an extra $5,000 for the “Coolest Bug of the Event” incentive.
With AIs being used in their products, Google wants to create an effective Security Red Teaming procedure; for this reason, their Bug Bounty team organized the event.
Worldwide, researchers were challenged by them to look for flaws that they had not discovered.
You can block malware, including Trojans, ransomware, spyware, rootkits, worms, and zero-day exploits, with Perimeter81 malware protection. All are incredibly harmful, can wreak havoc, and damage your network.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter
Read the full article here

