Ivanti Connect Secure vulnerabilities were disclosed in January 2024 as a potential gateway for threat actors to penetrate corporate networks.
The two vulnerabilities, CVE-2023-46805 and CVE-2024-21887 were associated with authentication bypass and arbitrary command execution. Combining these two could result in an unauthenticated remote command execution on affected systems.
However, Ivanti addressed these vulnerabilities in its security advisory. Ever since threat actors have found several attempts of exploitation in the wild.
In addition to the disclosure, a proof of concept for these vulnerabilities was also released by Volexity researchers, providing additional information for threat actors and security researchers to find them more easily.
Live attack simulation Webinar demonstrates various ways in which account takeover can happen and practices to protect your websites and APIs against ATO attacks
.
Exploitation Observed
According to the reports shared by Akami, roughly 250,000 exploitation attempts have been observed daily against Ivanti Connect Secure devices.
This narrows down to 1000+ customers and 10,000+ domains with more than 3,300+ unique IPs involved in this exploitation. These attacks originate from 18 different countries.
These attacks peaked during the first 24 hours of exploit details disclosure. In most of these attacks, threat actors attempt to deliver a payload that sends a beacon request to the attacker-controlled domain to perform a remote command execution.
Exploit Codes:
Researchers have found two principal exploit codes used by threat actors for exploiting these Ivanti Connect Secure devices. These exploit codes were Directory traversal-based Local File Inclusion attacks or OS command injection attacks.
Exploit 1:
/api/v1/totp/user-backup-code/../../system/maintenance/archiving/cloud-server-test-connection
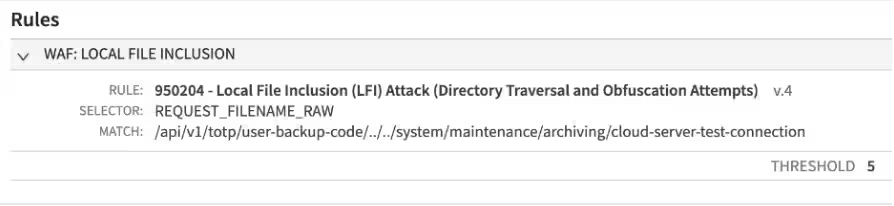
Exploit 2:
/api/v1/totp/user-backup-code/../../license/keys-status/

It is recommended that all the users of Ivanti Connect Secure upgrade to the latest versions to prevent them from getting exploited by threat actors.
You can block malware, including Trojans, ransomware, spyware, rootkits, worms, and zero-day exploits, with Perimeter81 malware protection. All are extremely harmful, can wreak havoc, and damage your network.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.
Read the full article here

