A new malware has been reported to be distributed by threat actors, which is likely known to be a stealthy espionage campaign going on since March 2021. This new malware backdoor has been named “Zardoor.”
This malware is deployed with several advanced techniques that use reverse proxy tools to evade detection and maintain persistence for several years.
Additionally, the threat actor has been using living-off-the-land binaries to deploy the backdoor and establish C2 control over the compromised systems. However, currently, there has been only one compromised target, which is an Islamic non-profit organization affected by this backdoor.
It is speculated that the threat actor could be based out of China due to the use of reverse proxy tools that are predominantly utilized by TTPs of threat groups originating from China.
Prevent malware from infecting your network at the delivery stage by intercepting malicious files in transit from their source to the target device’s web browser.
.
Stealthy Zardoor Malware
The initial access vector of this backdoor is unknown, but the threat actor uses open-source reverse proxy tools like Fast Reverse Proxy (FRP), sSocks, and Venom, which are typically used by penetration testers.
Once the threat actor establishes connectivity with the compromised system, the threat actor uses Windows Management Instrumentation to move laterally and spread the backdoor alongside other attacker tools.
Execution of Zardoor Backdoor
This backdoor is specifically designed to maintain persistent access over the compromised system. which uses several DLL files like “zar32.dll” and “zor32.dll”. “Zar32.dll” is found to be the main backdoor component that communicates with the C2 server, whereas “zor32.dll” ensures that zar32.dll has been deployed with proper admin privileges.
The original dropper of this backdoor is still not found, but based on the samples collected, the dropper’s main purpose is to configure “msdtc.exe” for loading the “oci.dll” malicious payload.
For executing the “zar32.dll”, the ServiceMain() is executed by the msdtc.exe, which loader this malicious DLL using the command rundll32.exe C:WINDOWSsystem32zar32.dll MainEntry. While this is operating, the “Zor32.dll” is also loaded from the same exported method with the command rundll32.exe C:WINDOWSsystem32zor32.dll MainEntry.
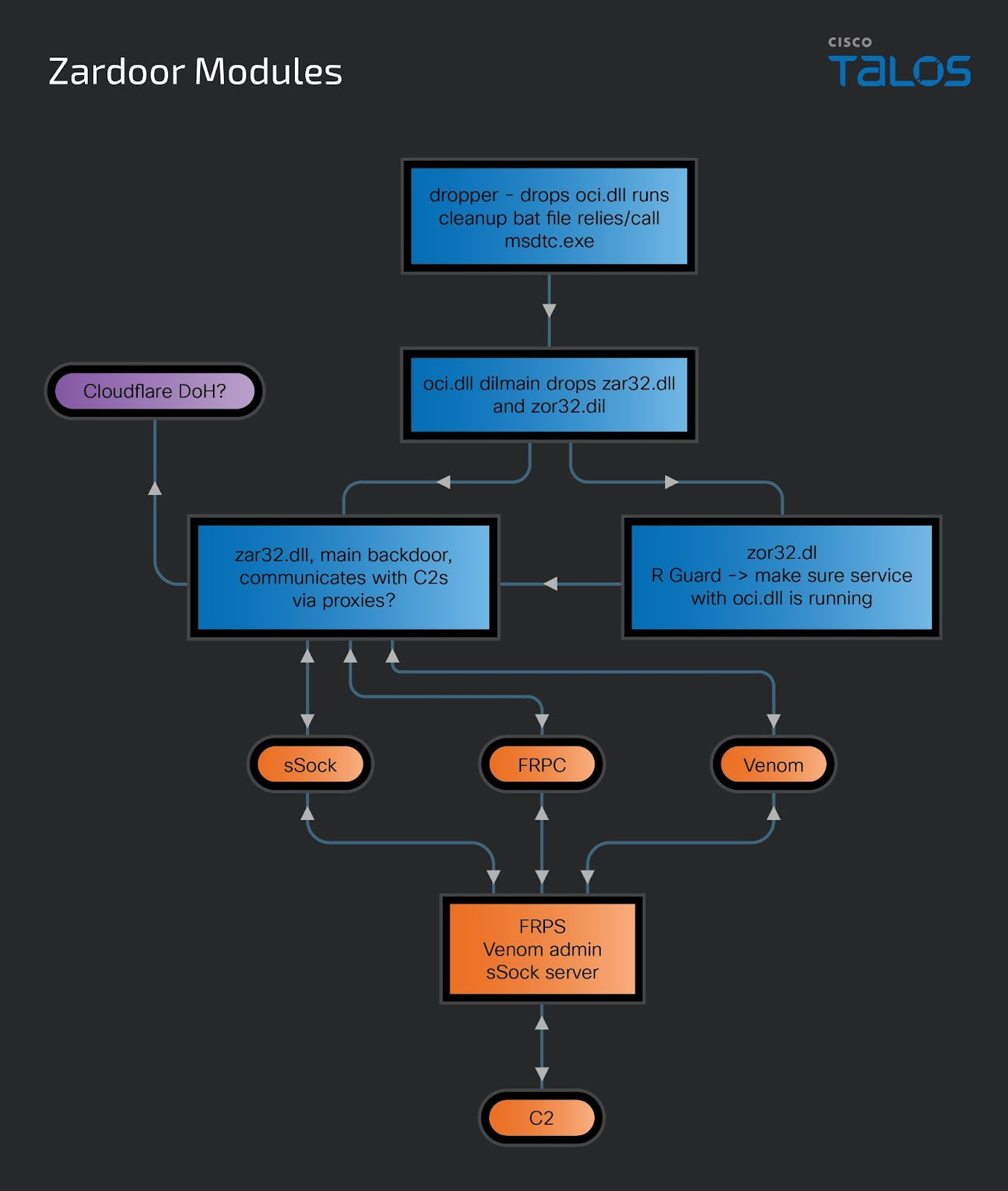
When the connection is fully established, “zar32.dll” is capable of the following C2 commands:
- Encrypt and send data to C2.
- Execute remotely fetched PE payload.
- Search for session ID.
- (Plugin exit).
- Remote shellcode execution.
- Delete this RAT.
- Update C2 IP (IP/domain_name:port).
- Do nothing.
Talos provides detailed information about the source code, techniques involved, DLL behavior, and other information.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.
Read the full article here

